Friend
Professional
- Messages
- 2,675
- Reaction score
- 1,053
- Points
- 113
Open source is becoming a powerful weapon in the hands of skilled strategists.
At the end of May, specialists from the Natto Team investigated the reconnaissance methods and tools of the APT41 hacker group associated with Chinese threats. Continuing their investigation, experts published a fresh report that reported on several more Chinese groups using similar methods and tools.
In the past ten years, at least three Chinese hacking groups, such as APT10, GALLIUM, and Stately Taurus, have used NBTscan or a modified version of it. Designed to search for information about systems on a network, this tool allows you to scan IP addresses and get data about users, computer names, and MAC addresses.
APT10, which is affiliated with China's Ministry of State Security, used NBTscan in Cloud Hopper and Soft Cell operations to search for services of interest on network devices. The GALLIUM group, according to Microsoft, used this tool to attack global telecom providers in 2019. And the famous Mustang Panda, operating in Southeast Asia, also used NBTscan to scan and examine victims' networks.
The APT40 group, active since 2009, uses a malicious tool called ScanBox that allows it to collect data from infected systems without the need to install software. This framework, written in JavaScript, collects information about the user's system, including the operating system, browsers, antiviruses, and other programs. ScanBox can also log keystrokes, making it a dangerous tool for stealing passwords and other sensitive information.
In May 2024, researchers from Palo Alto Networks reported on the Diplomatic Specter campaign, aimed at government entities in the Middle East, Africa and Asia. As part of this campaign, the Chinese group TGR-STA-0043 used LadonGo and Yasso tools. Yasso is a new suite of tools introduced in 2022 that includes features for SQL penetration, scanning, and command execution. The developer of Yasso is a Chinese security specialist known online under the pseudonym SaiRson.
In addition to well-known tools, Chinese hackers actively use various open source solutions. For example, the Earth Krahang group often uses tools such as sqlmap and nuclei to find vulnerabilities in servers. Some of these tools were developed by Chinese developers.
A complete list of hacking tools that are actively used by various Chinese cyber groups can be found in the image below:
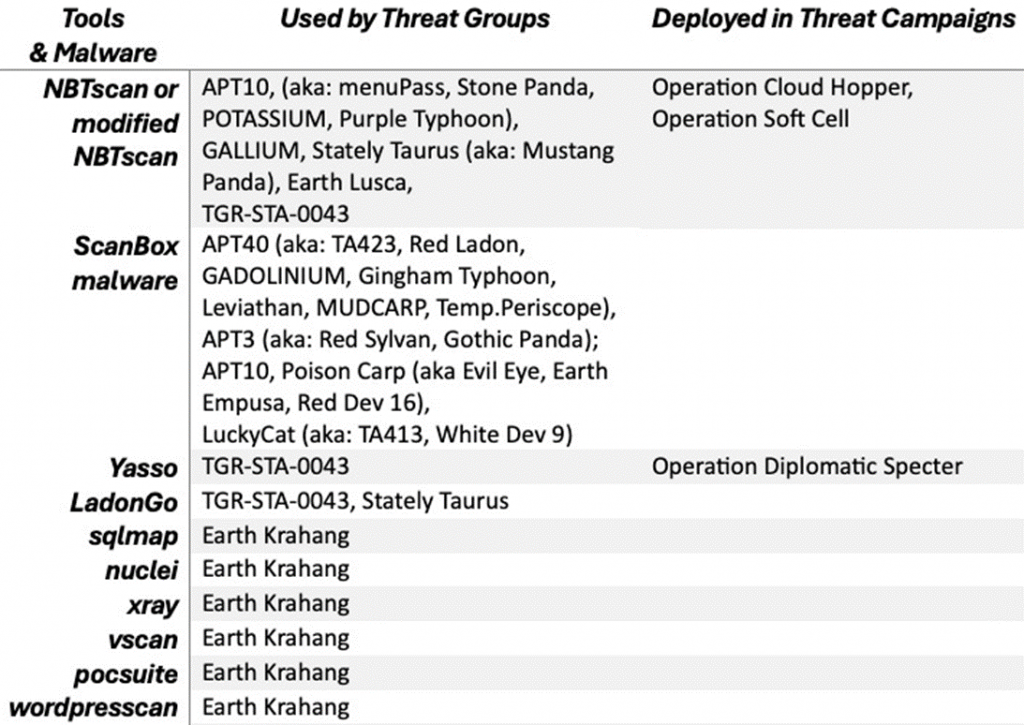
The researchers note that the use of scanning tools, both known and open, remains one of the key strategies of Chinese hackers to find vulnerabilities and further attacks. This points to the need for a comprehensive approach to the protection of information systems, including not only technical measures, but also international cooperation in the field of cybersecurity.
The situation also highlights the importance of constant education and vigilance against new methods of cyber attacks for all participants in the digital space.
Source
At the end of May, specialists from the Natto Team investigated the reconnaissance methods and tools of the APT41 hacker group associated with Chinese threats. Continuing their investigation, experts published a fresh report that reported on several more Chinese groups using similar methods and tools.
In the past ten years, at least three Chinese hacking groups, such as APT10, GALLIUM, and Stately Taurus, have used NBTscan or a modified version of it. Designed to search for information about systems on a network, this tool allows you to scan IP addresses and get data about users, computer names, and MAC addresses.
APT10, which is affiliated with China's Ministry of State Security, used NBTscan in Cloud Hopper and Soft Cell operations to search for services of interest on network devices. The GALLIUM group, according to Microsoft, used this tool to attack global telecom providers in 2019. And the famous Mustang Panda, operating in Southeast Asia, also used NBTscan to scan and examine victims' networks.
The APT40 group, active since 2009, uses a malicious tool called ScanBox that allows it to collect data from infected systems without the need to install software. This framework, written in JavaScript, collects information about the user's system, including the operating system, browsers, antiviruses, and other programs. ScanBox can also log keystrokes, making it a dangerous tool for stealing passwords and other sensitive information.
In May 2024, researchers from Palo Alto Networks reported on the Diplomatic Specter campaign, aimed at government entities in the Middle East, Africa and Asia. As part of this campaign, the Chinese group TGR-STA-0043 used LadonGo and Yasso tools. Yasso is a new suite of tools introduced in 2022 that includes features for SQL penetration, scanning, and command execution. The developer of Yasso is a Chinese security specialist known online under the pseudonym SaiRson.
In addition to well-known tools, Chinese hackers actively use various open source solutions. For example, the Earth Krahang group often uses tools such as sqlmap and nuclei to find vulnerabilities in servers. Some of these tools were developed by Chinese developers.
A complete list of hacking tools that are actively used by various Chinese cyber groups can be found in the image below:

The researchers note that the use of scanning tools, both known and open, remains one of the key strategies of Chinese hackers to find vulnerabilities and further attacks. This points to the need for a comprehensive approach to the protection of information systems, including not only technical measures, but also international cooperation in the field of cybersecurity.
The situation also highlights the importance of constant education and vigilance against new methods of cyber attacks for all participants in the digital space.
Source
