Even changing your password won't help you avoid losing your account.
At the end of December 2023, we wrote about the abuse of the undocumented Google Chrome API by malicious software. It is noted that two data theft operations, Lumma and Rhadamanthys, use the API to restore expired Google credentials stolen during attacks.
After this report, four other ransomware programs-Stealc, Medusa, RisePro, and Whitesnake-also began using a similar technique. CloudSEK security specialists have revealed that malware uses the Google OAuth "MultiLogin" API to create new working authentication cookies when the original stolen Google cookies of the victim expire.
The specified API is intended for syncing accounts from different Google services. Malware steals not only authentication cookies for Google sites, but also a special token that can be used to update or create new authentication tokens. Experts were not able to learn more about this API from Google, and the only documentation can be found in the source code of Google Chrome.
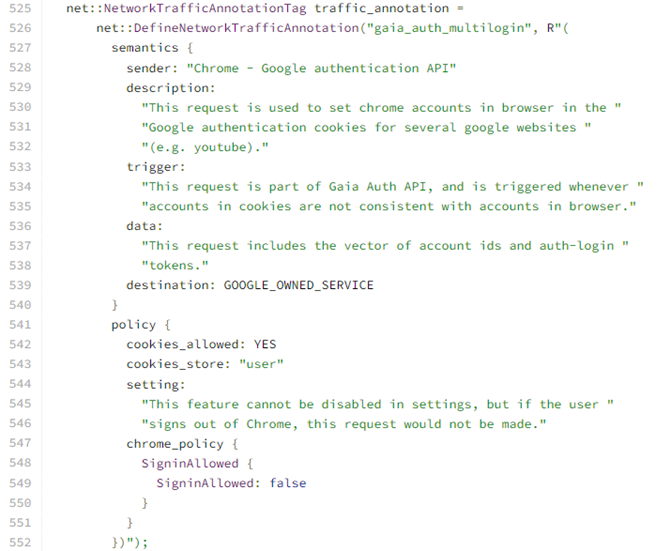
Information about MultiLogin in the source code
Google in its statement confirmed its awareness of the situation, but treats the problem as a normal cookie theft through malware. The company claims that it regularly updates its security mechanisms and helps users affected by malware.
Google recommends that users log out of their Chrome account on affected devices and cancel all active sessions via the My Devices menu, which will make the Refresh token invalid for use with the API. In addition, Google advises you to change your password, especially if it was used on other sites.
However, many affected users do not know when or how to take the suggested measures. Often, they only find out about the infection after their accounts have been hacked and used improperly. An example is the case of an employee of Orange Spain, when the infection became known only after using stolen credentials to log in to the company's account and changing its BGP configuration, which led to failures in Internet services.
At the moment, Google notifies victims of API abuse, but the question remains how future victims will be notified and how they will know if they need to log out of the browser to revoke authentication tokens.
Many experts believe that the best solution would be to restrict access to the mentioned API in order to prevent its exploitation. However, at the moment there is no information that Google plans to take such steps. Google did not respond to questions about its plans to combat API abuse.
At the end of December 2023, we wrote about the abuse of the undocumented Google Chrome API by malicious software. It is noted that two data theft operations, Lumma and Rhadamanthys, use the API to restore expired Google credentials stolen during attacks.
After this report, four other ransomware programs-Stealc, Medusa, RisePro, and Whitesnake-also began using a similar technique. CloudSEK security specialists have revealed that malware uses the Google OAuth "MultiLogin" API to create new working authentication cookies when the original stolen Google cookies of the victim expire.
The specified API is intended for syncing accounts from different Google services. Malware steals not only authentication cookies for Google sites, but also a special token that can be used to update or create new authentication tokens. Experts were not able to learn more about this API from Google, and the only documentation can be found in the source code of Google Chrome.

Information about MultiLogin in the source code
Google in its statement confirmed its awareness of the situation, but treats the problem as a normal cookie theft through malware. The company claims that it regularly updates its security mechanisms and helps users affected by malware.
Google recommends that users log out of their Chrome account on affected devices and cancel all active sessions via the My Devices menu, which will make the Refresh token invalid for use with the API. In addition, Google advises you to change your password, especially if it was used on other sites.
However, many affected users do not know when or how to take the suggested measures. Often, they only find out about the infection after their accounts have been hacked and used improperly. An example is the case of an employee of Orange Spain, when the infection became known only after using stolen credentials to log in to the company's account and changing its BGP configuration, which led to failures in Internet services.
At the moment, Google notifies victims of API abuse, but the question remains how future victims will be notified and how they will know if they need to log out of the browser to revoke authentication tokens.
Many experts believe that the best solution would be to restrict access to the mentioned API in order to prevent its exploitation. However, at the moment there is no information that Google plans to take such steps. Google did not respond to questions about its plans to combat API abuse.
