Mutt
Professional
- Messages
- 1,458
- Reaction score
- 1,274
- Points
- 113

In general, "forensics" is a tracing paper from the English word forensics, which, in turn, is an abbreviated form of forensic science, "forensic science", that is, the science of the study of evidence. In Russian, this concept is often called forensics, and the word "forensics" was assigned to the computer part of it.
Forensics is the lot of specialists from the rapid response teams who are involved in the work if an incident occurs, for example, a hacking of a web server or a leak of confidential information, encryption of valuable data, and the like. In this case, forensic experts are assigned the following tasks:
- understand how the attack was implemented;
- build a hacking scenario;
- restore the chronology (timeline) of the attack;
- collect artifacts (in the sense, not the sword of Armageddon and not the holy grail, but the traces left after the attack);
- propose preventive protective measures so that this does not happen again.
Now more and more large companies from those that have their own brand of information security services, without fail, start a specialized laboratory and a staff of several forensics experts. Forensics is also often included in the services of companies that are far from the IT sector and are engaged, for example, in financial audit. Indeed, when investigating financial fraud, up to 100% of all evidence can be contained in computer systems (ERP, CRM, BI, BPM, and so on).
And, of course, forensics experts are an integral part of "K management". Indeed, in order to initiate a criminal case on the facts of computer crimes, first, according to the norms of the law, it is necessary to confirm the very fact of the crime and determine its composition. Similarly, if the injured party goes to court to recover the damage caused by the break-in, there is no way to do without an expert examination.
A separate topic is the investigation of targeted attacks, or APT. Their essence boils down to hacking target systems using a variety of attack vectors, tools, sophisticated techniques and methods unknown until now.
Classification
Any science tends to be divided into smaller topics. To finally feel like at the institute, let's look at the classification map of our subject.
- Computer forensics - it includes everything related to the search for hacking artifacts on a local machine: analysis of RAM, HDD, registry, OS logs, and so on.
- Network forensics - as the name implies, has to do with investigating the network stack, for example, dumping and parsing network traffic to reveal interesting things like RATs, reverse shells, backdoor tunnels, and the like.
- Forensic data analysis is devoted to the analysis of files, data structures and binary sequences left after an attack or used during an intrusion.
- Mobile device forensics deals with everything related to the features of data extraction from Android and iOS.
- Hardware forensic - The expertise of hardware and technical devices. This direction is the least popular and the most difficult. This includes parsing data at a low level (microcontroller, firmware or BIOS), researching specific features of the device's operation, for example, the frequency range of a Wi-Fi transmitter or an internal skimmer device installed on ATMs.
Expertise methods and techniques
As with malware analysis, there are two main approaches to examining a compromised machine - static and dynamic analysis.
The tasks of static analysis are to create (copy) an image of a hard disk or a dump of RAM, identify and restore deleted files, remnants of anomalous files in% TEMP% and system directories, collect web browser surfing history, system logs (authorization events, audit of file access and directories, and so on), get a list of processes running in memory and open network connections.
Dynamic analysis, or live analysis, uses snapshots of a system running under various conditions to get a complete picture of what is happening. For example, malware tends to delete its code and traces of infection after certain actions. And if a snapshot of the compromised system was taken before that moment, there is a real chance to get data on what this malware was doing on the victim's computer. Accordingly, screenshots, logs of connections to the network, transmitted traffic, comparison of the state of the OS file system before and after the incident can act as a filing of electronic evidence.
A car
Our main forensic distribution, containing a pack with all the necessary utilities, will be the legendary BackTrack. We use an image with Windows XP installed as the analyzed machine. BackTrack is recommended to run as a host OS, and for XP it is quite possible to be content with free Oracle VirtualBox or VMware Player.
Case 1. Finding and recovering a deleted JPEG file using Autopsy
The essence of this case is to find artifacts of a deleted file (JPEG image) on the hard disk of the target machine and restore it to another directory for further study.
The main tool for us in this task will be Autopsy - this is a digital platform for forensic procedures and at the same time a graphical interface for the CLI version of the famous whale The Sleuth Kit. In particular, the program allows you to analyze disk devices, find and recover files, extract EXIF from pictures, find and view individual video fragments. More information about the tool is available here and also here.
