Everyone knows that these six bytes, usually displayed in hexadecimal format, are assigned to the network card at the factory, and at first glance are random. Some people know that the first three bytes of an address are the manufacturer's identifier, and the remaining three bytes are assigned to them. It is also known that you can set an arbitrary address for yourself. Many people have also heard about" random addresses " in Wi-Fi.
Let's find out what it is.
MAC address (media access control address) – a unique identifier assigned to a network adapter, used in IEEE 802 networks, mainly Ethernet, Wi-Fi and Bluetooth. Officially, it is called the "EUI-48 type identifier". From the name, it is obvious that the address is 48 bits long, i.e. 6 bytes. There is no generally accepted standard for writing an address (as opposed to an IPv4 address, where octets are always separated by dots).It is usually written as six hexadecimal numbers separated by a colon: 00:AB:CD:EF:11: 22, although some hardware manufacturers prefer writing in the form 00-AB-CD-EF-11-22 and even 00ab. cdef. 1122.
Historically, addresses were flashed into the ROM of the network card chipset without the possibility of modifying them without a flash programmer, but now the address can be changed programmatically, from the operating system. You can manually set the MAC address of the network card in Linux and macOS (always), Windows (almost always, if the driver allows), Android (only rooted); with iOS (without root), this trick is not possible.
Google has only 40 of them, and this is not surprising: they do not produce so many network devices themselves.
MA blocks are not provided for free, but can be purchased for a reasonable amount of money (without a subscription fee) for $3000, $1800, or $755, respectively. Interestingly, for additional money (per year), you can purchase "hiding" public information about the selected block. As can be seen above, there are currently 232 of them.
The MAC address has 48 bits, of which 46 can be considered "useful" (why? read on), which gives 2 46 or 10 14 addresses, which is 2 14 times the IPv4 address space.
Currently, approximately half a trillion addresses are distributed, or only 0.73% of the total volume. MAC addresses are still very, very far away from being exhausted.
We divide each MAC address (six bytes) of each of the samples into bits byte-by-byte, and look at the frequency of occurrence of bit " 1 " in each of the 48 positions. If the bit is set in a completely arbitrary way, then the probability of getting a " 1 " should be 50%.
Why such an injustice in 7 and 8 bits? There are almost always zeros.
Indeed, the standard defines these bits as special (Wikipedia):

The eighth (from the beginning) bit of the first byte of the MAC address is called the Unicast / Multicast bit and determines which type of frame (frame) is transmitted with this address, regular (0) or broadcast (1) (multicast or broadcast). For normal, unicast network adapter communication, this bit is set to "0" in all packets sent by the network adapter.
The seventh (from the beginning) bit of the first byte of the MAC address is called the U/L (Universal/Local) bit and determines whether the address is globally unique (0) or locally unique (1). By default, all" flashed by the manufacturer "addresses are globally unique, so the vast majority of MAC addresses collected contain the seventh bit set to "0". In the table of assigned OUI identifiers, only about 130 entries have the U/L bit "1", and apparently these are MAC address blocks for special needs.
From the sixth to the first bits of the first byte, bits of the second and third bytes in the OUI identifiers, and even more so bits in 4-6 bytes of the address assigned by the manufacturer, are more or less evenly distributed.
Thus, in the real MAC address of the network adapter, the bits are actually equivalent and do not carry any technological meaning, except for the two service bits of the highest byte.
I wonder which manufacturers of wireless equipment are most popular? Combine the OUI database search with sample # 1 data.
Practice shows that the more affluent the number of wireless network subscribers in a given location, the greater the share of Apple devices.
they set the last three bytes of the MAC address to a random number, apparently after each reboot of the device. There were 82,000 such addresses in my sample #1.
You can, of course, set up someone else's address that is not unique by purposefully setting it "like a neighbor's", using a sniffer, or selecting it at random. It is also possible to accidentally set yourself a non-unique address by performing, for example, restoring the configuration backup of some router like Mikrotik or OpenWRT.
What happens if there are two devices on the network with the same MAC address? It all depends on the logic of the network equipment (wired router, wireless network controller). Most likely, both devices will either not work or will work intermittently. From the point of view of IEEE standards, protection against MAC address forgery is proposed to be solved using, for example, MACsec or 802.1 X.
What if you set yourself a MAC with the seventh or eighth bit set to "1", i.e. a local or multicast address? Most likely, your network will not pay attention to this, but formally such an address will not comply with the standard, and it is better not to do so.
