BadB
Professional
- Messages
- 2,459
- Reaction score
- 2,450
- Points
- 113
Google Dorking is a computer hacking technique that uses Google Search and other Google apps. This is done very simply, through holes in search queries. This method is also known as Google Hacking.
How does Dork work?
Standard situation: you recently purchased a security camera that allows you to view, for example, your backyard from anywhere on your phone. By downloading the app, you log in, voila, now everything is in your phone.
However, a person with information and knowledge can only use Google to get a picture from a video surveillance camera in real time. How does it work?
Unfortunately, Google is not very effective in protecting devices on the world wide web, especially those running on HTTP and HTTPS servers. For this reason, the search engine gets everything that doesn't need to be there.
Vulnerability and disclosure
By far, the most frequent type of disclosed file that we can find through a search engine, if desired, is data from user accounts. The development of events is as follows: the server or other service is configured incorrectly, exposing its administrative logs to the Internet by mistake. If passwords are changed or the user is unable to log in correctly, these logs leak to the network.
But you can use Google dorks not only to search for data from accounts, but also to intercept information from servers that may contain interesting information, email lists, and open Webcams. Yes, Yes, like in the Snowden movie.
Course of action
You will need a browser with Internet access. A great feature of using Google dorks is that the necessary tools for implementation are available to almost everyone.
Step 1: Search for FTP servers and websites using HTTP
To get started, we'll use the following dork to search for servers that transmit any information. A search for these servers may allow you to find files that should be internal, but were mistakenly made public.
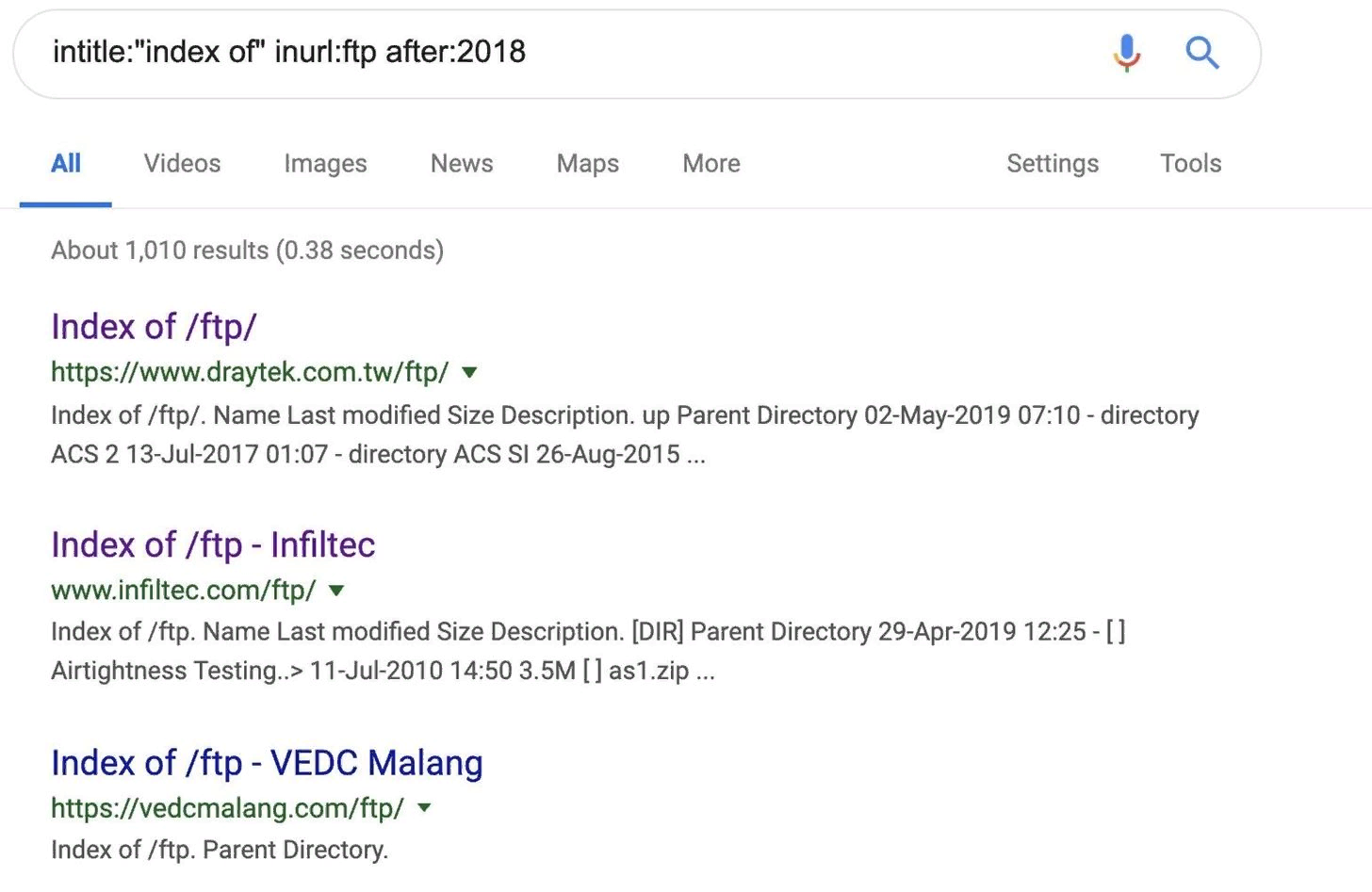
These servers are made publicly available because the index file of their FTP server is data that Google often scans. Scanning leads to data leakage from the server to the open source of the search engine.