So, let's begin.
The first step is to launch BackTrack with a GUI interface. Open the browser and download the JPEG Search Test # 1 archive using the specified link , additional information on the file can be read here. Then press Ctrl + T and execute the following commands in the terminal window that appears.
Create directories:
Code:
# mkdir -p / var / forensics / images
# ls -ld / var / forensics / images
Let's unpack our archive:
# cd / var / forensics / images
# ls -lrta
# unzip 8-jpeg-search.zip
# cd 8-jpeg-search
# ls -lrta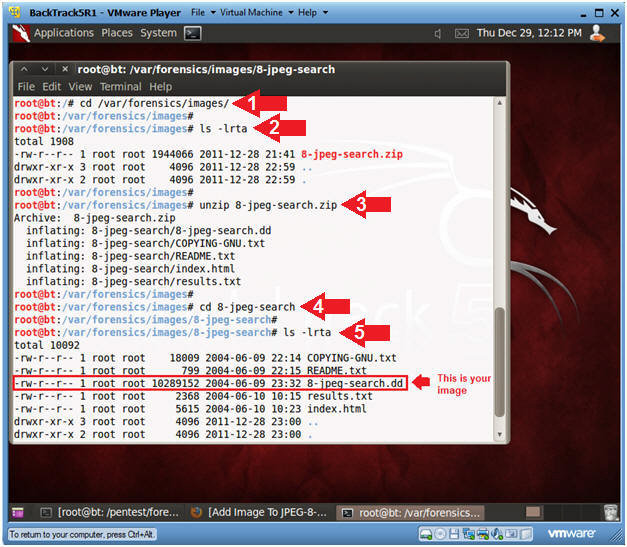
Unpacking the downloaded archive JPEG Search Test # 1
And we continue to type commands in the terminal:
Code:
# cd / var / forensics / images / 8-jpeg-search
# ls -l
# md5sum 8-jpeg-search.ddNow you need to calculate the hash of the file in md5sum.
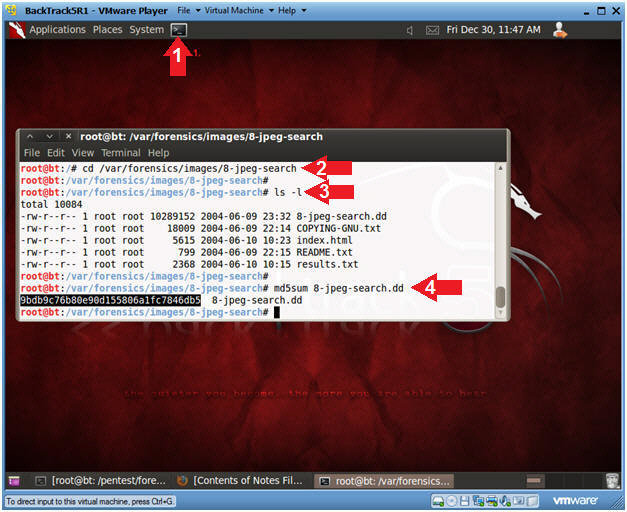
The MD5 hash of the unpacked file.
After that, launch our tool in the GUI shell: Applications → BackTrack → Forensics → Forensic Suites → setup Autopsy. After the window appears on the question Have you purchased or downloaded a copy of the NSRL (y / n), click n. Then go to /pentest/forensics/autopsyand run the script ./autopsy. The script starts a local web server with an interface for working with Autopsy.
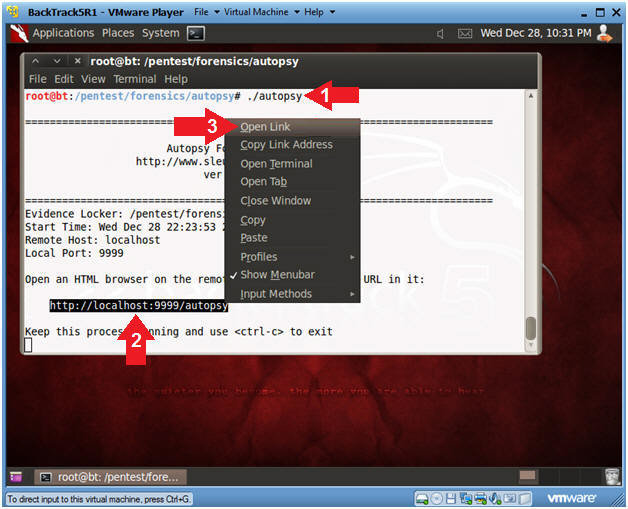
Running the ./autopsy script from the terminal.