Enabled randomization allows you to specify not a" flashed " one, but some other source address of the packet that changes with each scan cycle, over time, or something else. Does it work? Let's look at the statistics of MAC addresses collected from the air by the so-called "Wi-Fi Radar":
The picture is quite different.
The 8th bit of the first byte of the MAC address still corresponds to the Unicast nature of the SRC address in the probe request packet.
The 7th bit is set to Local in 92.2% of cases, i.e. we can assume with a sufficient degree of confidence that exactly this number of collected addresses belongs to randomized ones, and less than 8% — to real ones. At the same time, the distribution of bits in the OUI for such real addresses approximately coincides with the data in the previous table.
Which manufacturer, according to the OUI, owns randomized addresses (i.e. with 7m bits in "1")?
However, all randomized addresses assigned to Google belong to the same OUI with the DA prefix:A1:19. What is this prefix? Let's take a look at the Android source code.
Stock android uses a special registered OUI to search for wireless networks, one of the few with the seventh bit installed.
The entire address, or its lower three bytes, is pure Random. nextLong(). "Patent recovery of real MAC" is a scam. With a high degree of confidence, we can expect that manufacturers of Android phones also use other non-registered OUI. We don't have the source code for iOS, but most likely it uses a similar algorithm.
The above does not negate the operation of other Wi-Fi subscriber deanonymization mechanisms based on the analysis of other probe request frame fields, or correlation of the relative frequency of requests sent by the device. However, it is extremely problematic to reliably track the subscriber by external means. The data collected is more suitable for analyzing the average/peak load by location and time, based on large numbers, without being tied to specific devices and people. Accurate data is available only for those who are "inside", for mobile OS manufacturers themselves, and for installed applications.
What can be dangerous if someone else finds out the MAC address of your device? For wired and wireless networks, you can launch a denial-of-service attack. For a wireless device, in addition, it is possible to record the moment of appearance in the place where the sensor is installed with some probability. By spoofing the address, you can try to "introduce yourself" as your device, which can only work if additional security features (authorization and/or encryption) are not applied. 99.9% of people here have nothing to worry about.
The MAC address is more complex than it sounds, but simpler than it could be.
Let's find out what it is.
MAC address (media access control address) – a unique identifier assigned to a network adapter, used in IEEE 802 networks, mainly Ethernet, Wi-Fi and Bluetooth. Officially, it is called the "EUI-48 type identifier". From the name, it is obvious that the address is 48 bits long, i.e. 6 bytes. There is no generally accepted standard for writing an address (as opposed to an IPv4 address, where octets are always separated by dots).It is usually written as six hexadecimal numbers separated by a colon: 00:AB:CD:EF:11: 22, although some hardware manufacturers prefer writing in the form 00-AB-CD-EF-11-22 and even 00ab. cdef. 1122.
Historically, addresses were flashed into the ROM of the network card chipset without the possibility of modifying them without a flash programmer, but now the address can be changed programmatically, from the operating system. You can manually set the MAC address of the network card in Linux and macOS (always), Windows (almost always, if the driver allows), Android (only rooted); with iOS (without root), this trick is not possible.
Address structure
The address consists of part of the manufacturer's identifier, OUI, and the identifier assigned by the manufacturer. The assignment of OUI (Organizationally Unique Identifier) identifiers is handled by the IEEE organization. In fact, its length can be not only 3 bytes (24 bits), but 28 or 36 bits, which form blocks (MAC Address Block, MA) of addresses of the Large (MA-L), Medium (MA-M) and Small (MA-S) types, respectively. The size of the issued block, in this case, will be 24, 20, 12 bits, or 16 million, 1 million, or 4 thousand addresses. Currently, about 38 thousand blocks are distributed, and you can view them with numerous online tools, such as IEEE or Wireshark.Who owns the addresses
Simple processing of a publicly available IEEE upload database provides quite a lot of information. For example, some organizations have taken a lot of OUI blocks for themselves. Here are our heroes:| Vendor | Number of blocks/records | Number of addresses, million. |
|---|---|---|
| Cisco Systems Inc | 888 | 14208 |
| Apple | 772 | 12352 |
| Samsung | 636 | 10144 |
| Huawei Technologies Co.Ltd | 606 | 9696 |
| Intel Corporation | 375 | 5776 |
| ARRIS Group Inc. | 319 | 5104 |
| Nokia Corporation | 241 | 3856 |
| Private | 232 | 2704 |
| Texas Instruments | 212 | 3392 |
| zte corporation | 198 | 3168 |
| IEEE Registration Authority | 194 | 3072 |
| Hewlett Packard | 149 | 2384 |
| Hon Hai Precision | 136 | 2176 |
| TP-LINK | 134 | 2144 |
| Dell Inc. | 123 | 1968 |
| Juniper Networks | 110 | 1760 |
| Sagemcom Broadband SAS | 97 | 1552 |
| Fiberhome Telecommunication Technologies Co. LTD | 97 | 1552 |
| Xiaomi Communications Co Ltd | 88 | 1408 |
| Guangdong Oppo Mobile Telecommunications Corp.Ltd | 82 | 1312 |
Google has only 40 of them, and this is not surprising: they do not produce so many network devices themselves.
