Encryption is uncompromising
Analyst report from the Electronic Frontier Foundation (EFF) on crypto regulation trends: officials want access to encrypted information to catch intruders, even if it endangers bona fide users
The topic of encryption is again on everyone's lips, as US officials insist on compromising the IT security of users, leaving loopholes for law enforcement in encryption systems. These opponents of encryption suggest that a "sweet spot" is possible: use strong encryption with "exclusive access" for decryption for law enforcement. They argue that tech companies are creating a world in which people can commit crimes without fear of detection.
Despite this new rhetoric, most experts are still unanimous that “exclusive access”, independently implemented, weakens security. The terminology may have changed, but the crux of the matter is not: Should tech companies create a system that inherently hurts their users? The answer, too, has not changed - no.
Let's count the reasons why.
- First, if authorized by the government, it would violate the First Amendment [to the US Constitution] in accordance with the “forced speech” doctrine, which prohibits the government from coercing an individual, company, or organization to disclose any information.
- Second, forcing tech companies to weaken encryption security puts users at risk. In the 1990s, the White House introduced the Clipper chip, which supports the backdoor in the encryption system. AT&T security researcher Matt Blaze discovered huge security flaws in the system, showing that a brute-force attack could compromise technology.
- Third, “exclusive access” can hurt US businesses and chill innovation. The US government cannot stop the development of encryption technologies; he can simply "squeeze" him out of the border.
- Finally, exclusive access does not work in crime prevention. Regardless of the government's requirements for US companies, high-tech criminals can still obtain strong encryption outside the US.
Safe backdoor is an oxymoron
Despite consensus among IT experts, some policymakers continue to seek an impossible middle ground. Last month, after years of research, the US National Academy of Sciences released a report on encryption and "exclusive access" that narrowed down the question "should a government require" exclusive access "to the content of encrypted messages? to the question "how can the government demand this without compromising user safety?" Cryptanalyst Susan Landau expressed concern that some might misinterpret the report as evidence that the idea of "exclusive access" is close to technical implementation:
“The Academy report discusses approaches to 'building ... secure systems' that provide 'exceptional access', but these are just initial approaches ... The presentations to the Academy committee were brief descriptions of the ideas of three specialist scientists, not detailing the architecture and operation of such systems. There is a huge difference between the sketch and the actual implementation - Leonardo da Vinci's drawings for a flying car are different from the Wright brothers' plane launched at Kitty Hawk. "
Research is carried out not only at the Academy. Last month, the international research institute EastWest Institute published a report proposing "two balanced and risk-sensitive policies to support a more constructive dialogue."
Finally, last week, Wired magazine ran an article on former Microsoft CTO Ray Ozzie as he tried to find an exclusive phone access model that would satisfy "both law enforcement and privacy advocates." While Ozzy may have been well-meaning, experts Matt Green, Steve Bellovin, Matt Blaze, Rob Graham and others quickly pointed out the significant flaws in his idea. No system is perfect, and a backdoor system designed for billions of phones has a huge cost of error.
The rethinking of the problem continues, but the truth remains. All attempts at "constructive dialogue" neglect one of the main obstacles: the starting point for this dialogue is diametrically opposed to the very purpose of encryption. To understand why, read on.
Encryption: Keys User's Guide
Encryption is often described using a key analogy - anyone with a “key” can decrypt or read information that is “private”. But if we go back, we can see problems with this metaphor.
In ancient times, encryption was achieved using sets of instructions that we now call "symmetric encryption". The instructions explain both how to disguise and how to decrypt the message.
For encryption, sometimes simple rules were used, for example, when entering alphanumeric text, replace each letter or number with the next alphabetically or counting, so "A" becomes "B", "B" becomes "C", etc. Sometimes more complex rules were applied, such as translating the letters of the message into numbers, and then converting those numbers using a mathematical formula to obtain a new string of numbers, which, while the cipher is unknown, is unreadable to the uninitiated.
As encryption developed, cryptographers began to use "keys" to provide greater security. The "key" was the secret information known to both the sender and the addressee, necessary to encrypt and decrypt messages.
"Keys" still play an important role in modern encryption, but more than one type of key is commonly used.