If we want to find insecure web pages that still use HTTP for search, we need to slightly change the command from " ftp "to" http", then re-run the search.
A search for this string should result in a list of sites that use HTTP and are ready for attack. But if we are looking for a specific type of site, then we can go even further.
If we want to start attacking a few simple targets, then we change the text in the search title.
We can continue to add search commands such as AND inurl:"registration" to get more specific information and search for registration pages of unsecured websites.
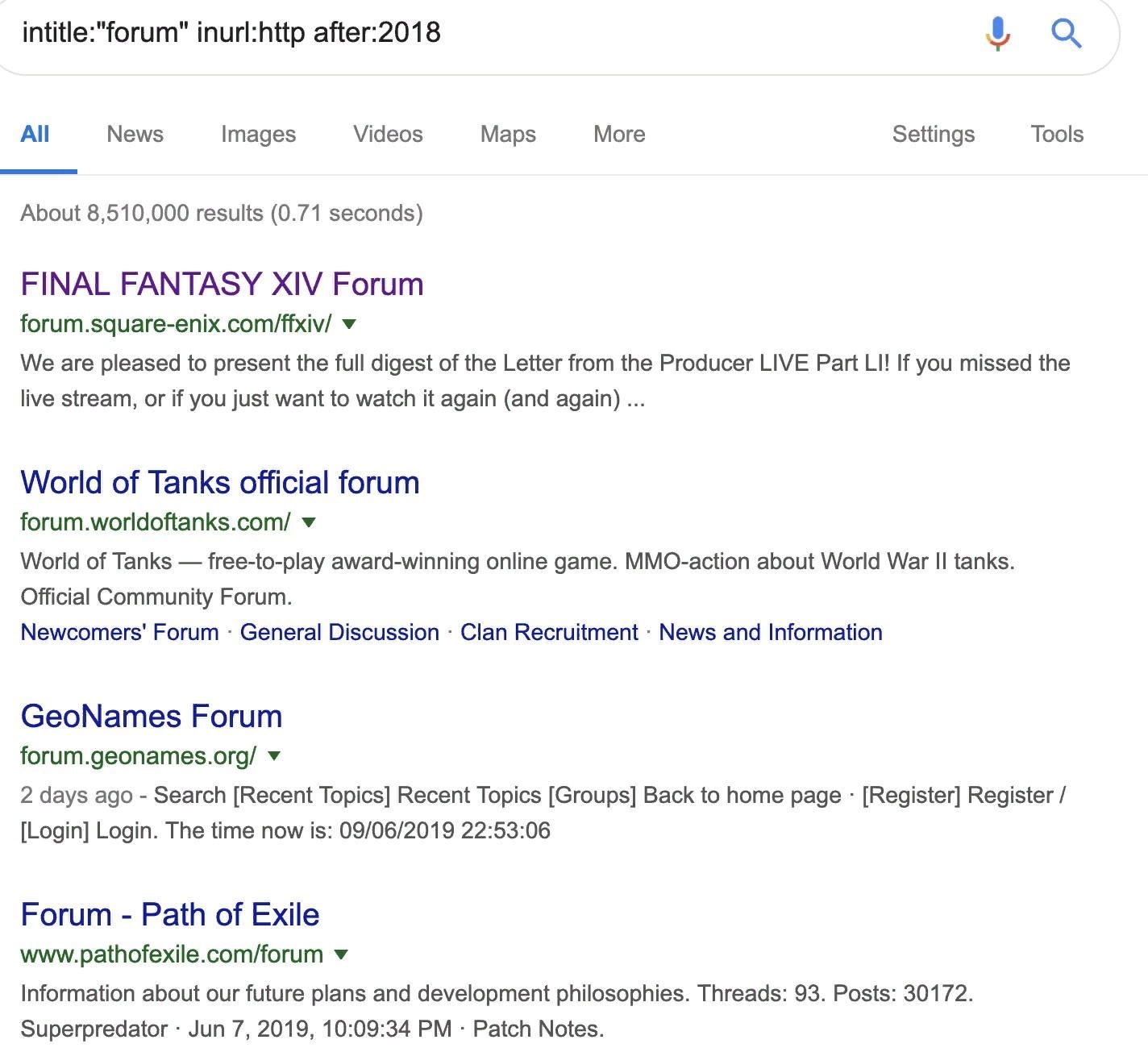
Vulnerable forums
Here you can see a list of vulnerable online forums that use HTTP.
