Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,081
- Points
- 113
Google, Microsoft, AWS and other major players are subject to large-scale code leaks.
Palo Alto Networks has discovered vulnerabilities in the CI/CD processes of a number of well-known open projects, including those developed by Google, Microsoft, AWS and Red Hat. The problem is related to the leak of GitHub tokens, which can be used to gain unauthorized access to private repositories, steal source code, or inject malware.
Tokens get caught in artifacts due to a combination of several factors: insecure default settings, configuration errors on the part of users, and insufficient security checks at the stage of configuring workflows in GitHub. One of the key elements of the problem was the "actions/checkout" feature that is widely used in GitHub workflows, which clones the repository code, making it available for workflow execution.
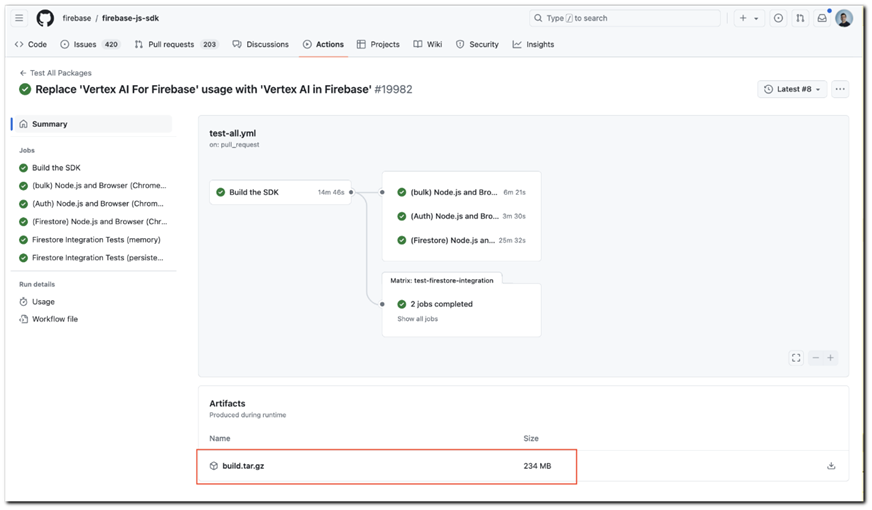
An artifact created by GitHub Actions
By default, the function stores the token in the local directory .git. If the directory is accidentally loaded as an artifact, the token becomes available to outsiders. In addition, the folder may store other sensitive data, such as API keys and access tokens for cloud services.

