Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,323
- Points
- 113
An old vulnerability has become a ransomware tool.
Fixed vulnerability in Veeam Backup & Replication is used by the new extortionist program EstateRansomware. Group-IB, which discovered the attacker in early April 2024, said that the attack included exploiting the vulnerability CVE-2023-27532 to carry out malicious activities.
CVE-2023-27532 (CVSS score: 7.5) allows you to obtain encrypted credentials stored in the configuration database, which can lead to access to backup infrastructure hosts.
The bug was fixed in early March 2023, and then a PoC exploit was published for the flaw. The vulnerability affects all versions of the software and can be used by unauthorized attackers to steal credentials and execute code remotely on behalf of SYSTEM.
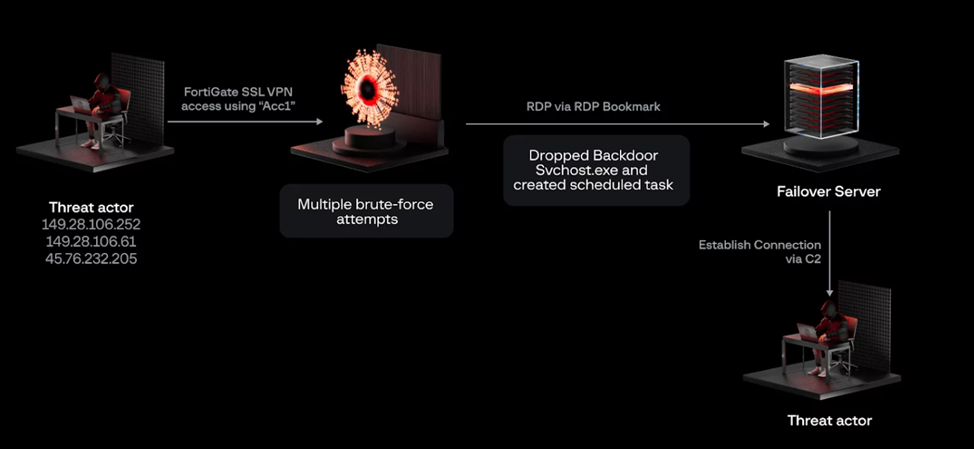
Attack Chain
It is reported that the initial access to the target environment was made using the SSL VPN device of the Fortinet FortiGate firewall using an inactive "Acc1" account. The attacker switched from the FortiGate firewall to the SSL VPN service to gain access to the failover server.
The hacker then proceeded to install RDP connections from the firewall to the failover server, and then deployed a permanent backdoor called "svchost.exe", which is executed daily as part of a scheduled task.
Subsequent access to the network was carried out using a backdoor to avoid detection. The main task of the backdoor is to connect to the C2 server via HTTP and execute arbitrary commands.
Group-IB discovered how an attacker exploits the Veeam vulnerability to enable xp_cmdshell on the backup server and create a fraudulent user account named "VeeamBkp", as well as performs network discovery, enumeration, and collection of credentials using NetScan, AdFind, and NitSoft tools.
The exploit potentially involved an attack originating from the VeeamHax folder on the file server against a vulnerable version of Veeam Backup & Replication installed on the backup server. This activity enabled the activation of the stored procedure " xp_cmdshell "and the subsequent creation of the account"VeeamBkp".
Note that Windows Defender was permanently disabled using DC.exe (Defender Control), after which the ransomware program was downloaded and executed using PsExec.exe. Also, before this, steps were taken to weaken security and move laterally from the AD server to all other servers and workstations using compromised domain accounts.
Source
Fixed vulnerability in Veeam Backup & Replication is used by the new extortionist program EstateRansomware. Group-IB, which discovered the attacker in early April 2024, said that the attack included exploiting the vulnerability CVE-2023-27532 to carry out malicious activities.
CVE-2023-27532 (CVSS score: 7.5) allows you to obtain encrypted credentials stored in the configuration database, which can lead to access to backup infrastructure hosts.
The bug was fixed in early March 2023, and then a PoC exploit was published for the flaw. The vulnerability affects all versions of the software and can be used by unauthorized attackers to steal credentials and execute code remotely on behalf of SYSTEM.

Attack Chain
It is reported that the initial access to the target environment was made using the SSL VPN device of the Fortinet FortiGate firewall using an inactive "Acc1" account. The attacker switched from the FortiGate firewall to the SSL VPN service to gain access to the failover server.
The hacker then proceeded to install RDP connections from the firewall to the failover server, and then deployed a permanent backdoor called "svchost.exe", which is executed daily as part of a scheduled task.
Subsequent access to the network was carried out using a backdoor to avoid detection. The main task of the backdoor is to connect to the C2 server via HTTP and execute arbitrary commands.
Group-IB discovered how an attacker exploits the Veeam vulnerability to enable xp_cmdshell on the backup server and create a fraudulent user account named "VeeamBkp", as well as performs network discovery, enumeration, and collection of credentials using NetScan, AdFind, and NitSoft tools.
The exploit potentially involved an attack originating from the VeeamHax folder on the file server against a vulnerable version of Veeam Backup & Replication installed on the backup server. This activity enabled the activation of the stored procedure " xp_cmdshell "and the subsequent creation of the account"VeeamBkp".
Note that Windows Defender was permanently disabled using DC.exe (Defender Control), after which the ransomware program was downloaded and executed using PsExec.exe. Also, before this, steps were taken to weaken security and move laterally from the AD server to all other servers and workstations using compromised domain accounts.
Source