As written in the text, we open the address http: // localhost: 9999 / autopsy in the browser. After that, the HTML shell of our tool appears in front of us in all its glory. All we need to do is create a "new case", enter the hostname, case name, other additional information and save the resulting template.
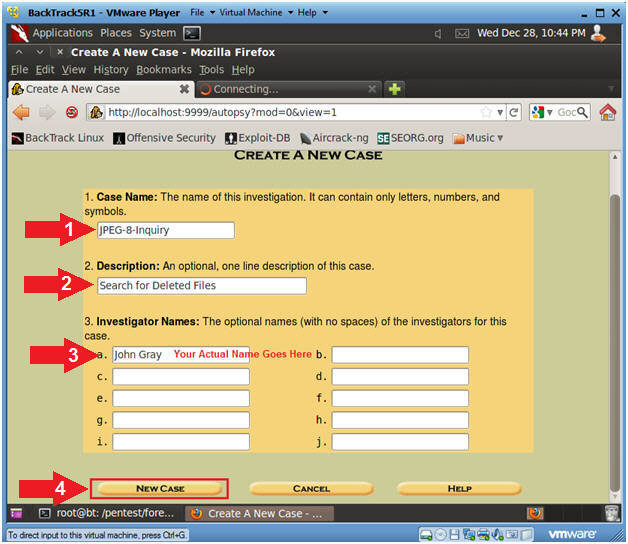
How to create a JPEG-8-Inquiry case.
Go to the terminal and execute the commands
Code:
# cd / var / forensics / images / 8-jpeg-search
# ls -l
# ls $ PWD / 8-jpeg-search.ddCopy the line.
Code:
/var/forensics/images/8-jpeg-search/8-jpeg-search.dd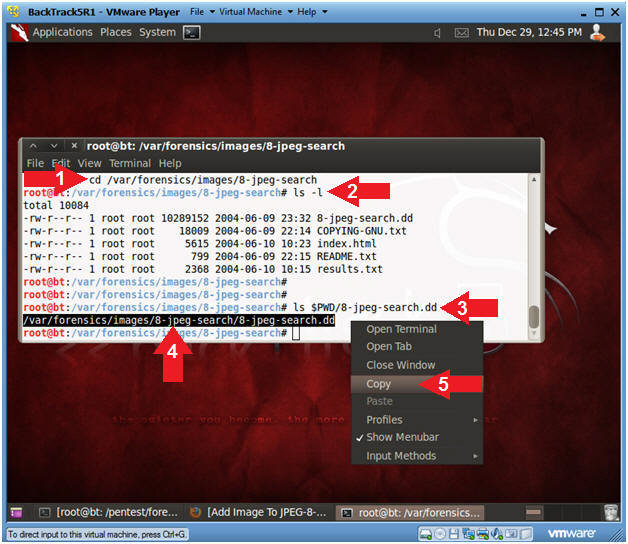
Copy the specified line in the terminal window.
Then we return to the browser and click "Add location / picture".