Publicly Submitted GitHub Token
The problem is compounded by the fact that artifacts generated during the CI/CD process, such as build and test results, can be stored and available for up to 3 months. Another risk is environment variables used in CI/CD pipelines to store GitHub tokens. Such variables can be accidentally written to logs, becoming available through artifacts.
As a result of an attack on leaked tokens, an attacker can exploit various race condition scenarios, trying to extract and use tokens before their expiration date. GitHub tokens are valid for the duration of the workflow, and the ability to use them depends on the specific case. For example, the "Actions_Runtime_Token" token used by GitHub to manage caching and artifacts is usually active for 6 hours, which limits the time for an attack.
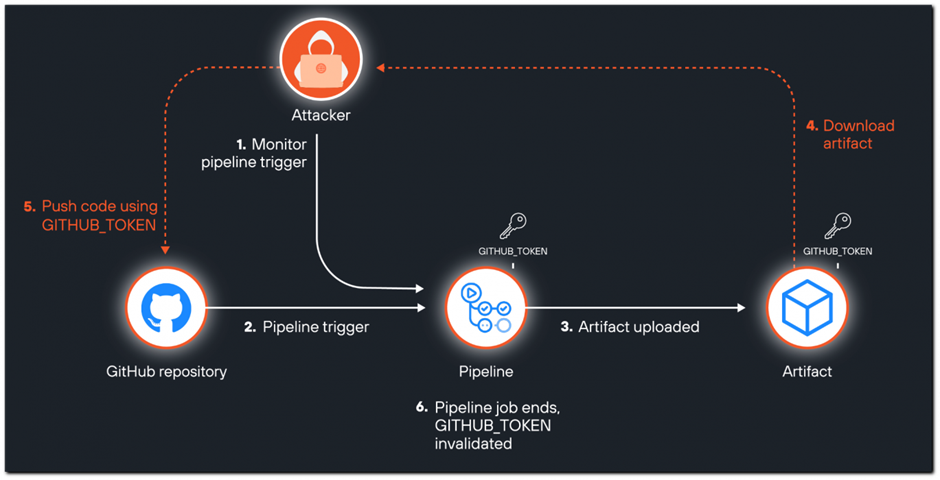
Attack Chain
Palo Alto Networks has identified 14 major open-source projects where tokens were leaked and informed developers. Among the projects are Firebase (Google), OpenSearch Security (AWS), Clair (Red Hat), JSON Schemas (Microsoft) and others.
GitHub users are advised to review the settings of their CI / CD processes, avoid loading entire directories into artifacts, clear logs, and regularly check configurations. It is also important to set the minimum necessary access rights for tokens in order to reduce the risks in the event of their leakage.
Despite the fact that Palo Alto Networks has identified a flaw, the main problems remain unresolved, since GitHub decided not to eliminate the risk, placing the responsibility for protecting artifacts on users. Given the current situation, GitHub users need to understand the risks, assess their vulnerability, and take measures to prevent future leaks.
Users are strongly encouraged to review the settings of their CI/CD pipelines, avoid including entire directories in artifacts, clear logs, and regularly review workflow configurations. You should also change the default settings for actions like "actions/checkout" to prevent storing tokens and other sensitive data. Setting the minimum required access rights for tokens used in workflows will also help reduce possible damage in the event of a leak.
Source
Palo Alto Networks has discovered vulnerabilities in the CI/CD processes of a number of well-known open projects, including those developed by Google, Microsoft, AWS and Red Hat. The problem is related to the leak of GitHub tokens, which can be used to gain unauthorized access to private repositories, steal source code, or inject malware.
Tokens get caught in artifacts due to a combination of several factors: insecure default settings, configuration errors on the part of users, and insufficient security checks at the stage of configuring workflows in GitHub. One of the key elements of the problem was the "actions/checkout" feature that is widely used in GitHub workflows, which clones the repository code, making it available for workflow execution.

An artifact created by GitHub Actions
By default, the function stores the token in the local directory .git. If the directory is accidentally loaded as an artifact, the token becomes available to outsiders. In addition, the folder may store other sensitive data, such as API keys and access tokens for cloud services.

Publicly Submitted GitHub Token
The problem is compounded by the fact that artifacts generated during the CI/CD process, such as build and test results, can be stored and available for up to 3 months. Another risk is environment variables used in CI/CD pipelines to store GitHub tokens. Such variables can be accidentally written to logs, becoming available through artifacts.
As a result of an attack on leaked tokens, an attacker can exploit various race condition scenarios, trying to extract and use tokens before their expiration date. GitHub tokens are valid for the duration of the workflow, and the ability to use them depends on the specific case. For example, the "Actions_Runtime_Token" token used by GitHub to manage caching and artifacts is usually active for 6 hours, which limits the time for an attack.

Attack Chain
Palo Alto Networks has identified 14 major open-source projects where tokens were leaked and informed developers. Among the projects are Firebase (Google), OpenSearch Security (AWS), Clair (Red Hat), JSON Schemas (Microsoft) and others.
GitHub users are advised to review the settings of their CI / CD processes, avoid loading entire directories into artifacts, clear logs, and regularly check configurations. It is also important to set the minimum necessary access rights for tokens in order to reduce the risks in the event of their leakage.
Despite the fact that Palo Alto Networks has identified a flaw, the main problems remain unresolved, since GitHub decided not to eliminate the risk, placing the responsibility for protecting artifacts on users. Given the current situation, GitHub users need to understand the risks, assess their vulnerability, and take measures to prevent future leaks.
Users are strongly encouraged to review the settings of their CI/CD pipelines, avoid including entire directories in artifacts, clear logs, and regularly review workflow configurations. You should also change the default settings for actions like "actions/checkout" to prevent storing tokens and other sensitive data. Setting the minimum required access rights for tokens used in workflows will also help reduce possible damage in the event of a leak.
Source