MA blocks are not provided for free, but can be purchased for a reasonable amount of money (without a subscription fee) for $3000, $1800, or $755, respectively. Interestingly, for additional money (per year), you can purchase "hiding" public information about the selected block. As can be seen above, there are currently 232 of them.
When will the MAC addresses run out?
We are all pretty tired of the stories that have been going on for 10 years that "IPv4 addresses are about to run out". Yes, new IPv4 blocks are no longer easy to get. At the same time, it is known that IP addresses are extremely unevenly distributed; there are huge and little-used blocks belonging to large corporations and a US government agency, however, without much hope of their redistribution in favor of those in need. The proliferation of NAT, CG-NAT, and IPv6 has made the problem of lack of public addresses less acute.The MAC address has 48 bits, of which 46 can be considered "useful" (why? read on), which gives 2 46 or 10 14 addresses, which is 2 14 times the IPv4 address space.
Currently, approximately half a trillion addresses are distributed, or only 0.73% of the total volume. MAC addresses are still very, very far away from being exhausted.
Randomness of bits
It can be assumed that the OUI is randomly distributed, and the vendor then also randomly assigns addresses to individual network devices. Is it so? Let's look at the distribution of bits in the available databases of MAC addresses of 802.11 devices collected by working authorization systems in WNAM wireless networks. The addresses belong to real devices that have been connected to Wi-Fi for several years in three countries. In addition, there is a small base of 802.3 wired LAN devices.We divide each MAC address (six bytes) of each of the samples into bits byte-by-byte, and look at the frequency of occurrence of bit " 1 " in each of the 48 positions. If the bit is set in a completely arbitrary way, then the probability of getting a " 1 " should be 50%.
| Wi-Fi Sample #1 (Russian Federation) | Wi-Fi sample #2 (Belarus) | Wi-Fi Sample #3 (Uzbekistan) | LAN Sampling (RF) | |
|---|---|---|---|---|
| Number of records in the database | 5929000 | 1274000 | 366000 | 1000 |
| Bit Number: | % bit "1" | % bit "1" | % bit "1" | % bit "1" |
| 1 | 48.6% | 49.2% | 50.7% | 28.7% |
| 2 | 44.8% | 49.1% | 47.7% | 30.7% |
| 3 | 46.7% | 48.3% | 46.8% | 35.8% |
| 4 | 48.0% | 48.6% | 49.8% | 37.1% |
| 5 | 45.7% | 46.9% | 47.0% | 32.3% |
| 6 | 46.6% | 46.7% | 47.8% | 27.1% |
| 7 | 0.3% | 0.3% | 0.2% | 0.7% |
| 8 | 0.0% | 0.0% | 0.0% | 0.0% |
| 9 | 48.1% | 50.6% | 49.4% | 38.1% |
| 10 | 49.1% | 50.2% | 47.4% | 42.7% |
| 11 | 50.8% | 50.0% | 50.6% | 42.9% |
| 12 | 49.0% | 48.4% | 48.2% | 53.7% |
| 13 | 47.6% | 47.0% | 46.3% | 48.5% |
| 14 | 47.5% | 47.4% | 51.7% | 46.8% |
| 15 | 48.3% | 47.5% | 48.7% | 46.1% |
| 16 | 50.6% | 50.4% | 51.2% | 45.3% |
| 17 | 49.4% | 50.4% | 54.3% | 38.2% |
| 18 | 49.8% | 50.5% | 51.5% | 51.9% |
| 19 | 51.6% | 53.3% | 53.9% | 42.6% |
| 20 | 46.6% | 46.1% | 45.5% | 48.4% |
| 21 | 51.7% | 52.9% | 47.7% | 48.9% |
| 22 | 49.2% | 49.6% | 41.6% | 49.8% |
| 23 | 51.2% | 50.9% | 47.0% | 41.9% |
| 24 | 49.5% | 50.2% | 50.1% | 47.5% |
| 25 | 47.1% | 47.3% | 47.7% | 44.2% |
| 26 | 48.6% | 48.6% | 49.2% | 43.9% |
| 27 | 49.8% | 49.0% | 49.7% | 48.9% |