Now let's move on to more detailed actions.
Step 2: Find the log files with passwords
The next step is to search for .LOG files. Searching for LOG files will allow us to find out what credentials the system or different user accounts, as well as administrators, may have.
The dork that we will use for this is as follows.
When we search for current files in the logs available on the Internet, we find almost immediately such information:
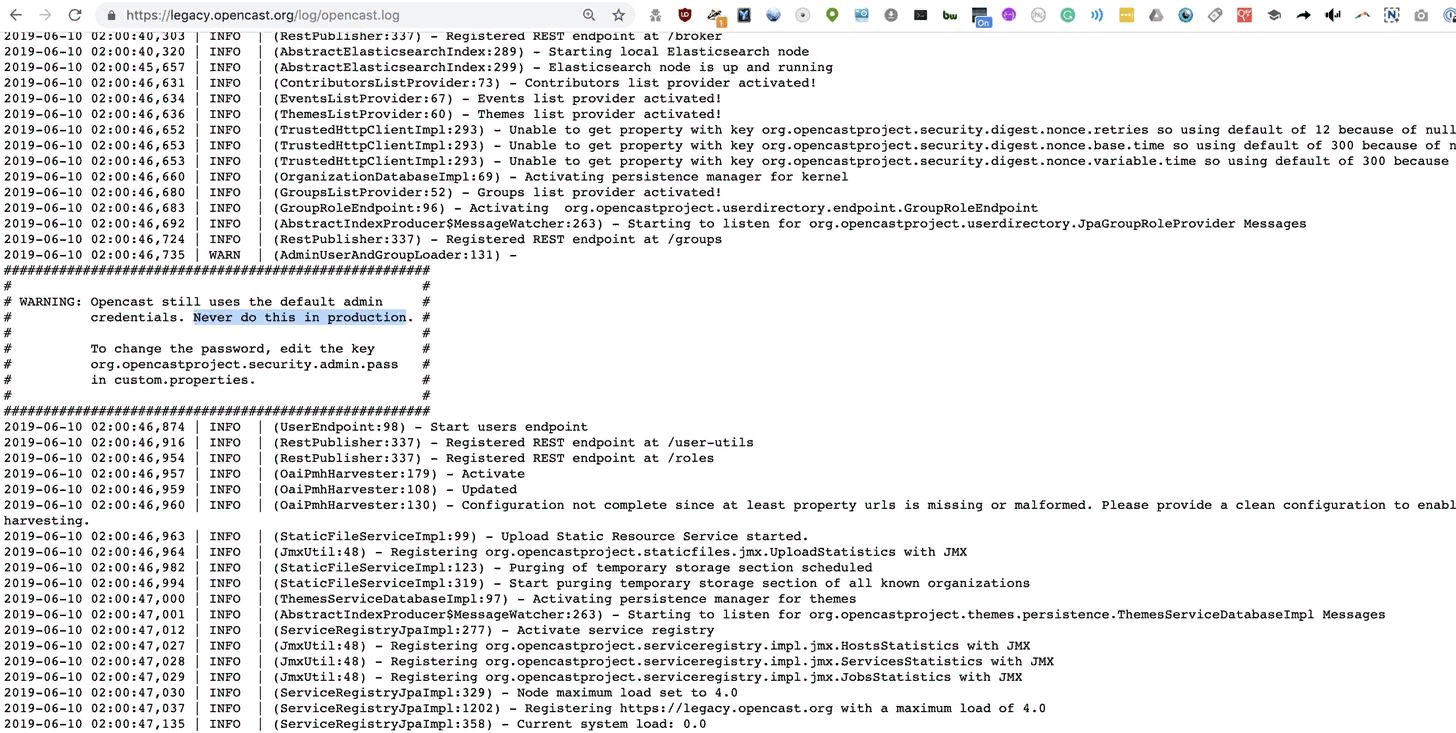
If we delete after: 2018, we will see old log files that also provide services to the Internet.
