
Experts MalwareHunterTeam and Guido Not CISSP found that the black market was aggressively marketed and sold new Trojan Evrial. Like any other info-stealer, Evrial steals cookies and credentials from infected machines, but the authors also "taught" their brainchild to closely monitor the contents of the Windows clipboard.
Evrial does not steal everything from the clipboard. Instead, the Trojan waits for the cryptocurrency wallet address or Steam trade offer URL to be buffered. As soon as this happens, the malware replaces the wallet address or URL with an address or link belonging to the cybercriminals. The list of supported cryptocurrencies, browsers and so on can be seen below, in the screenshot of the advertisement.
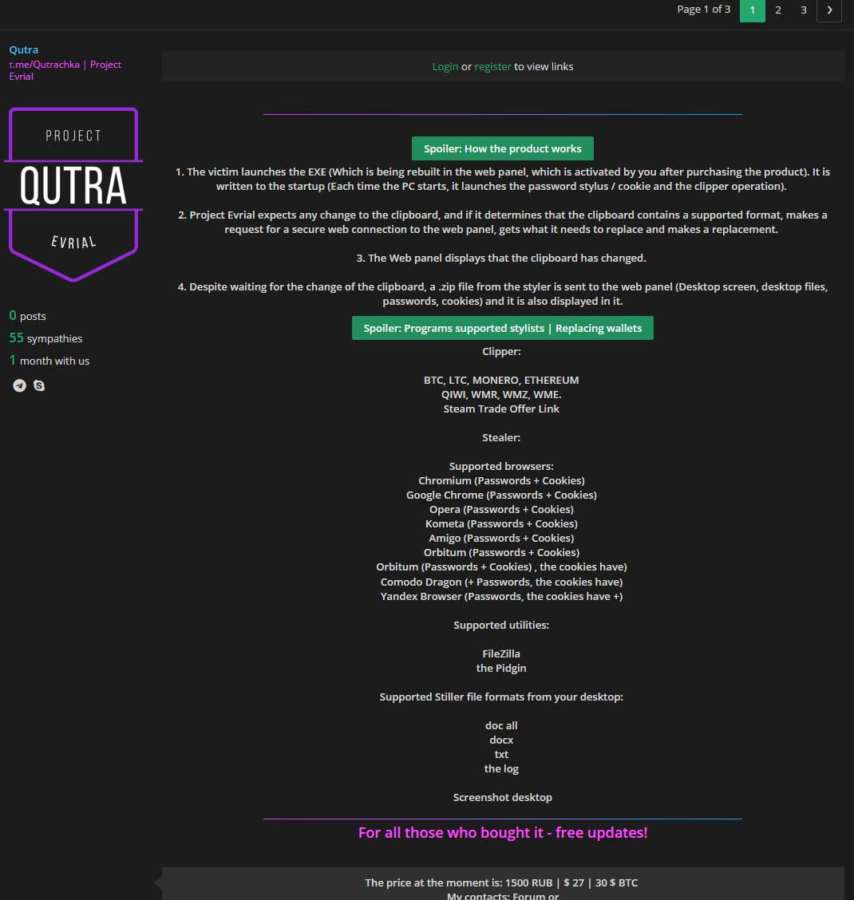
At present, researchers have not yet determined exactly how Evrial is distributed, but, according to MalwareHunterTeam, the Trojan is sold on Russian-language underground resources at a price of 1,500 rubles. For this amount, the buyer gets access to the web panel, where he can configure the malware in the way he needs: select addresses and links for replacement, and also track the spoofs already performed by the malware.
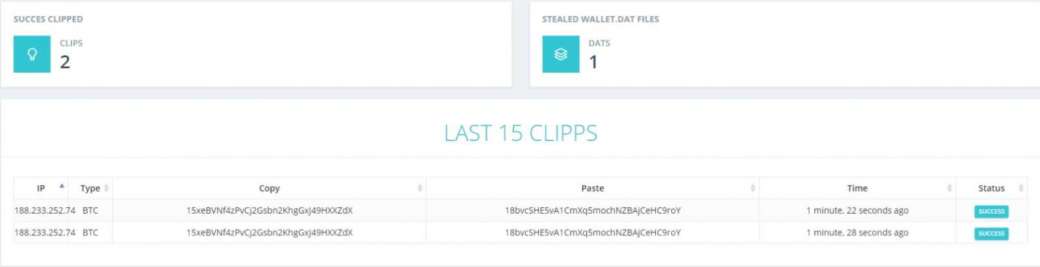
So, finding a string suitable for substitution, Evrial contacts the remote server and uploads it there, and in response receives a new sequence that needs to be substituted into the user's buffer.
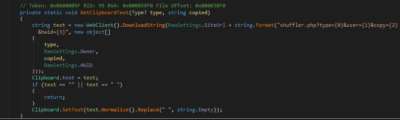
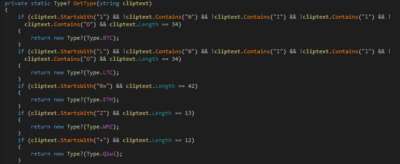
But just changing the data in the clipboard is not enough. Evrial also steals data about cryptocurrency wallets (wallet.dat files), passwords stored on the device (in particular from Chrome, Yandex, Orbitum, Opera, Amigo, Torch and Comodo browsers, as well as passwords stored in Pidgin and Filezilla), documentation , and takes snapshots of the victim's active windows. All this information is packed into an archive (ZIP) and uploaded to the management server. The stolen data can be viewed directly from the malware control panel.

xakep.ru
