Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,038
- Points
- 113

The NSA, the Department of Homeland Security (DHS CISA), Cybersecurity and Infrastructure Protection Agency, the FBI and the UK National Cyber Security Center (NCSC) issued a joint statement warning that the Russian “government hack group from APT28 (aka Fancy Bear, Pawn Storm, Sednit, Strontium) actively brute-force the resources of public and private companies and organizations around the world.
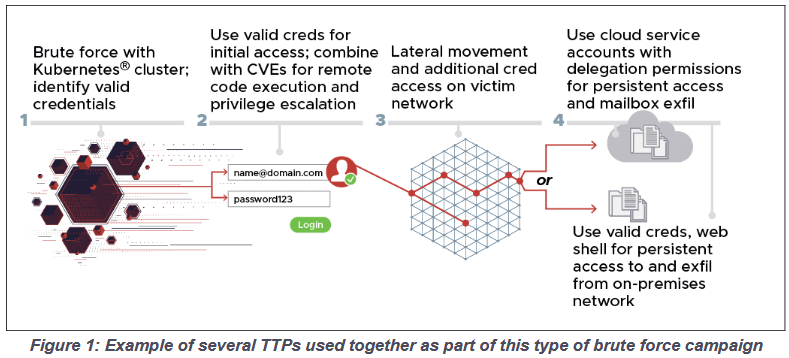
“From at least mid-2019 to early 2021, the 85th GRU Special Services Center, also known as Unit 26165, used the Kubernetes cluster to conduct large-scale, distributed and anonymous brute force attacks against hundreds of targets in the public and private sector.
If the brute-force was successful, the APT28 hackers used the compromised accounts to move laterally within the affected organizations' networks. Specifically, the agencies say APT28 used compromised credentials along with various exploits for vulnerabilities in Microsoft Exchange, including RCE issues CVE-2020-0688 and CVE-2020-17144, combining them to gain access to internal mail servers.The 85th GVC targeted much of this activity at organizations using Microsoft Office 365 cloud services, but attacks also targeted other service providers and on-premises mail servers using a variety of different protocols. This activity almost certainly continues to this day, ”the statement reads.
Attack scheme
These attacks reportedly went largely unnoticed as APT28 masked brute-force attacks via Tor or commercial VPN services including CactusVPN, IPVanish, NordVPN, ProtonVPN, Surfshark, and WorldVPN, and used Kubernetes clusters. Typically, brute-force was performed using a variety of protocols, including HTTP (S), IMAP (S), POP3, and NTLM, so attacks did not always go through the same channels.
The NSA states that between November 2020 and March 2021, hackers carried out attacks without using anonymization services, and as a result, the following IP addresses were identified:
- 158.58.173 [.] 40
- 185.141.63 [.] 47
- 185.233.185 [.] 21
- 188.214.30 [.] 76
- 195.154.250 [.] 89
- 93.115.28 [.] 161
- 95.141.36 [.] 180
- 77.83.247 [.] 81
- 192.145.125 [.] 42
- 193.29.187 [.] 60