Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
The authorities took a creative approach to disclosing information about actions against the group.
Law enforcement agencies dealt a powerful blow to cybercrime by neutralizing the infrastructure of LockBit, one of the most dangerous groups involved in the distribution of extortionate software. As part of Operation Cronos, the LockBit data leak site was taken under control, which was turned into a platform for exposing the actions of criminals.

Europol's summary of Operation Kronos
The site, which was previously used to publish victims ' data, now publishes information about the progress of the investigation. The UK authorities, represented by the National Crime Agency (NCA), coordinated the disclosure of information. The converted site has retained its original format, but now, instead of threats and ransom demands, each post is dedicated to new facts about the group's activities. One of the posts on the site promises to reveal the identity of the LockBit leader by the end of the week.
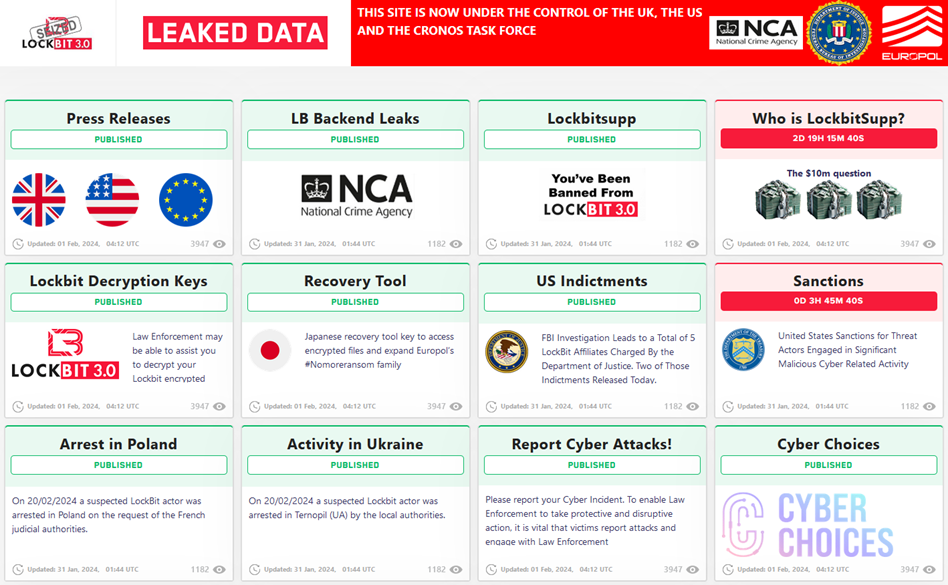
Police records on the LockBit leak
The key point is the arrest of two LockBit affiliates in Ukraine and Poland, which is a continuation of a series of arrests that began earlier in the United States and Canada. Those arrested are accused of developing and distributing the LockBit malware. Also, the US Department of Justice accused Artur Sungatov and Ivan Kondratiev of attacking targets in the United States using the LockBit ransomware program.
In addition to the arrests, more than 200 cryptocurrency accounts were frozen and decryption keys were seized for more than 1,000 cases of infection, which was a significant blow to LockBit's operations. Servers in the Netherlands, Germany, Finland, France, Switzerland, Australia, the United States, and the United Kingdom that were used to distribute malware were also seized.
An important part of the operation was to gain control over the source code of the LockBit platform and collect intelligence about the group's activities. The collected data will allow law enforcement agencies not only to pursue members of the group, but also to help victims regain access to their data. To do this, decryption keys will be available on a special portal.
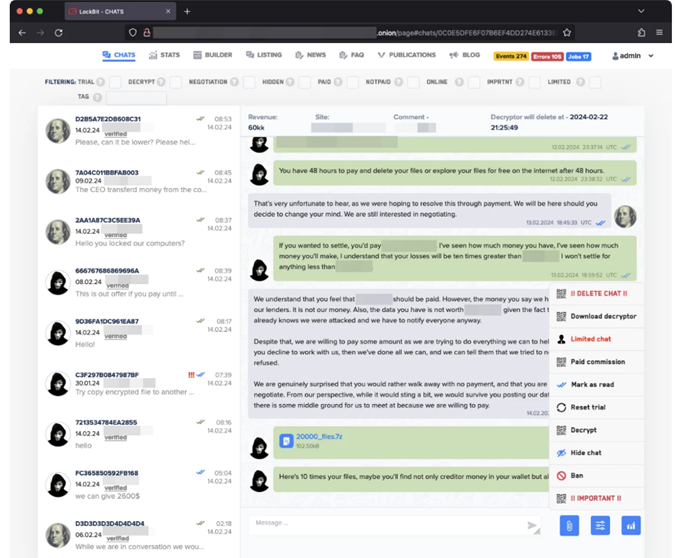
Captured LockBit Partner Portal
The NCA said that the work on countering LockBit will not end there. Law enforcement agencies will continue to track and prosecute members of LockBit and other cybercrime groups. The NCA also emphasizes that the authorities know who is behind LockBit's activities and how they operate, which will effectively counter attempts to restore the group's activities.
It is expected that more information about LockBit will be published during the week, including data on partners, infrastructure, and technical reports from leading information security companies. The revelations will be an important step in the fight against cybercrime, demonstrating the readiness and ability of the international community to counter threats in cyberspace.
Law enforcement agencies dealt a powerful blow to cybercrime by neutralizing the infrastructure of LockBit, one of the most dangerous groups involved in the distribution of extortionate software. As part of Operation Cronos, the LockBit data leak site was taken under control, which was turned into a platform for exposing the actions of criminals.

Europol's summary of Operation Kronos
The site, which was previously used to publish victims ' data, now publishes information about the progress of the investigation. The UK authorities, represented by the National Crime Agency (NCA), coordinated the disclosure of information. The converted site has retained its original format, but now, instead of threats and ransom demands, each post is dedicated to new facts about the group's activities. One of the posts on the site promises to reveal the identity of the LockBit leader by the end of the week.

Police records on the LockBit leak
The key point is the arrest of two LockBit affiliates in Ukraine and Poland, which is a continuation of a series of arrests that began earlier in the United States and Canada. Those arrested are accused of developing and distributing the LockBit malware. Also, the US Department of Justice accused Artur Sungatov and Ivan Kondratiev of attacking targets in the United States using the LockBit ransomware program.
In addition to the arrests, more than 200 cryptocurrency accounts were frozen and decryption keys were seized for more than 1,000 cases of infection, which was a significant blow to LockBit's operations. Servers in the Netherlands, Germany, Finland, France, Switzerland, Australia, the United States, and the United Kingdom that were used to distribute malware were also seized.
An important part of the operation was to gain control over the source code of the LockBit platform and collect intelligence about the group's activities. The collected data will allow law enforcement agencies not only to pursue members of the group, but also to help victims regain access to their data. To do this, decryption keys will be available on a special portal.

Captured LockBit Partner Portal
The NCA said that the work on countering LockBit will not end there. Law enforcement agencies will continue to track and prosecute members of LockBit and other cybercrime groups. The NCA also emphasizes that the authorities know who is behind LockBit's activities and how they operate, which will effectively counter attempts to restore the group's activities.
It is expected that more information about LockBit will be published during the week, including data on partners, infrastructure, and technical reports from leading information security companies. The revelations will be an important step in the fight against cybercrime, demonstrating the readiness and ability of the international community to counter threats in cyberspace.