Step 3: Find email lists
Email lists are a great way to find information about companies or schools. Emails are often formed to organize customers, employees, and students into one single group.
Let's do the search. We will need the file type .XLS, namely tables with the string "email.xls" in the URL.
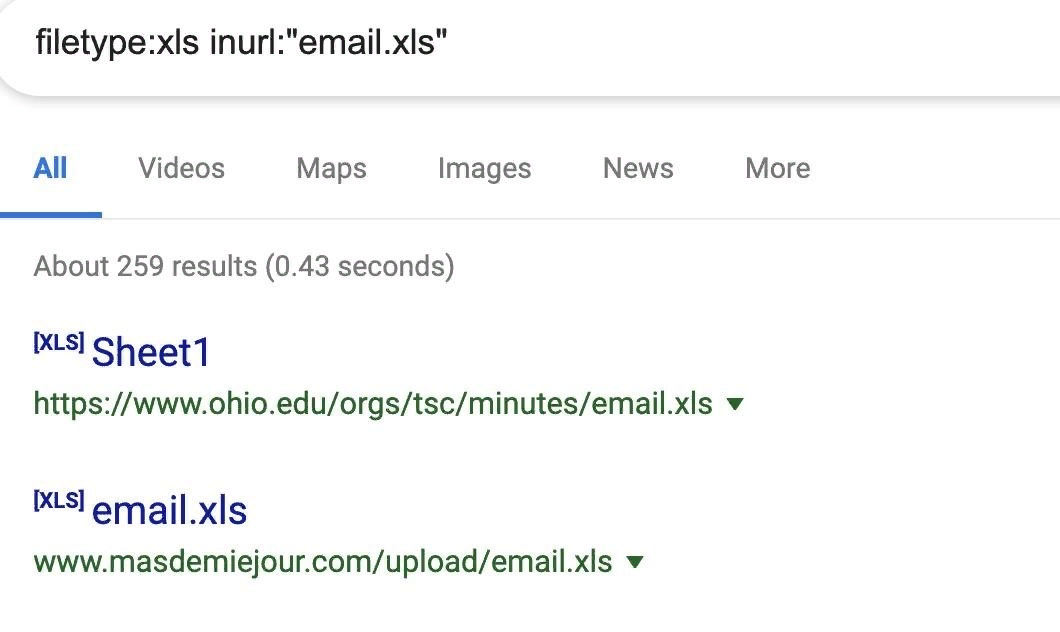
It seems to be a good result, but I advise you to pay attention to the