| 28 | 49.3% | 49.3% | 49.7% | 55.1% |
| 29 | 49.5% | 49.4% | 49.8% | 49.8% |
| 30 | 49.8% | 49.8% | 49.7% | 52.1% |
| 31 | 49.5% | 49.7% | 49.6% | 46.6% |
| 32 | 49.4% | 49.7% | 49.5% | 47.5% |
| 33 | 49.4% | 49.8% | 49.7% | 48.3% |
| 34 | 49.7% | 50.0% | 49.6% | 44.9% |
| 35 | 49.9% | 50.0% | 50.0% | 50.6% |
| 36 | 49.9% | 49.9% | 49.8% | 49.1% |
| 37 | 49.8% | 50.0% | 49.9% | 51.4% |
| 38 | 50.0% | 50.0% | 49.8% | 51.8% |
| 39 | 49.9% | 50.0% | 49.9% | 55.7% |
| 40 | 50.0% | 50.0% | 50.0% | 49.5% |
| 41 | 49.9% | 50.0% | 49.9% | 52.2% |
| 42 | 50.0% | 50.0% | 50.0% | 53.9% |
| 43 | 50.1% | 50.0% | 50.3% | 56.1% |
| 44 | 50.1% | 50.0% | 50.1% | 45.8% |
| 45 | 50.0% | 50.0% | 50.1% | 50.1% |
| 46 | 50.0% | 50.0% | 50.1% | 49.5% |
| 47 | 49.2% | 49.4% | 49.7% | 45.2% |
| 48 | 49.9% | 50.1% | 50.7% | 54.6% |
Why such an injustice in 7 and 8 bits? There are almost always zeros.
Indeed, the standard defines these bits as special (Wikipedia):

The eighth (from the beginning) bit of the first byte of the MAC address is called the Unicast / Multicast bit and determines which type of frame (frame) is transmitted with this address, regular (0) or broadcast (1) (multicast or broadcast). For normal, unicast network adapter communication, this bit is set to "0" in all packets sent by the network adapter.
The seventh (from the beginning) bit of the first byte of the MAC address is called the U/L (Universal/Local) bit and determines whether the address is globally unique (0) or locally unique (1). By default, all" flashed by the manufacturer "addresses are globally unique, so the vast majority of MAC addresses collected contain the seventh bit set to "0". In the table of assigned OUI identifiers, only about 130 entries have the U/L bit "1", and apparently these are MAC address blocks for special needs.
From the sixth to the first bits of the first byte, bits of the second and third bytes in the OUI identifiers, and even more so bits in 4-6 bytes of the address assigned by the manufacturer, are more or less evenly distributed.
Thus, in the real MAC address of the network adapter, the bits are actually equivalent and do not carry any technological meaning, except for the two service bits of the highest byte.
Prevalence rate
I wonder which manufacturers of wireless equipment are most popular? Combine the OUI database search with sample # 1 data.
| Vendor | Device Share, % |
|---|---|
| Apple | 26,09 |
| Samsung | 19,79 |
| Huawei Technologies Co. Ltd | 7,80 |
| Xiaomi Communications Co Ltd | 6,83 |
| Sony Mobile Communications Inc | 3,29 |
| LG Electronics (Mobile Communications) | 2,76 |
| ASUSTek COMPUTER INC. | 2,58 |
| TCT mobile ltd | 2,13 |
| zte corporation | 2,00 |
| not found in the IEEE database | 1,92 |
| Lenovo Mobile Communication Technology Ltd. | 1,71 |
| HTC Corporation | 1,68 |
| Murata Manufactuaring | 1,31 |
| InPro Comm | 1,26 |
| Microsoft Corporation | 1,11 |
| Shenzhen TINNO Mobile Technology Corp. | 1,02 |
| Motorola (Wuhan) Mobility Technologies Communication Co. Ltd. | 0,93 |
| Nokia Corporation | 0,88 |
| Shanghai Wind Technologies Co. Ltd | 0,74 |
| Lenovo Mobile Communication (Wuhan) Company Limited | 0,71 |
Practice shows that the more affluent the number of wireless network subscribers in a given location, the greater the share of Apple devices.
