Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,324
- Points
- 113

The market of electronic payments in Ukraine and the world is growing rapidly, and with it the number of threats increases. Experts warn that the professionalism of cybercriminals is increasing every year, as is the variety of deception methods they use. However, phishing is still the most popular. How modern phishing works, what types of it are, and how to secure your finances on the Internet - let's try to figure it out.
The main purpose of phishing (English phishing, from distorted fishing - fishing) is to gain access to confidential user data. The long-term "success" of this method of Internet fraud is due to the low awareness of users about security measures and their gullibility.
Most often, phishing is carried out by sending bulk emails on behalf of well-known brands or banks. Such a letter contains a direct link to the site, which is outwardly difficult to distinguish from the real one, or a link to a site with a redirect. By clicking on the link, the user is taken to a fake bank page, where by various psychological methods he is prompted to enter his username and password to access the Internet bank. This is how criminals gain access to accounts and bank accounts.
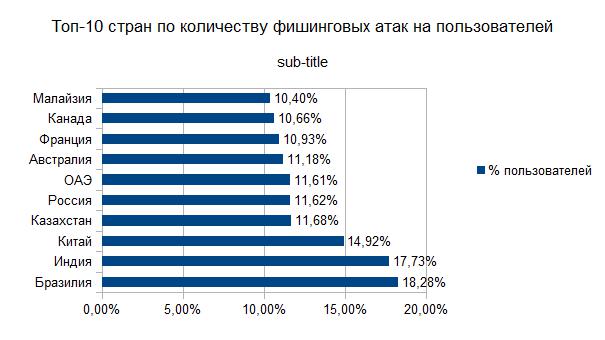
According to Kaspersky Lab, in the first quarter of 2021, the top 10 countries in terms of the number of phishing attacks on users were as follows:
There are several types of phishing. First of all, these are email, online and combined phishing.
Email phishing is the distribution of worms, Trojans and other viruses. Its danger lies in the fact that attackers can bypass the spam filters installed on the computer. Also, phishing messages can look like the official bank page and thus mislead the user.
Online phishing involves creating a fake online banking page for a customer, and it is extremely difficult to distinguish it from the original. Without suspecting anything, the user enters his username and password on such a page, and the scammers quickly intercept this data in order to use it later to log into the victim's account and transfer money to their accounts.
Combined phishing involves creating a fake bank website to lure potential victims. Fraudsters, allegedly on behalf of the bank, are in correspondence with the user, talk about new interesting banking products and recommend performing some operations on their own, for example, transferring funds from your account to a deposit opened especially for you. As a result of this, as in previous cases, fraudsters gain access to the user's account and transfer money to their accounts.
Phishing also has several varieties that few people have heard of. Distinguish between vishing, smishing and farming. How are these types of online scams different?
Vishing, or voice phishing, consists in using the capabilities of Internet telephony (VoIP) to steal access passwords, bank card numbers, etc. account or card. At the other end of the line, the user is called up by an answering machine, and at the end asks to enter the account number and PIN-code. As soon as this information reaches the scammers, they transfer all the money to their account.
Thus, the use of VoIP allows companies to reduce their telephone costs, but at the same time makes networks more vulnerable to attacks. Unfortunately, there are still no effective remedies for the prevention of vishing.

Smishing, or SMS phishing, consists in sending SMS messages to users from a supposedly reliable sender, for example, a bank. In an SMS message, a potential victim is asked to send some sensitive data, such as a card number and PIN. Often, an SMS message may also contain a link to a fake bank page, where the user is asked to enter the same data. The irony is that by sending personal data to criminals in an SMS message, you not only give them access to your funds, but also lose money from your mobile account, since SMS turns out to be paid.
In fact, it should be remembered that the bank will never call or write you and ask for bank card numbers, PIN codes, logins and passwords for online banking and other confidential information.
Pharming means replacing DNS addresses, that is, redirecting a user to a false address. Attackers replace DNS records on the servers of real sites, as a result of which the visitor is redirected to a similar but fake site. In this case, it is most difficult to detect fraud and distinguish a fake. In addition, there are no special protection mechanisms against pharming. Therefore, it is necessary to control incoming letters, use antivirus software, close preview windows in the mail client, and so on.
Analysts predict further active development of financial fraud, in particular, using methods of social engineering and phishing. Banks are aware of this dangerous trend and are stepping up investments in information security, because it is their clients that are most vulnerable to such threats and are most attractive to cybercriminals. However, only compliance with the rules for the safe storage of personal data and the use of finances on the Internet by the Internet user himself will save funds and resist the growing cyber fraud. Let us recall the main ones.
- Do not give your bank card number and PIN codes to unknown people, both on the Internet and in SMS correspondence.
- Update the antivirus software on your computer regularly.
- Pay attention to the page of the bank and other payment providers on the Internet. If it is not loaded via the secure HTTPS protocol (green padlock to the left of the address bar), then it is better to leave it.
- Do not enter payment card details from public computers.
- Connect SMS notification to your card to always be aware of all current transactions on it.
- Set a limit on electronic transactions on your card.
- Do not open suspicious links from letters and SMS messages from unknown senders.
- Use the virtual keyboard to enter the login and password for your personal account in Internet banking.
- Use cards with 3D-secure support for online payments.
- If you have lost the phone that receives the verification codes of your payment service, immediately block the SIM card.