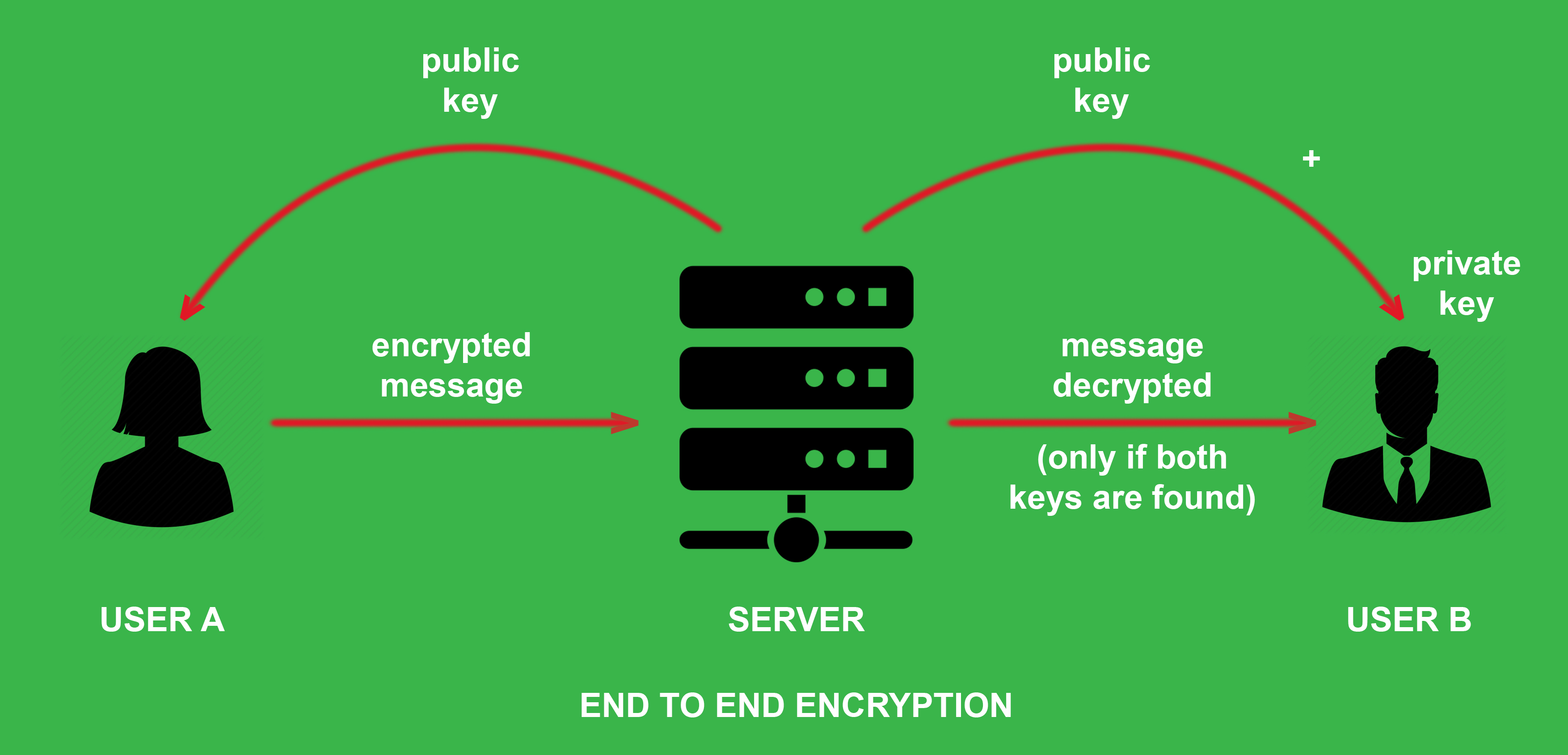
Some digital devices encrypt stored data, and the entered password for device operation unlocks a random key used to encrypt this data. But for communications between people, such as emails or chats, "public key encryption" is used. The advantage of this form of encryption is that the people who are communicating do not need to know the "key" in advance.
With public key encryption, a user, who can be a person or an organization - for example, a company, website, or network server - is given two (sometimes more) associated keys. This is usually a key for encrypting data and a key for decrypting data. The key that encrypts the data is called the "public key" and can be exchanged with anyone. It looks like an open instruction set. Anyone who wants to send encrypted messages to a person can use their set of open instructions to encrypt data according to these rules. The second key is called the "private key" and is never published. This private key decrypts data that has been encrypted using the corresponding public key.
In modern encryption, public and private keys are not used for messages by themselves. They are used to encrypt and decrypt a single key that both encrypts and decrypts data. This separate key is called a "session key" and is used with traditional symmetric encryption as a secret instruction set that can be used by both the sender and receiver of a message to encrypt and decrypt the message.
Public key encryption ensures that the session key is secure and cannot be intercepted and used by outsiders. Private keys keep session keys secret, which protect the secret of encrypted messages. The fewer opportunities to steal or accidentally publish a private key, the higher the security.
But “exclusive access” requires just that - more keys, more access, and more vulnerability. "Exclusive access" essentially undermines the security of encryption by providing law enforcement agencies with either their own set of private keys for each encrypted device and the private key that sends and receives encrypted messages, or requires duplicate keys to be created and stored securely for transmission ...
Therefore, the proposals of law enforcement agencies for a "responsible decision" are irresponsible. Any system that includes a separate channel for the other party to access is inherently less secure than a system that does not have that channel. In encryption systems, the very existence of duplicate or separate target keys makes these keys attractive to attackers. This is similar to creating duplicate physical keys for a bank vault - the risk of one of these keys being lost or stolen is quite high. Copying the encryption key (for law enforcement in the US and subsequently around the world) increases the risk.
There is no good faith compromise in the government's request for “exclusive access”. The middle ground between what law enforcement wants (bad encryption) and what users want (good encryption) is still just bad encryption.
US Deputy Attorney General Rod Rosenstein admitted in an interview with Politico that a device with exclusive access "will be less secure than a product that does not have this ability." He continued: "The logical question is: how much risk are we willing to take on because of this?" The answer to this question must be built on ironclad arguments about the risks of moving away from strong encryption.
Common sense must combat the populist rhetoric of politicians.
The translation was prepared by Evgeniya Hotovitskaya based on EFF materials