Uniqueness
Are MAC addresses unique? In theory, yes, since each of the device manufacturers (owners of the MA block) must provide a unique address for each of the network adapters they produce. However, some chip manufacturers, namely:- 00:0A:F5 Airgo Networks, Inc. (now Qualcomm)
- 00: 08: 22 InPro Comm (now MediaTek)
they set the last three bytes of the MAC address to a random number, apparently after each reboot of the device. There were 82,000 such addresses in my sample #1.
You can, of course, set up someone else's address that is not unique by purposefully setting it "like a neighbor's", using a sniffer, or selecting it at random. It is also possible to accidentally set yourself a non-unique address by performing, for example, restoring the configuration backup of some router like Mikrotik or OpenWRT.
What happens if there are two devices on the network with the same MAC address? It all depends on the logic of the network equipment (wired router, wireless network controller). Most likely, both devices will either not work or will work intermittently. From the point of view of IEEE standards, protection against MAC address forgery is proposed to be solved using, for example, MACsec or 802.1 X.
What if you set yourself a MAC with the seventh or eighth bit set to "1", i.e. a local or multicast address? Most likely, your network will not pay attention to this, but formally such an address will not comply with the standard, and it is better not to do so.
How randomization works
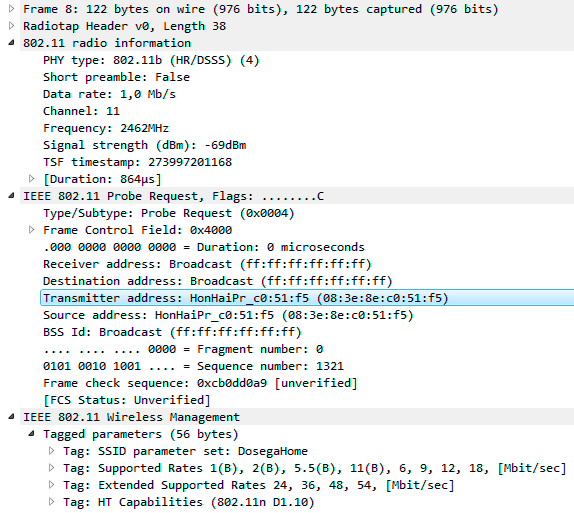
We know that smartphone operating systems have been using randomization technology for several years to prevent tracking people's movements by scanning the ether and collecting MAC data. Theoretically, when scanning the ether for known networks, the smartphone sends a packet (group of packets) of the type 802.11 probe request with the MAC address as the source:
Enabled randomization allows you to specify not a" flashed " one, but some other source address of the packet that changes with each scan cycle, over time, or something else. Does it work? Let's look at the statistics of MAC addresses collected from the air by the so-called "Wi-Fi Radar":
| The entire sample | Sampling only with the null 7th bit | |
|---|---|---|
| Number of records in the database | 3920000 | 305000 |
| Bit Number: | % bit "1" | % bit "1" |
| 1 | 66.1% | 43.3% |
| 2 | 66.5% | 43.4% |
| 3 | 31.7% | 43.8% |
| 4 | 66.6% | 46.4% |
| 5 | 66.7% | 45.7% |
| 6 | 31.9% | 46.4% |
| 7 | 92.2% | 0.0% |
| 8 | 0.0% | 0.0% |
| 9 | 67.2% | 47.5% |
| 10 | 32.3% | 45.6% |
| 11 | 66.9% | 45.3% |
| 12 | 32.3% | 46.8% |
| 13 | 32.6% | 50.1% |
| 14 | 33.0% | 56.1% |
| 15 | 32.5% | 45.0% |
| 16 | 67.2% | 48.3% |
| 17 | 33.2% | 56.9% |
| 18 | 33.3% | 56.8% |
| 19 | 33.3% | 56.3% |
| 20 | 66.8% | 43.2% |
| 21 | 67.0% | 46.4% |
| 22 | 32.6% | 50.1% |
| 23 | 32.9% | 51.2% |
| 24 | 67.6% | 52.2% |
| 25 | 49.8% | 47.8% |
| 26 | 50.0% | 50.0% |
| 27 | 50.0% | 50.2% |
| 28 | 50.0% | 49.8% |
| 29 | 50.0% | 49.4% |
| 30 | 50.0% | 50.0% |
| 31 | 50.0% | 49.7% |
| 32 | 50.0% | 49.9% |
| 33 | 50.0% | 49.7% |
| 34 | 50.0% | 49.6% |
| 35 | 50.0% | 50.1% |
| 36 | 50.0% | 49.5% |
| 37 | 50.0% | 49.9% |
| 38 | 50.0% | 49.8% |
| 39 | 50.0% | 49.9% |
| 40 | 50.0% | 50.1% |
| 41 | 50.0% | 50.2% |
| 42 | 50.0% | 50.2% |
| 43 | 50.0% | 50.1% |
| 44 | 50.0% | 50.1% |
| 45 | 50.0% | 50.0% |
| 46 | 50.0% | 49.8% |
| 47 | 50.0% | 49.8% |
| 48 | 50.1% | 50.9% |
The picture is quite different.