fact that some people deliberately leave malware in the hole. By downloading a conditional table with email addresses, you can easily catch a Stiller.
Step 4: Find the open cameras
Logging in from the camera and viewing pages is usually done via the HTTP Protocol. This means that Google will happily index them and provide them for viewing, as long as you know the correct search string.
One of the most common web camera string formats is search "top.htm" in the URL with the current time and date. So you will find a lot of results.
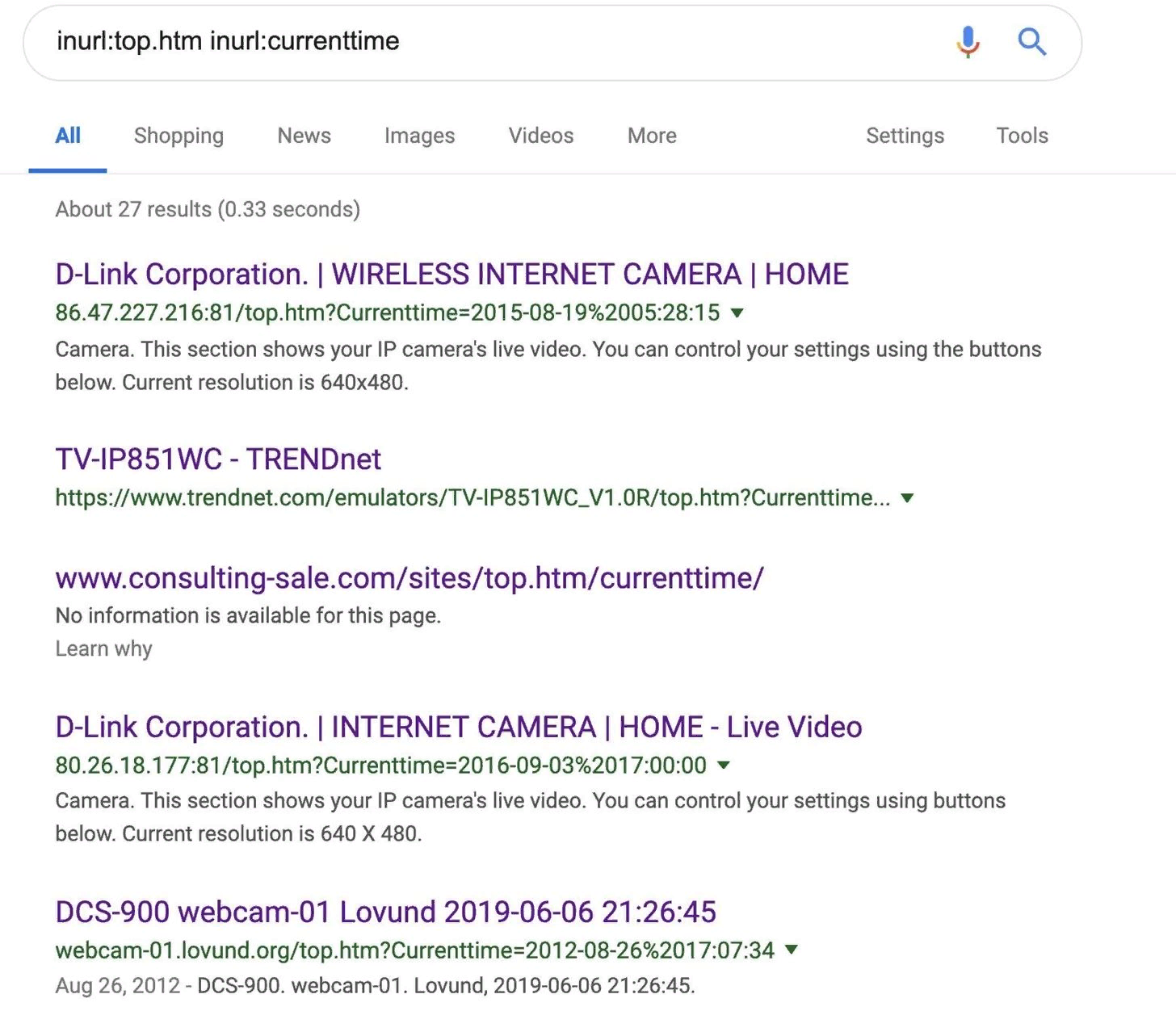
The first result is a webcam that looks like the Windows XP background from a different angle in Ireland.

Another dork for cameras that Google will give us:
With it, I was able to find the best camera of all, birdcam1.
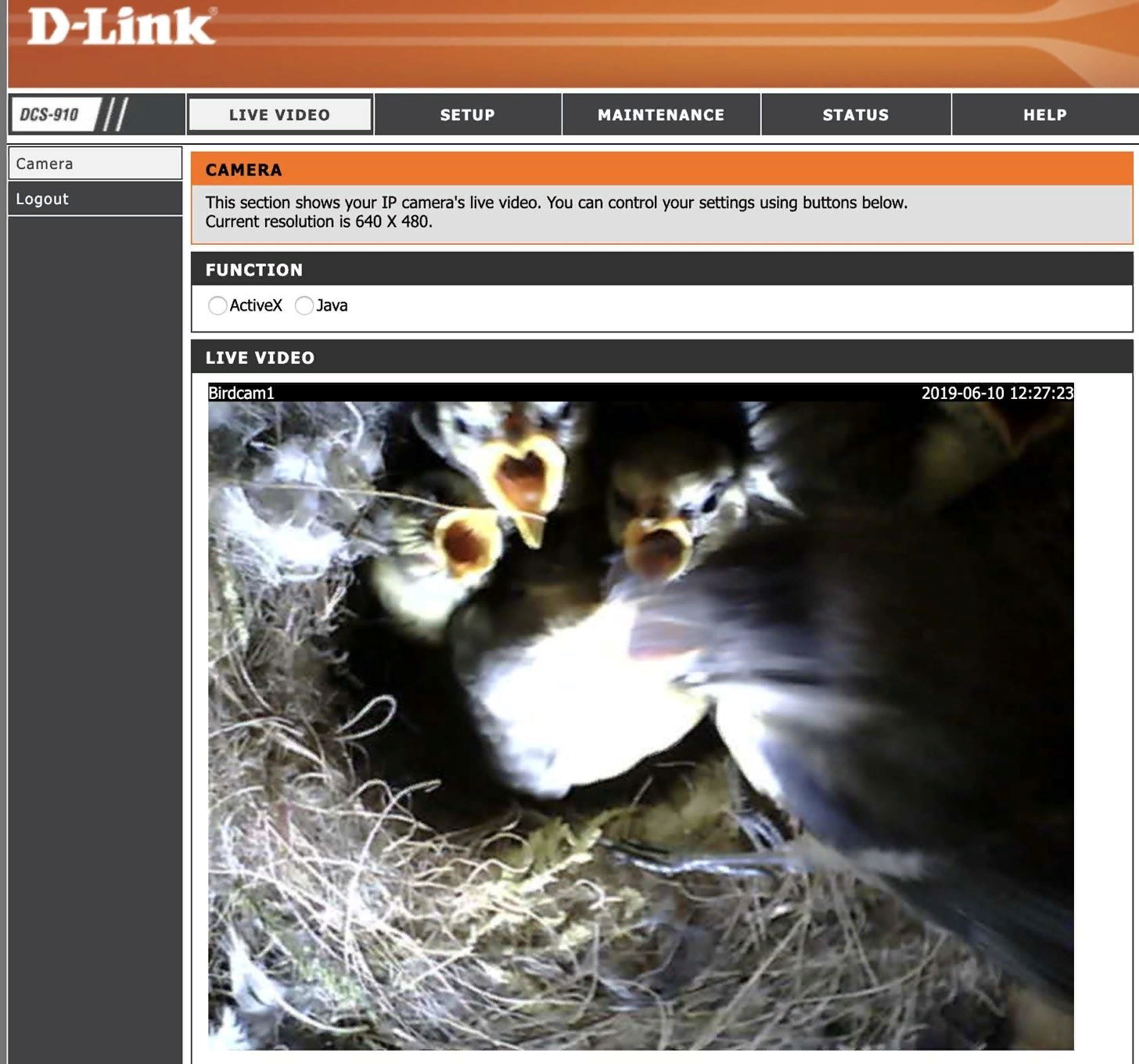
