Man
Professional
- Messages
- 3,222
- Reaction score
- 1,199
- Points
- 113
A false sense of security opens the door to new attacks.
Cybersecurity experts have reported a surge in phishing pages created with the Webflow website builder. According to Netskope, from April to September 2024, traffic to Webflow phishing pages increased tenfold. The attacks covered more than 120 organizations, mainly in North America and Asia, including the financial, banking and technology sectors.
Criminals create separate phishing pages on Webflow or redirect users to other malicious sites. This approach allows for flexibility: creating fake pages does not require complex code, and the ability to redirect allows for more sophisticated attacks.
Webflow turned out to be more attractive than Cloudflare R2 and Microsoft Sway due to the ability to create custom subdomains at no additional cost. Unlike random alphanumeric subdomains, these addresses are less suspicious to users.
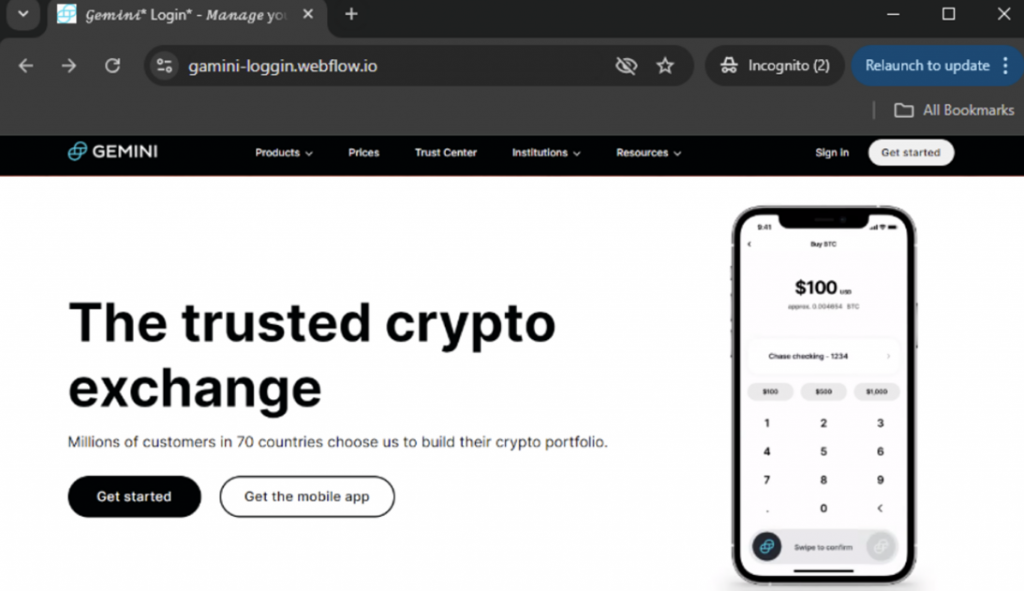
Phishing pages mimic the login pages of crypto wallets such as Coinbase and MetaMask, as well as corporate platforms including Microsoft 365. The entered data is sent to third-party servers, which allows attackers to take possession of seed phrases and empty victims' accounts.
Netskope has also identified sites on Webflow that use screenshots of the main pages of legitimate crypto wallets as fake pages. When clicking on page elements, the user is redirected to a fraudulent resource.
In some cases, victims are shown an error message indicating "unauthorized activity" and prompting them to contact support via a chat service. Similar methods have previously been used in the campaigns of the CryptoCore scammers.
To prevent phishing attacks related to *.webflow[.]io, it is recommended to check the URL before entering data and avoid clicking on links from search engines and third-party resources.
It's important for organizations to review their security policies: configure URL filtering to block known malicious sites, inspect all web traffic with NG-SWG, and use threat-based and machine learning protection to identify new threats.
It is also worth implementing Remote Browser Isolation (RBI) technology to safely visit suspicious domains to minimize risks when working with new or newly registered sites.
Source
Cybersecurity experts have reported a surge in phishing pages created with the Webflow website builder. According to Netskope, from April to September 2024, traffic to Webflow phishing pages increased tenfold. The attacks covered more than 120 organizations, mainly in North America and Asia, including the financial, banking and technology sectors.
Criminals create separate phishing pages on Webflow or redirect users to other malicious sites. This approach allows for flexibility: creating fake pages does not require complex code, and the ability to redirect allows for more sophisticated attacks.
Webflow turned out to be more attractive than Cloudflare R2 and Microsoft Sway due to the ability to create custom subdomains at no additional cost. Unlike random alphanumeric subdomains, these addresses are less suspicious to users.

Phishing pages mimic the login pages of crypto wallets such as Coinbase and MetaMask, as well as corporate platforms including Microsoft 365. The entered data is sent to third-party servers, which allows attackers to take possession of seed phrases and empty victims' accounts.
Netskope has also identified sites on Webflow that use screenshots of the main pages of legitimate crypto wallets as fake pages. When clicking on page elements, the user is redirected to a fraudulent resource.
In some cases, victims are shown an error message indicating "unauthorized activity" and prompting them to contact support via a chat service. Similar methods have previously been used in the campaigns of the CryptoCore scammers.
To prevent phishing attacks related to *.webflow[.]io, it is recommended to check the URL before entering data and avoid clicking on links from search engines and third-party resources.
It's important for organizations to review their security policies: configure URL filtering to block known malicious sites, inspect all web traffic with NG-SWG, and use threat-based and machine learning protection to identify new threats.
It is also worth implementing Remote Browser Isolation (RBI) technology to safely visit suspicious domains to minimize risks when working with new or newly registered sites.
Source

