Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,038
- Points
- 113
Microsoft spoke about the tactics of intruders who start hunting on the eve of the holidays.
Microsoft published a new Cyber Signals report, in which it shared fresh data on the activities of the Storm-0539 hacker group and a sharp increase in gift card theft on the eve of Memorial Day in the United States.
In a new Cyber Signals report, Microsoft confirms that attackers are targeting organizations that issue gift cards, not end users. The report also points to widespread abuse of cloud services to reduce the cost of operations.
Microsoft notes that attackers are becoming more active before major holidays: during Christmas last year, Storm-0539 activity increased by 60%, and from March to May 2024, there was a noticeable increase of 30%.
Working methods of Storm-0539
After gaining access to the target environment using stolen credentials, hackers register their devices with the company's MFA services to preserve access. They then move around the network, compromising VMs, VPNs, SharePoint, OneDrive, Salesforce, and Citrix.
Eventually, Storm-0539 gains access to credentials that allow them to create new gift cards for subsequent sale on the darknet, in stores, or cashed out via cash mules.
Companies usually set a limit on the amount of a single gift card. For example, if the limit is $100,000, attackers create a $99,000 card, send themselves the card code, and cash it out. The main motivation of hackers is to steal gift cards and sell them cheaper. In some cases, the attackers stole up to $100,000 a day from some companies, as Microsoft explains.
To create a new infrastructure, cybercriminals create websites that mimic charities in order to register with cloud service providers. Accounts use pay-as-you-go pricing plans or free trial versions, abusing such rates for large-scale operations with minimal costs.
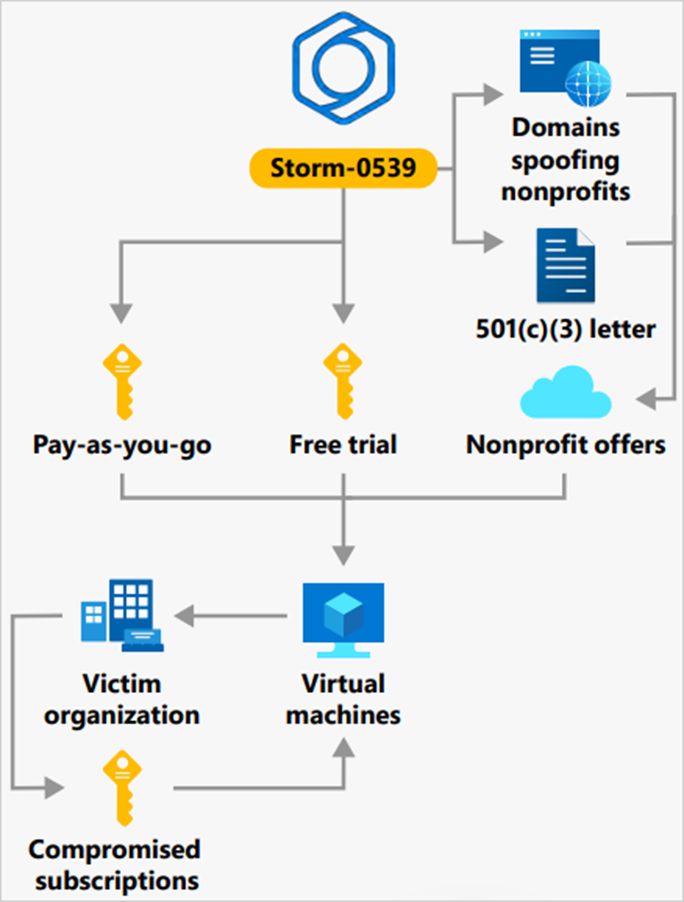
Storm-0539 Attack Chain
Security recommendations
Microsoft advises gift card portal operators to constantly monitor anomalies and implement conditional access policies that would prevent the possibility of creating an unusually large number of cards with a single account.
In addition, organizations are encouraged to implement token reuse protection measures, adhere to the principle of least privilege, and use FIDO2 security keys to protect high-risk accounts. Sellers can also play an important role in disrupting the profit chain of Storm-0539 and similar attackers by recognizing and rejecting orders with suspicious signs.
Although the attacks do not affect shoppers, Internet users preparing for the holidays should exercise increased caution against fraud, fake stores, and malicious advertising.
Storm-0539 is a financially motivated hacker group from Morocco that has been active since 2021 and specializes in gift and payment card fraud. Cybercriminals are known for their intelligence activities and specially created phishing emails and SMS messages aimed at employees of organizations that issue gift cards.
Microsoft published a new Cyber Signals report, in which it shared fresh data on the activities of the Storm-0539 hacker group and a sharp increase in gift card theft on the eve of Memorial Day in the United States.
In a new Cyber Signals report, Microsoft confirms that attackers are targeting organizations that issue gift cards, not end users. The report also points to widespread abuse of cloud services to reduce the cost of operations.
Microsoft notes that attackers are becoming more active before major holidays: during Christmas last year, Storm-0539 activity increased by 60%, and from March to May 2024, there was a noticeable increase of 30%.
Working methods of Storm-0539
After gaining access to the target environment using stolen credentials, hackers register their devices with the company's MFA services to preserve access. They then move around the network, compromising VMs, VPNs, SharePoint, OneDrive, Salesforce, and Citrix.
Eventually, Storm-0539 gains access to credentials that allow them to create new gift cards for subsequent sale on the darknet, in stores, or cashed out via cash mules.
Companies usually set a limit on the amount of a single gift card. For example, if the limit is $100,000, attackers create a $99,000 card, send themselves the card code, and cash it out. The main motivation of hackers is to steal gift cards and sell them cheaper. In some cases, the attackers stole up to $100,000 a day from some companies, as Microsoft explains.
To create a new infrastructure, cybercriminals create websites that mimic charities in order to register with cloud service providers. Accounts use pay-as-you-go pricing plans or free trial versions, abusing such rates for large-scale operations with minimal costs.

Storm-0539 Attack Chain
Security recommendations
Microsoft advises gift card portal operators to constantly monitor anomalies and implement conditional access policies that would prevent the possibility of creating an unusually large number of cards with a single account.
In addition, organizations are encouraged to implement token reuse protection measures, adhere to the principle of least privilege, and use FIDO2 security keys to protect high-risk accounts. Sellers can also play an important role in disrupting the profit chain of Storm-0539 and similar attackers by recognizing and rejecting orders with suspicious signs.
Although the attacks do not affect shoppers, Internet users preparing for the holidays should exercise increased caution against fraud, fake stores, and malicious advertising.
Storm-0539 is a financially motivated hacker group from Morocco that has been active since 2021 and specializes in gift and payment card fraud. Cybercriminals are known for their intelligence activities and specially created phishing emails and SMS messages aimed at employees of organizations that issue gift cards.