Please don't hack the bird camera, it's a bit creaky.
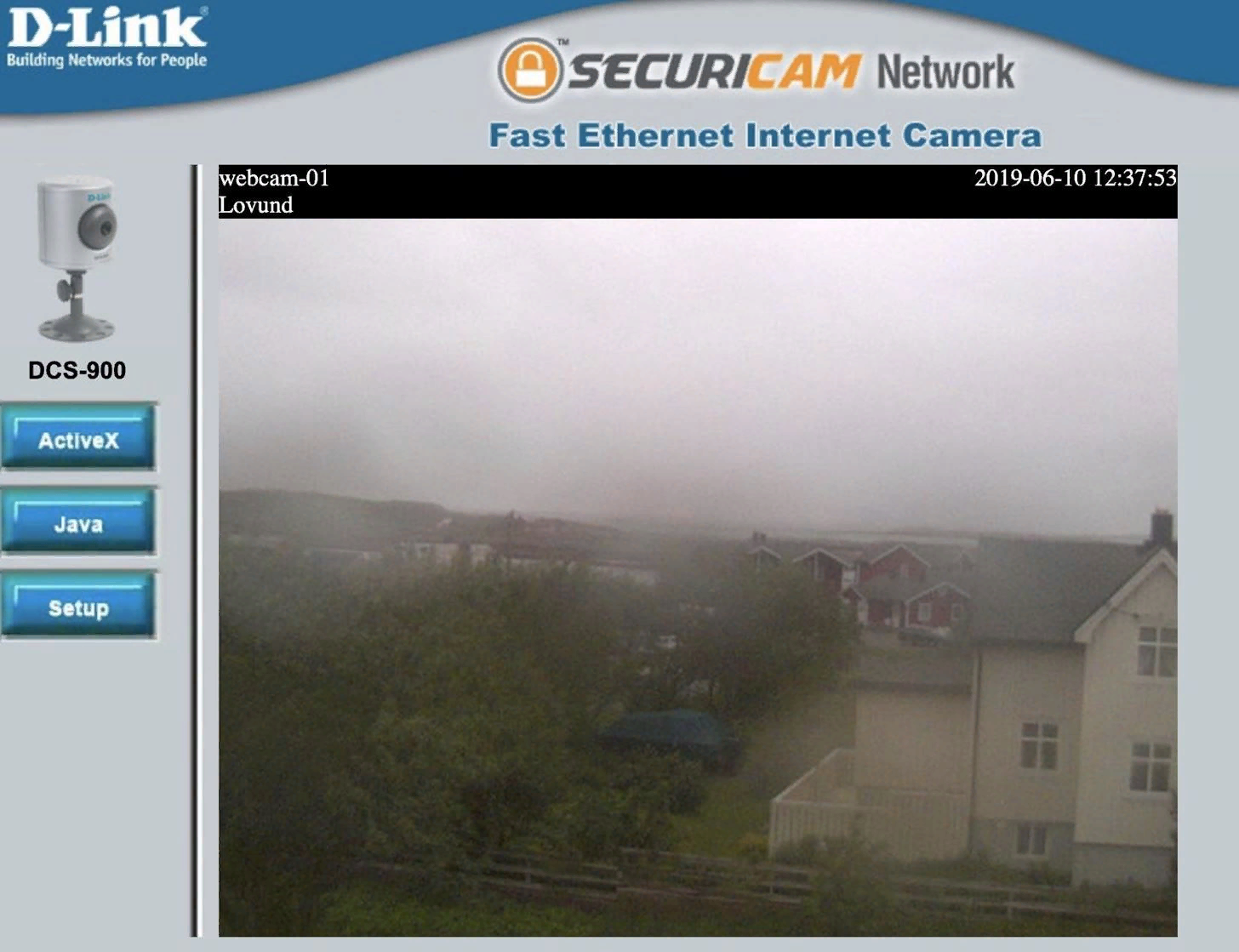
Many cameras are also regulated inside factories or industrial areas.
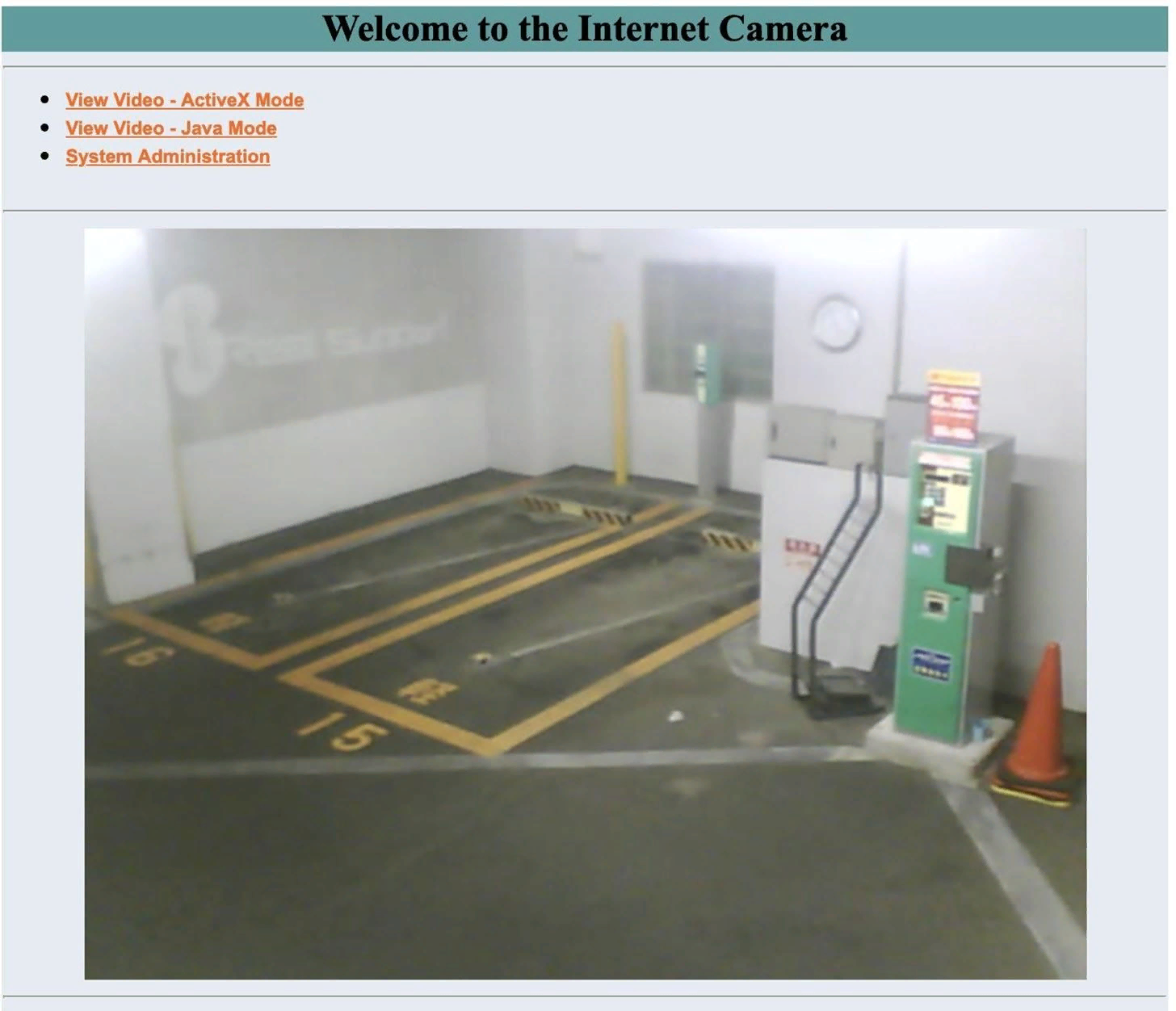
What is shown above is cameras without a password. but many dorks search for pages with a pass, but this is not a problem, because most people use primitive sets of numbers or letters by default.
