The new version of the PlugX virus is testing the strength of systems in the Asian region.
A new report from Trend Micro revealed that the Chinese Mustang Panda group has stepped up its attacks on Asian countries using a modified version of the PlugX virus called DOPLUGS. The new version differs from the previous ones in the presence of unique features and is intended primarily for downloading the main virus.
The main targets of the attacks were Taiwan and Vietnam, and to a lesser extent Hong Kong, India, Japan, Malaysia, Mongolia and China. The decimation chain begins with sending phishing messages, through which the payload of the first stage is delivered. This load, displaying a fake document on the victim's screen, unpacks a signed executable file vulnerable to DLL Sideloading in the background to load a malicious DLL that runs PlugX.
The PlugX malware then delivers the Remote Access Trojan (RAT) Poison Ivy or Cobalt Strike Beacon to establish a connection to the Command and Control server (C2).
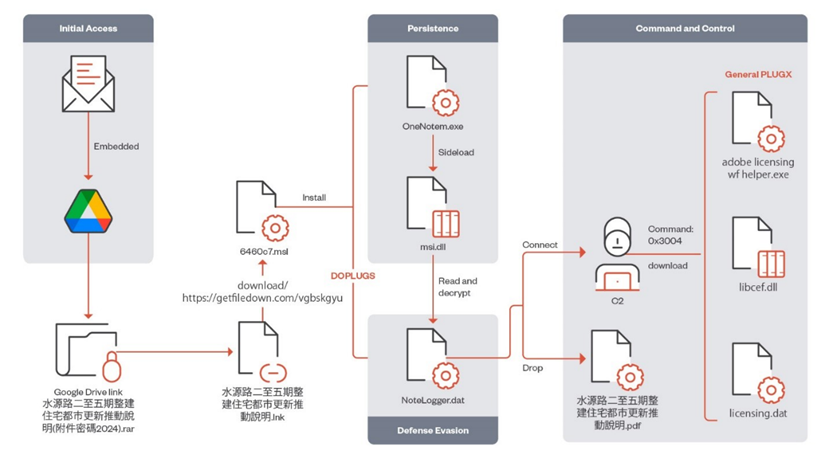
DOPLUGS infection Chain
DOPLUGS is a loader with four control commands, one of which is designed to load the standard version of the PlugX virus. Trend Micro also identified samples of DOPLUGS integrated with the KillSomeOne module, which is responsible for spreading malware, collecting information, and stealing documents from USB drives.
PlugX (also known as Korplug) is a modular implant that is installed after an exploit and is known for its many features, including data exfiltration and the ability to use a compromised machine for malicious purposes.
One of the key methods used by PlugX is the DLL Sideloading technique, which consists of downloading a malicious DLL library from a digitally signed software application. A valid digital signature can confuse some security tools, allowing hackers to remain undetected, maintain resilience, elevate privileges, and bypass file execution restrictions.
A new report from Trend Micro revealed that the Chinese Mustang Panda group has stepped up its attacks on Asian countries using a modified version of the PlugX virus called DOPLUGS. The new version differs from the previous ones in the presence of unique features and is intended primarily for downloading the main virus.
The main targets of the attacks were Taiwan and Vietnam, and to a lesser extent Hong Kong, India, Japan, Malaysia, Mongolia and China. The decimation chain begins with sending phishing messages, through which the payload of the first stage is delivered. This load, displaying a fake document on the victim's screen, unpacks a signed executable file vulnerable to DLL Sideloading in the background to load a malicious DLL that runs PlugX.
The PlugX malware then delivers the Remote Access Trojan (RAT) Poison Ivy or Cobalt Strike Beacon to establish a connection to the Command and Control server (C2).

DOPLUGS infection Chain
DOPLUGS is a loader with four control commands, one of which is designed to load the standard version of the PlugX virus. Trend Micro also identified samples of DOPLUGS integrated with the KillSomeOne module, which is responsible for spreading malware, collecting information, and stealing documents from USB drives.
PlugX (also known as Korplug) is a modular implant that is installed after an exploit and is known for its many features, including data exfiltration and the ability to use a compromised machine for malicious purposes.
One of the key methods used by PlugX is the DLL Sideloading technique, which consists of downloading a malicious DLL library from a digitally signed software application. A valid digital signature can confuse some security tools, allowing hackers to remain undetected, maintain resilience, elevate privileges, and bypass file execution restrictions.
