Man
Professional
- Messages
- 3,222
- Reaction score
- 1,199
- Points
- 113
How a 0day vulnerability in Chrome became the key to other people's wealth.
The North Korean Lazarus group used a zero-day vulnerability in the Google Chrome browser to steal cryptocurrency under the guise of a malicious online game. This was announced by Kaspersky Lab experts at the Security Analyst Summit 2024 in Bali.
The attackers created a tank-game website, promising users cryptocurrency rewards to attract them to the platform and infect devices.
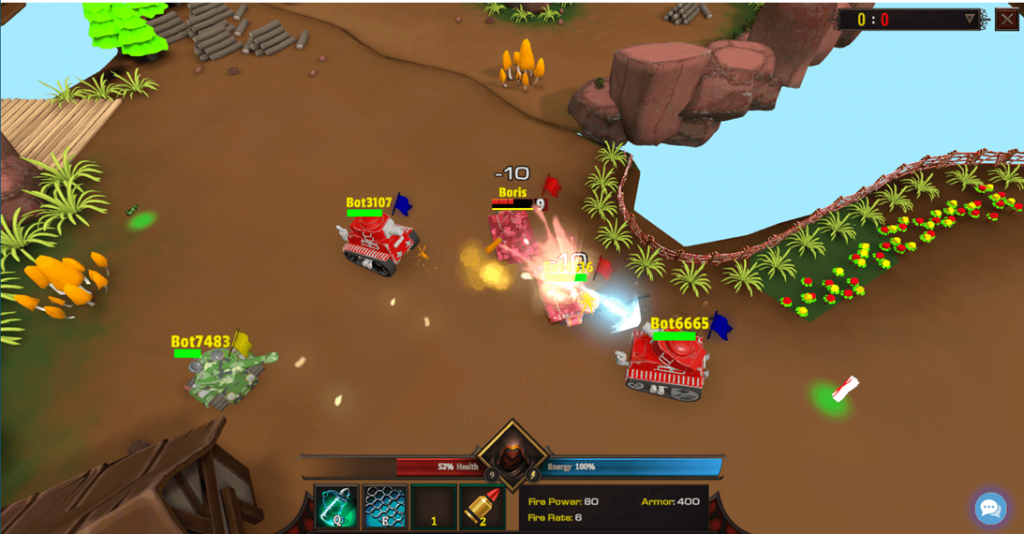
The campaign turned out to be carefully thought out. For several months, cybercriminals have been promoting the game through international social networks, using images generated by neural networks, and attracting crypto influencers for advertising.

Kaspersky Lab experts found that the malicious game copied an existing project and almost all of its source code, only slightly changing the logos and visual design. It is noteworthy that shortly after the launch of the campaign, the developers of the original game reported the theft of 20 thousand dollars in cryptocurrency from their wallet.
The malicious Lazarus site hid an exploit for Chrome that exploited two vulnerabilities. One of them was previously unknown — a bug in the V8 JavaScript engine and WebAssembly allowed attackers to gain full control over the device by bypassing defense mechanisms and performing malicious actions. To infect the device, it was enough just to go to the site without even launching the game.
Kaspersky Lab researchers reported Google's problem in a timely manner. As a result, the vulnerability, which received the identifier CVE-2024-4947, was fixed, and the malicious site was blocked. The second vulnerability used in the campaign did not receive a CVE designation, but was also fixed.
Lazarus is known for its specialization in zero-day vulnerability attacks, which require significant resources and time. The Manuscrypt backdoor used in this operation was used by the group in more than 50 previous attacks targeting various organizations around the world.
Boris Larin of Kaspersky Lab noted that Lazarus goes beyond standard methods, using full-fledged gaming projects to infect devices as a cover. Such large-scale preparation indicates the group's ambitious plans and high risks for users and organizations around the world.
Source
The North Korean Lazarus group used a zero-day vulnerability in the Google Chrome browser to steal cryptocurrency under the guise of a malicious online game. This was announced by Kaspersky Lab experts at the Security Analyst Summit 2024 in Bali.
The attackers created a tank-game website, promising users cryptocurrency rewards to attract them to the platform and infect devices.

The campaign turned out to be carefully thought out. For several months, cybercriminals have been promoting the game through international social networks, using images generated by neural networks, and attracting crypto influencers for advertising.

Kaspersky Lab experts found that the malicious game copied an existing project and almost all of its source code, only slightly changing the logos and visual design. It is noteworthy that shortly after the launch of the campaign, the developers of the original game reported the theft of 20 thousand dollars in cryptocurrency from their wallet.
The malicious Lazarus site hid an exploit for Chrome that exploited two vulnerabilities. One of them was previously unknown — a bug in the V8 JavaScript engine and WebAssembly allowed attackers to gain full control over the device by bypassing defense mechanisms and performing malicious actions. To infect the device, it was enough just to go to the site without even launching the game.
Kaspersky Lab researchers reported Google's problem in a timely manner. As a result, the vulnerability, which received the identifier CVE-2024-4947, was fixed, and the malicious site was blocked. The second vulnerability used in the campaign did not receive a CVE designation, but was also fixed.
Lazarus is known for its specialization in zero-day vulnerability attacks, which require significant resources and time. The Manuscrypt backdoor used in this operation was used by the group in more than 50 previous attacks targeting various organizations around the world.
Boris Larin of Kaspersky Lab noted that Lazarus goes beyond standard methods, using full-fledged gaming projects to infect devices as a cover. Such large-scale preparation indicates the group's ambitious plans and high risks for users and organizations around the world.
Source