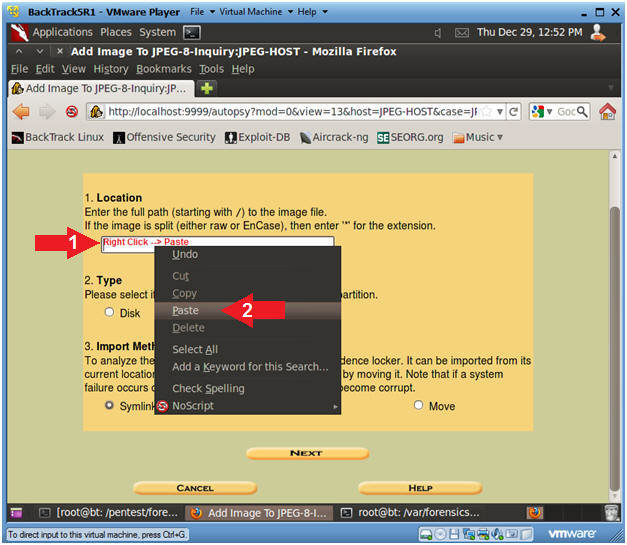
Paste the copied link into the specified form.
After that, traditionally, boldly click the Next button and on the new page of the wizard, click the Partition option.
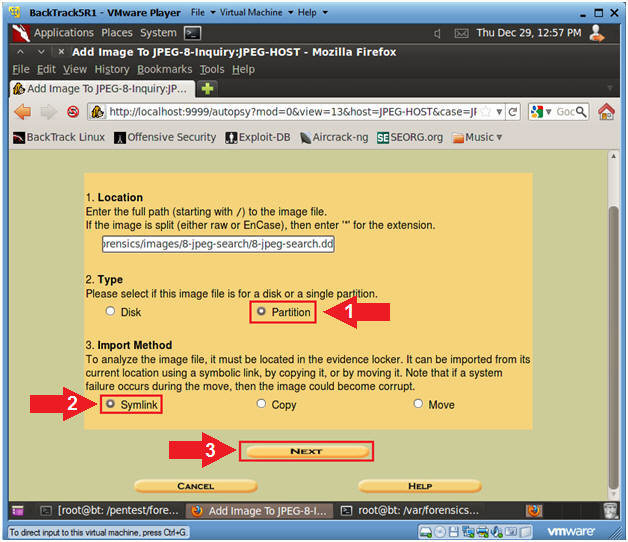
In the wizard window, select the Partition option.
In the next step, we need to do three actions, namely, click Ignore the hash value for this image, specify the C drive letter and the NTFS file system type.
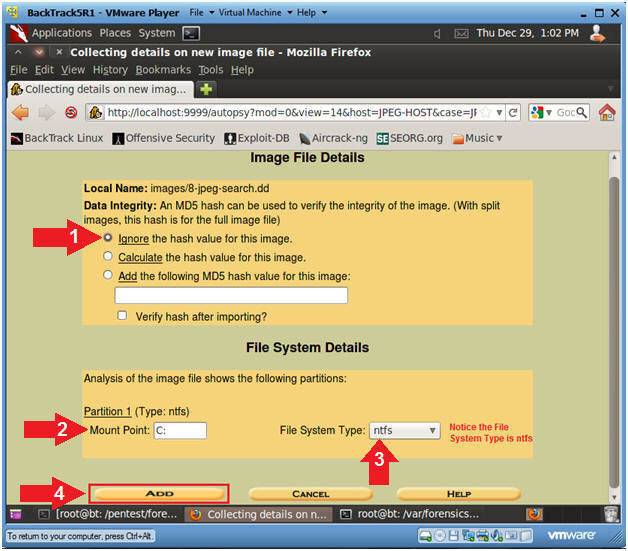
Fill in the fields with the specified data.
At the end of the step-by-step wizard, press the only Calculate button.
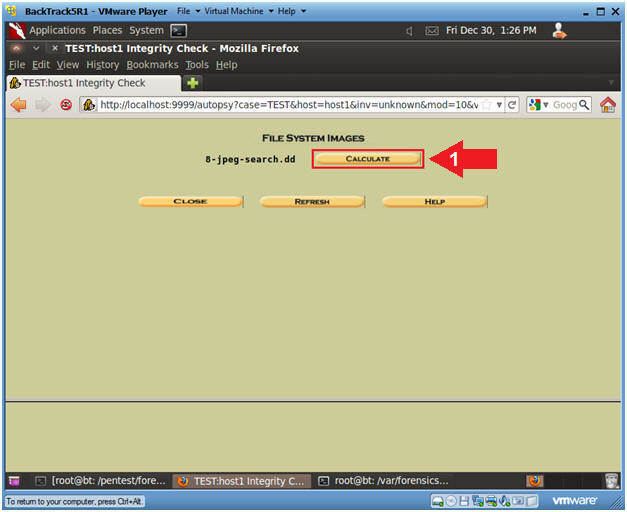
Closing the wizard by clicking the Calculate button.
