Carding 4 Carders
Professional
Customers of online stores have already tried out a new method of stealing funds.
Cybersecurity researchers from the Akamai Security Intelligence Group have discovered a new campaign for skimming Magecart maps. Attackers use 404 error pages on online store sites to place malicious code that steals customer credit card data.
Experts note that this technique is one of three variants that were noticed during the campaign. The other two methods of attack are to hide the code in the "onerror" attribute of the HTML tag of the image and in the binary image, which makes it look like a fragment of the code of the Meta* Pixel tracking pixel.
The campaign is focused on sites running on the Magento and WooCommerce platforms. Some of the affected sites are linked to well-known organizations in the food and retail sectors.
Note that all websites have 404 error pages that are displayed to users when they try to access a page that doesn't exist, has been moved, or has a broken link. The Magecart grouping uses the standard "404 Not Found" page to hide and download malicious code, which is an innovation compared to previous campaigns.
By manipulating the standard 404 error page on the target site, cybercriminals gain various opportunities to improve their concealment and evasion of detection. Malicious code is either disguised as a Meta Pixel code snippet, or hidden in random embedded scripts that are already present on the compromised checkout page. The Magecart loader initiates a request to a relative path named "icons", which does not exist on the site, which is why the request returns the error "404 Not Found".
At first, the researchers assumed that the skimmer was no longer active or that the Magecart team had made a configuration error. However, upon closer inspection, it was found that the loader contains a regular expression that searches for a specific string in the returned HTML code of the 404 page.
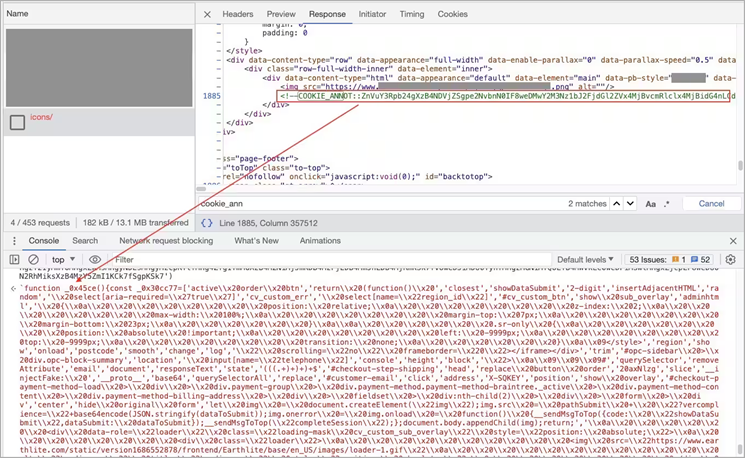
String that the loader looks for in HTM L
Having found the necessary string on the page, the experts found a "glued" string (concatenation) in base64 format, hidden in the comment. Decoding the string revealed a JavaScript skimmer that is hidden on all 404 pages. The skimmer code displays a fake form that site visitors are asked to fill out, including the credit card number, expiration date, and CVV code.
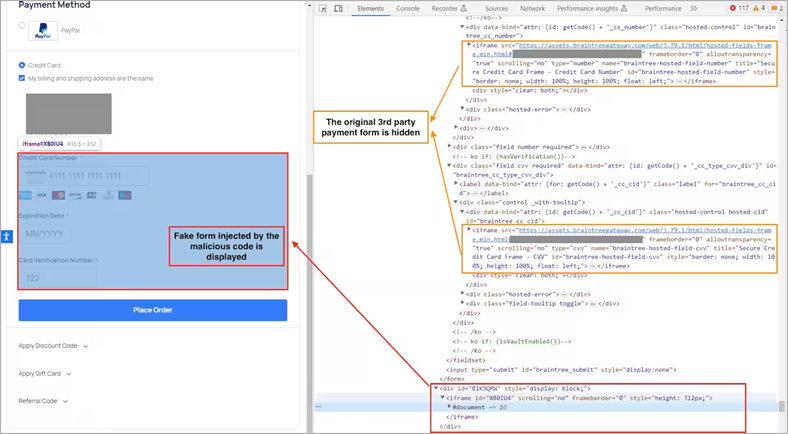
Fake card data entry form
After entering data in a fake form, the victim receives the "session timeout" error. At this point, all data is encoded in base64 format in the background and sent to attackers. And in such a way that it looks like a normal request to get an image from a website. This is done in order to deceive security systems that monitor suspicious activity on the network. Attackers use base64 encoding to hide the real meaning of the sent data, making it invisible to security systems.
This case of manipulating 404 pages highlights the evolution of tactics and versatility of Magecart hackers, who continue to make it harder for website administrators to detect malicious code on compromised sites and clean them up.
Cybersecurity researchers from the Akamai Security Intelligence Group have discovered a new campaign for skimming Magecart maps. Attackers use 404 error pages on online store sites to place malicious code that steals customer credit card data.
Experts note that this technique is one of three variants that were noticed during the campaign. The other two methods of attack are to hide the code in the "onerror" attribute of the HTML tag of the image and in the binary image, which makes it look like a fragment of the code of the Meta* Pixel tracking pixel.
The campaign is focused on sites running on the Magento and WooCommerce platforms. Some of the affected sites are linked to well-known organizations in the food and retail sectors.
Note that all websites have 404 error pages that are displayed to users when they try to access a page that doesn't exist, has been moved, or has a broken link. The Magecart grouping uses the standard "404 Not Found" page to hide and download malicious code, which is an innovation compared to previous campaigns.
By manipulating the standard 404 error page on the target site, cybercriminals gain various opportunities to improve their concealment and evasion of detection. Malicious code is either disguised as a Meta Pixel code snippet, or hidden in random embedded scripts that are already present on the compromised checkout page. The Magecart loader initiates a request to a relative path named "icons", which does not exist on the site, which is why the request returns the error "404 Not Found".
At first, the researchers assumed that the skimmer was no longer active or that the Magecart team had made a configuration error. However, upon closer inspection, it was found that the loader contains a regular expression that searches for a specific string in the returned HTML code of the 404 page.

String that the loader looks for in HTM L
Having found the necessary string on the page, the experts found a "glued" string (concatenation) in base64 format, hidden in the comment. Decoding the string revealed a JavaScript skimmer that is hidden on all 404 pages. The skimmer code displays a fake form that site visitors are asked to fill out, including the credit card number, expiration date, and CVV code.

Fake card data entry form
After entering data in a fake form, the victim receives the "session timeout" error. At this point, all data is encoded in base64 format in the background and sent to attackers. And in such a way that it looks like a normal request to get an image from a website. This is done in order to deceive security systems that monitor suspicious activity on the network. Attackers use base64 encoding to hide the real meaning of the sent data, making it invisible to security systems.
This case of manipulating 404 pages highlights the evolution of tactics and versatility of Magecart hackers, who continue to make it harder for website administrators to detect malicious code on compromised sites and clean them up.