How does Dork work?
Standard situation: you recently purchased a security camera that allows you to view, for example, your backyard from anywhere on your phone. By downloading the app, you log in, voila, now everything is in your phone.
However, a person with information and knowledge can only use Google to get a picture from a video surveillance camera in real time. How does it work?
Unfortunately, Google is not very effective in protecting devices on the world wide web, especially those running on HTTP and HTTPS servers. For this reason, the search engine gets everything that doesn't need to be there.
Vulnerability and disclosure
By far, the most frequent type of disclosed file that we can find through a search engine, if desired, is data from user accounts. The development of events is as follows: the server or other service is configured incorrectly, exposing its administrative logs to the Internet by mistake. If passwords are changed or the user is unable to log in correctly, these logs leak to the network.
But you can use Google dorks not only to search for data from accounts, but also to intercept information from servers that may contain interesting information, email lists, and open Webcams. Yes, Yes, like in the Snowden movie.
Course of action
You will need a browser with Internet access. A great feature of using Google dorks is that the necessary tools for implementation are available to almost everyone.
Step 1: Search for FTP servers and websites using HTTP
To get started, we'll use the following dork to search for servers that transmit any information. A search for these servers may allow you to find files that should be internal, but were mistakenly made public.
Code:
intitle:"index of" inurl:ftp after:2018
These servers are made publicly available because the index file of their FTP server is data that Google often scans. Scanning leads to data leakage from the server to the open source of the search engine.
If we want to find insecure web pages that still use HTTP for search, we need to slightly change the command from " ftp "to" http", then re-run the search.
Code:
intitle:"index of" inurl:http after:2018A search for this string should result in a list of sites that use HTTP and are ready for attack. But if we are looking for a specific type of site, then we can go even further.
If we want to start attacking a few simple targets, then we change the text in the search title.
Code:
intitle:"forum" inurl:http after:2018We can continue to add search commands such as AND inurl:"registration" to get more specific information and search for registration pages of unsecured websites.

Vulnerable forums
Here you can see a list of vulnerable online forums that use HTTP.
Now let's move on to more detailed actions.
Step 2: Find the log files with passwords
The next step is to search for .LOG files. Searching for LOG files will allow us to find out what credentials the system or different user accounts, as well as administrators, may have.
The dork that we will use for this is as follows.
Code:
allintext:password filetype:log after:2018When we search for current files in the logs available on the Internet, we find almost immediately such information:

If we delete after: 2018, we will see old log files that also provide services to the Internet.
Step 3: Find email lists
Email lists are a great way to find information about companies or schools. Emails are often formed to organize customers, employees, and students into one single group.
Let's do the search. We will need the file type .XLS, namely tables with the string "email.xls" in the URL.

It seems to be a good result, but I advise you to pay attention to the fact that some people deliberately leave malware in the hole. By downloading a conditional table with email addresses, you can easily catch a Stiller.
Step 4: Find the open cameras
Logging in from the camera and viewing pages is usually done via the HTTP Protocol. This means that Google will happily index them and provide them for viewing, as long as you know the correct search string.
One of the most common web camera string formats is search "top.htm" in the URL with the current time and date. So you will find a lot of results.
Code:
inurl:top.htm inurl:currenttime
The first result is a webcam that looks like the Windows XP background from a different angle in Ireland.

Another dork for cameras that Google will give us:
Code:
inurl:"lvappl.htm"With it, I was able to find the best camera of all, birdcam1.

Please don't hack the bird camera, it's a bit creaky.

Many cameras are also regulated inside factories or industrial areas.

What is shown above is cameras without a password. but many dorks search for pages with a pass, but this is not a problem, because most people use primitive sets of numbers or letters by default.