Our next step is to analyze the file, determine its structure and content. The process is started by pressing the Analysis button.
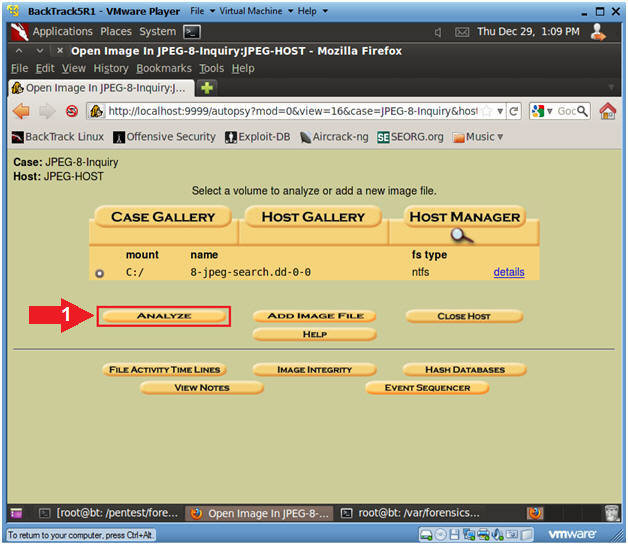
Start file analysis with the Analysis button.
After a few seconds of waiting, we will see a small report about the analyzed file - File information and Metadata information.
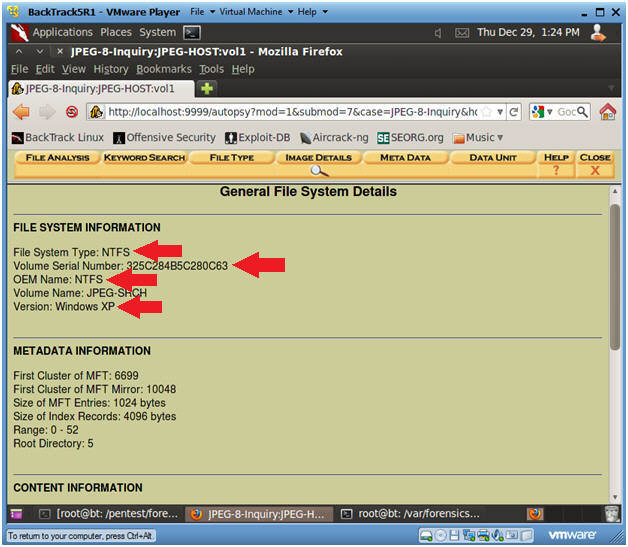
Summary of File information and Metadata information.
As a result, we will see a window with a list of deleted files and some additional information.
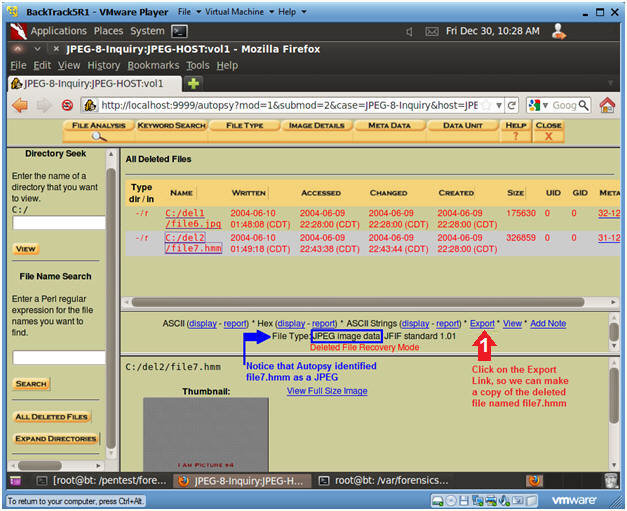
Summary window: deleted files found.
xakep.ru