The 8th bit of the first byte of the MAC address still corresponds to the Unicast nature of the SRC address in the probe request packet.
The 7th bit is set to Local in 92.2% of cases, i.e. we can assume with a sufficient degree of confidence that exactly this number of collected addresses belongs to randomized ones, and less than 8% — to real ones. At the same time, the distribution of bits in the OUI for such real addresses approximately coincides with the data in the previous table.
Which manufacturer, according to the OUI, owns randomized addresses (i.e. with 7m bits in "1")?
| OUI Software Manufacturer | Share among all addresses |
|---|---|
| not found in the IEEE database | 62.45% |
| Google Inc. | 37.54% |
| the others | 0.01% |
However, all randomized addresses assigned to Google belong to the same OUI with the DA prefix:A1:19. What is this prefix? Let's take a look at the Android source code.
Code:
private static final MacAddress BASE_GOOGLE_MAC = MacAddress.fromString("da:a1:19:0:0:0");Stock android uses a special registered OUI to search for wireless networks, one of the few with the seventh bit installed.
Calculate the real MAC from a random one
Let's see in the same place:
Code:
private static final long VALID_LONG_MASK = (1L << 48) - 1;
private static final long LOCALLY_ASSIGNED_MASK = MacAddress.fromString("2:0:0:0:0:0").mAddr;
private static final long MULTICAST_MASK = MacAddress.fromString("1:0:0:0:0:0").mAddr;
public static @NonNull MacAddress createRandomUnicastAddress(MacAddress base, Random r) {
long addr;
if (base == null) {
addr = r.nextLong() & VALID_LONG_MASK;
} else {
addr = (base.mAddr & OUI_MASK) | (NIC_MASK & r.nextLong());
}
addr |= LOCALLY_ASSIGNED_MASK;
addr &= ~MULTICAST_MASK;
MacAddress mac = new MacAddress(addr);
if (mac.equals(DEFAULT_MAC_ADDRESS)) {
return createRandomUnicastAddress(base, r);
}
return mac;
}The entire address, or its lower three bytes, is pure Random. nextLong(). "Patent recovery of real MAC" is a scam. With a high degree of confidence, we can expect that manufacturers of Android phones also use other non-registered OUI. We don't have the source code for iOS, but most likely it uses a similar algorithm.
The above does not negate the operation of other Wi-Fi subscriber deanonymization mechanisms based on the analysis of other probe request frame fields, or correlation of the relative frequency of requests sent by the device. However, it is extremely problematic to reliably track the subscriber by external means. The data collected is more suitable for analyzing the average/peak load by location and time, based on large numbers, without being tied to specific devices and people. Accurate data is available only for those who are "inside", for mobile OS manufacturers themselves, and for installed applications.
What can be dangerous if someone else finds out the MAC address of your device? For wired and wireless networks, you can launch a denial-of-service attack. For a wireless device, in addition, it is possible to record the moment of appearance in the place where the sensor is installed with some probability. By spoofing the address, you can try to "introduce yourself" as your device, which can only work if additional security features (authorization and/or encryption) are not applied. 99.9% of people here have nothing to worry about.
The MAC address is more complex than it sounds, but simpler than it could be.
