Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
A company error can lead to a wave of phishing attacks and numerous hacks.
Last week, it became known that the support website of network equipment manufacturer Juniper Networks unintentionally disclosed potentially sensitive information about customers products, including data on purchased devices, warranty status, service contracts and serial numbers. According to the company, the problem has already been fixed. The error was related to a recent update to the support portal. This was reported by the KrebsOnSecurity portal.
A specialist responsible for managing Juniper devices discovered the ability to access information about devices and support contracts for other Juniper customers through the company's support portal.
Logan George, a 17-year-old intern who works for an organization that uses Juniper products, accidentally discovered the vulnerability when he was looking for information about support for a specific Juniper product.
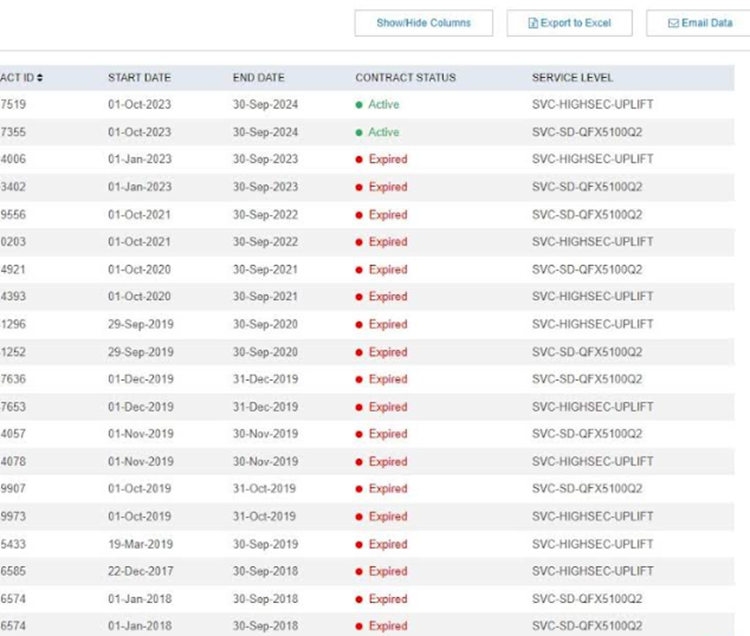
Expanded list of devices
By logging in with a regular user account, George was able to access detailed information about any Juniper device purchased by other customers. A Juniper search turned up tens of thousands of entries, including the model and serial number of the device, the approximate location of its installation, as well as the status of the device and information about the service contract associated with it.
George stressed that the disclosed information about service contracts can be sensitive, as it shows which Juniper products are devoid of critical security updates. If the user doesn't have a service contract, they don't get updates, the specialist explained.
Juniper said in an official statement that the data disclosure was the result of a recent update to the support portal. The company said it quickly fixed the issue and confirmed that customers ' personal data was not disclosed.
The company did not specify when exactly such excessive user rights were introduced. However, the changes may date back as far as September 2023, when Juniper announced a redesign of its customer support portal. George told KrebsOnSecurity that the backend of the Juniper support website appears to be supported by Salesforce, and that Juniper probably doesn't have proper user permissions set for its Salesforce assets.
Last year, the information security company Guardio disclosed a sophisticated phishing attack based on a zero-day vulnerability in Salesforce's email and SMTP servers. Attackers used the flaw to create fraudulent emails that mimicked messages from Salesforce. Thus, cybercriminals were able to bypass standard detection methods and attack users.
Last week, it became known that the support website of network equipment manufacturer Juniper Networks unintentionally disclosed potentially sensitive information about customers products, including data on purchased devices, warranty status, service contracts and serial numbers. According to the company, the problem has already been fixed. The error was related to a recent update to the support portal. This was reported by the KrebsOnSecurity portal.
A specialist responsible for managing Juniper devices discovered the ability to access information about devices and support contracts for other Juniper customers through the company's support portal.
Logan George, a 17-year-old intern who works for an organization that uses Juniper products, accidentally discovered the vulnerability when he was looking for information about support for a specific Juniper product.

Expanded list of devices
By logging in with a regular user account, George was able to access detailed information about any Juniper device purchased by other customers. A Juniper search turned up tens of thousands of entries, including the model and serial number of the device, the approximate location of its installation, as well as the status of the device and information about the service contract associated with it.
George stressed that the disclosed information about service contracts can be sensitive, as it shows which Juniper products are devoid of critical security updates. If the user doesn't have a service contract, they don't get updates, the specialist explained.
Juniper said in an official statement that the data disclosure was the result of a recent update to the support portal. The company said it quickly fixed the issue and confirmed that customers ' personal data was not disclosed.
The company did not specify when exactly such excessive user rights were introduced. However, the changes may date back as far as September 2023, when Juniper announced a redesign of its customer support portal. George told KrebsOnSecurity that the backend of the Juniper support website appears to be supported by Salesforce, and that Juniper probably doesn't have proper user permissions set for its Salesforce assets.
Last year, the information security company Guardio disclosed a sophisticated phishing attack based on a zero-day vulnerability in Salesforce's email and SMTP servers. Attackers used the flaw to create fraudulent emails that mimicked messages from Salesforce. Thus, cybercriminals were able to bypass standard detection methods and attack users.

