Lord777
Professional
- Messages
- 2,577
- Reaction score
- 1,553
- Points
- 113
The advantages of the ZPAQ format made it possible to bypass security features and collect data.
G Data discovered a new version of Agent Tesla malware delivered via a ZPAQ compressed decoy file to collect data from several email clients and nearly 40 web browsers.
G Data noted that ZPAQ offers better compression rates and a logging function compared to conventional formats (ZIP and RAR), but its disadvantage is limited software support.
Agent Tesla, which first appeared in 2014, is a keylogger and Remote Access Trojan (RAT) written in .NET. Agent Tesla is implemented under the "Malware-as-a-Service" model (Malware-as-a-Service, MaaS) and is usually used to provide remote access to compromised applications. systems, as well as for further downloading extortionate software.
In the detected campaigns, Agent Tesla is distributed through phishing emails, and in some cases the vulnerability CVE-2017-11882 (CVSS: 7.8) in the formula editor of Microsoft Office Equation Editor was exploited. The attack itself starts with an email containing an attachment in the form of a ZPAQ file, which looks like a PDF document. Opening the file causes the overflowing executable file to be unpacked .NET, the size of which was artificially increased to 1 GB to bypass standard security measures.
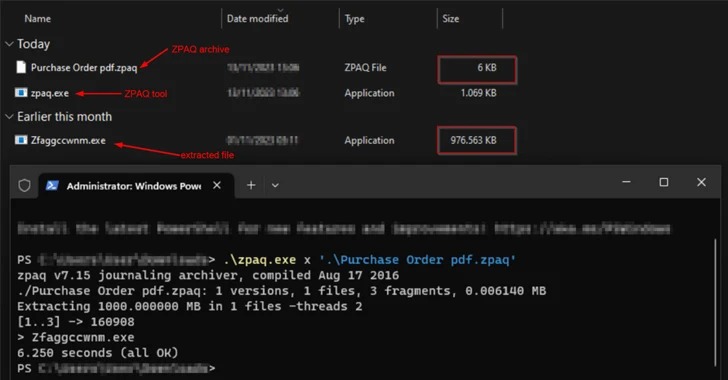
Files delivered during an attack
G Data explains that the main function of an executable file is to download and decrypt the file with the extension .wav in order to disguise malicious activity as normal traffic and make it difficult for network security solutions to detect it. The ultimate goal of the attack is to infect the device Agent Tesla, which is hidden behind .NET Reactor, a legitimate code protection software. Management takes place via Telegram.
The new development of attacks indicates that attackers are looking for new ways to deliver malware using unusual file formats. This trend requires users to be especially vigilant against suspicious emails and constantly update their systems. G Data noted that the use of ZPAQ in this context raises questions, suggesting that attackers are either targeting a specific group of people with technical knowledge, or testing new methods of distributing malware to bypass security systems.
G Data discovered a new version of Agent Tesla malware delivered via a ZPAQ compressed decoy file to collect data from several email clients and nearly 40 web browsers.
G Data noted that ZPAQ offers better compression rates and a logging function compared to conventional formats (ZIP and RAR), but its disadvantage is limited software support.
Agent Tesla, which first appeared in 2014, is a keylogger and Remote Access Trojan (RAT) written in .NET. Agent Tesla is implemented under the "Malware-as-a-Service" model (Malware-as-a-Service, MaaS) and is usually used to provide remote access to compromised applications. systems, as well as for further downloading extortionate software.
In the detected campaigns, Agent Tesla is distributed through phishing emails, and in some cases the vulnerability CVE-2017-11882 (CVSS: 7.8) in the formula editor of Microsoft Office Equation Editor was exploited. The attack itself starts with an email containing an attachment in the form of a ZPAQ file, which looks like a PDF document. Opening the file causes the overflowing executable file to be unpacked .NET, the size of which was artificially increased to 1 GB to bypass standard security measures.

Files delivered during an attack
G Data explains that the main function of an executable file is to download and decrypt the file with the extension .wav in order to disguise malicious activity as normal traffic and make it difficult for network security solutions to detect it. The ultimate goal of the attack is to infect the device Agent Tesla, which is hidden behind .NET Reactor, a legitimate code protection software. Management takes place via Telegram.
The new development of attacks indicates that attackers are looking for new ways to deliver malware using unusual file formats. This trend requires users to be especially vigilant against suspicious emails and constantly update their systems. G Data noted that the use of ZPAQ in this context raises questions, suggesting that attackers are either targeting a specific group of people with technical knowledge, or testing new methods of distributing malware to bypass security systems.

