Lord777
Professional
- Messages
- 2,577
- Reaction score
- 1,553
- Points
- 113
BitSight detected an army of proxies that were victims of large-scale infections.
BitSight specialists have discovered a new large botnet network called Socks5Systemz, which has already managed to infect about 10,000 devices using malicious uploaders PrivateLoader and Amadey. The infections come amid a growing number of cyberattacks that use compromised computers to redirect malicious, illegal, or anonymous traffic through proxy servers.
The BitSight report details the activities of the Socks5Systemz botnet, which, although launched in 2016, remained little known until recently. Malware is distributed through various channels, including phishing, exploit kits, malicious advertising, and downloading Trojans from P2P networks. The task of the detected malware samples is to inject the proxy bot into the host memory and ensure its persistence in the system through the Windows ContentDWSvc service.
The proxy bot is a 32-bit DLL library with a size of 300 KB. The domain generation algorithm (DGA) is used to communicate with the Command and Control server (C2). In response, the server can send one of the following commands: wait, connect to or disconnect from the server, update the list of allowed IP addresses, and so on.
Connecting to the attackers infrastructure makes the infected device available for use as a proxy server, which is then sold to other cybercriminals. Socks5Systemz proxy servers are sold on a subscription basis, with prices ranging from $1 to $140 per day, and payment is accepted in cryptocurrency through the anonymous Cryptomus payment gateway. Standard subscribers are limited to a single thread and proxy type, while VIP users can use 100-5000 threads and set the proxy server type to SOCKS4, SOCKS5, or HTTP.
At least 53 Socks5Systemz-related servers were identified – all located in Europe and distributed across France, Bulgaria, the Netherlands, and Sweden. Of the 10,000 victims, the top ten most affected countries are India, Brazil, Colombia, South Africa, Bangladesh, Argentina, Angola, the United States, Suriname and Nigeria.
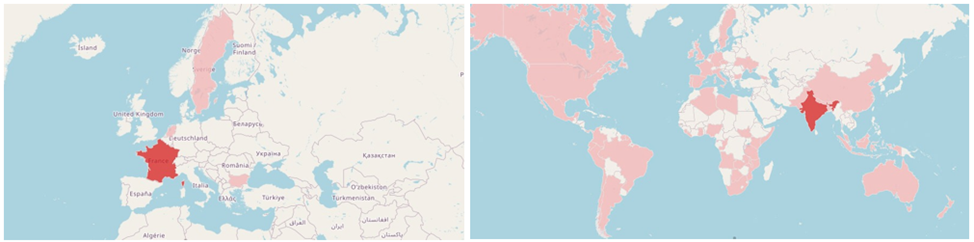
Geographical distribution of infrastructure (left) and victims (right).
Resident proxy servers have become a lucrative business that has a serious impact on Internet security and unauthorized use of network bandwidth. Such services are usually used for trading bots and circumventing geographical restrictions, which makes them very popular.
BitSight specialists have discovered a new large botnet network called Socks5Systemz, which has already managed to infect about 10,000 devices using malicious uploaders PrivateLoader and Amadey. The infections come amid a growing number of cyberattacks that use compromised computers to redirect malicious, illegal, or anonymous traffic through proxy servers.
The BitSight report details the activities of the Socks5Systemz botnet, which, although launched in 2016, remained little known until recently. Malware is distributed through various channels, including phishing, exploit kits, malicious advertising, and downloading Trojans from P2P networks. The task of the detected malware samples is to inject the proxy bot into the host memory and ensure its persistence in the system through the Windows ContentDWSvc service.
The proxy bot is a 32-bit DLL library with a size of 300 KB. The domain generation algorithm (DGA) is used to communicate with the Command and Control server (C2). In response, the server can send one of the following commands: wait, connect to or disconnect from the server, update the list of allowed IP addresses, and so on.
Connecting to the attackers infrastructure makes the infected device available for use as a proxy server, which is then sold to other cybercriminals. Socks5Systemz proxy servers are sold on a subscription basis, with prices ranging from $1 to $140 per day, and payment is accepted in cryptocurrency through the anonymous Cryptomus payment gateway. Standard subscribers are limited to a single thread and proxy type, while VIP users can use 100-5000 threads and set the proxy server type to SOCKS4, SOCKS5, or HTTP.
At least 53 Socks5Systemz-related servers were identified – all located in Europe and distributed across France, Bulgaria, the Netherlands, and Sweden. Of the 10,000 victims, the top ten most affected countries are India, Brazil, Colombia, South Africa, Bangladesh, Argentina, Angola, the United States, Suriname and Nigeria.

Geographical distribution of infrastructure (left) and victims (right).
Resident proxy servers have become a lucrative business that has a serious impact on Internet security and unauthorized use of network bandwidth. Such services are usually used for trading bots and circumventing geographical restrictions, which makes them very popular.

