Carding Forum
Professional
Not for all audiences, but very informative and interesting reading.
An anonymous, offline, peer-to-peer file-sharing network with free access first appeared during the Cold War, which was launched by the United States and the Soviet Union. Typically, Hollywood spy films have treated us to stories of shooting pens, exotic locations, and scheming double agents. But real intelligence is often much more mundane. And caches are a great example of this. The simple, unexciting, but extremely effective method of network file sharing can be an excellent tool for more secretive communication.
The idea of creating undetectable communication paths, originally intended for agents to transmit government secrets, can also be effectively used in another scenario.
Imagine finding yourself in a less developed part of the world, where the internet signal is weak and the postal service is either unreliable or non-existent. In this case, a pre-arranged method of communicating messages to a local contact and receiving responses from him can be a good help. The risk of the message being intercepted by criminal elements or corrupt local authorities will also be minimized.
If there is a local or regional disruption to daily life, such as a large-scale power outage or natural disaster that short-circuits communication lines, you can use a USB drive to send messages to your neighbors and loved ones. You can also design a special “dead drops” hiding place for emergencies as a means of family communication. Of course, each family member should know its location, as well as the signs and marking methods to notify household members of the arrival of a new message, and when one of them sees the corresponding signal, then he is obliged to check the “mailbox "
Planning
Unlike a dead drop, which is called a “dead spot,” there is also a “live spot.” In intelligence parlance, this is when two people meet in person to exchange information or materials face to face. In spy movies, a live contact goes something like this: Agent #1 sits down at a table in a cafe and places his briefcase on the floor under the table. A few minutes later, Agent #2 sits down across from him. After drinking a cup of coffee and chatting about the weather, Agent #2 takes the briefcase and both people leave.
Deadlock is when two agents never, under any circumstances, come into direct contact to transmit information. The parties involved must establish two things in advance: the location of the cache and the signaling pointer. Such a point would obviously be where the message or information would be left for the other party and where it could be identified. Recognition points must be selected taking into account the circumstances. If you need to go to a certain place at a certain time, you need to be able to justify your presence there in case you are asked about it.

Note
The pointer is usually located at a distance from the bookmark location. It is a kind of signal, usually visual, indicating that a message has already been delivered to a pre-agreed location.
If the chalk lines on a mailbox don't inspire you, a sign could be a ribbon tied around a specific tree in your yard. Or a piece of chewing gum stuck to the recipient's windshield. The possibilities are endless, and you and your partner can always agree on exactly what the sign is and where it should be placed.


Mark on the corner of the window
On the other hand, you can completely abandon the use of signals and marks. In this case, the stash site will simply be checked on a regular schedule. When using this method, precautions should be taken to ensure that regularly scheduled site inspection trips do not stand out from your normal daily activities. For example, use the time to walk the dog in the park near your home. Every morning you get up early and walk the dog before going to work. You might agree, for example, that the designated location will be the underside of the green bench on the northeast side of this park, and that you will check it every Wednesday at 7:45 am. Since you are in this place all the time and this time is part of your daily morning exercise, and since this park is where you have a favorite bench for relaxing on Wednesday mornings, it is much less likely that casual (or not so casual) Observers will become suspicious. or other dog owners.
Implementation
When leaving information in a designated location, you can install either a hidden or overt cache. A hidden cache is intentionally hidden from view and must be retrieved skillfully. An overt cache is disguised using everyday objects and has contextual camouflage to be “hidden in plain sight.”
As an example, these metal pegs, painted black and hollow inside, in which a note, documents, or money are left, can be easily stuck into the ground and just as easily removed.
The item that is most often associated with the concept of “dead drops” is the “drop spike”. Although it is not as common as in past eras, it can still be found. The option in the photo above is from ITS Tactical products. It is a hollow steel spike with a threaded cap on the flat end. Simply unscrew the cap, place your message or items inside and screw it on. The model even has a rubber gasket on the lid to protect the contents from moisture. Once sealed, the pin can be stuck into the ground for the recipient to pull out later.

Open dead drop capsules can be almost any size or shape, as long as they allow you to transfer data. Several specialized tools are also available for this task. For example, Dead Drop Spike ITS also sells a hollow spy bolt. It is a real steel bolt with a head that can be removed to access its hollow body.


Hollow coins can be used in the same way. During the Cold War, they were used to hide small microfilm slides. And today, for example, micro SD cards or SIM cards can be placed there.
If you don't have the special tools, there are plenty of ways to disguise dead drop containers. Hidden media can be found stuck under a park bench, a trash barrel, or inside a toilet paper dispenser in a public restroom. Over hiding places can be functionally simple. A USB drive, for example, can be placed inside an empty soda can and left as trash. Just be careful. Be mindful of where you put your storage device and how long it stays there before being retrieved. The old soda can USB stick trick goes awry very quickly if some eco-conscious citizen decides to recycle your trash.



If there is no desire or extra funds for specialized items, then even ordinary items that are essentially garbage (for example, like this cola can) are perfect for storing flash drives.
In the past, messages were transmitted on handwritten notes. Now, information in documents can be compressed down to microdots. However, to hide a folded sheet of paper or film, your “spy tools” had to be quite large. And while USB drives and SD cards are not very large, they are still larger than a piece of note paper. You will need to plan your dead drop and organize it according to the size of the media you need to transmit via dead drops.
There is also an inherent risk that your bookmark will be found by someone other than the intended recipient. This is why it is vital and necessary to know both your position and the method of cover. If possible, consider "testing" the location of the cache. Leave a distracting object and see if a passing stranger notices it. And if you use digital media, you can also use passwords or encrypt files.
From a security standpoint, there are two main things to consider. One is the possibility of being seen while setting up or retrieving the dead drop. If someone witnesses you setting up the dead drop, especially if the same person sees you more than once, it can quickly arouse curiosity or suspicion. Can you prepare a convincing story about what you are doing in that location at that hour? Is the information you are transmitting illegal? The other consideration is that if your dead drop is discovered by a third party, they could use the information against you or your partner. In some ways, this may be a problem, in other ways it is not. It depends on what you are primarily using the dead drop for. Still, it is something to think about.
CIA Covert Communications Signals
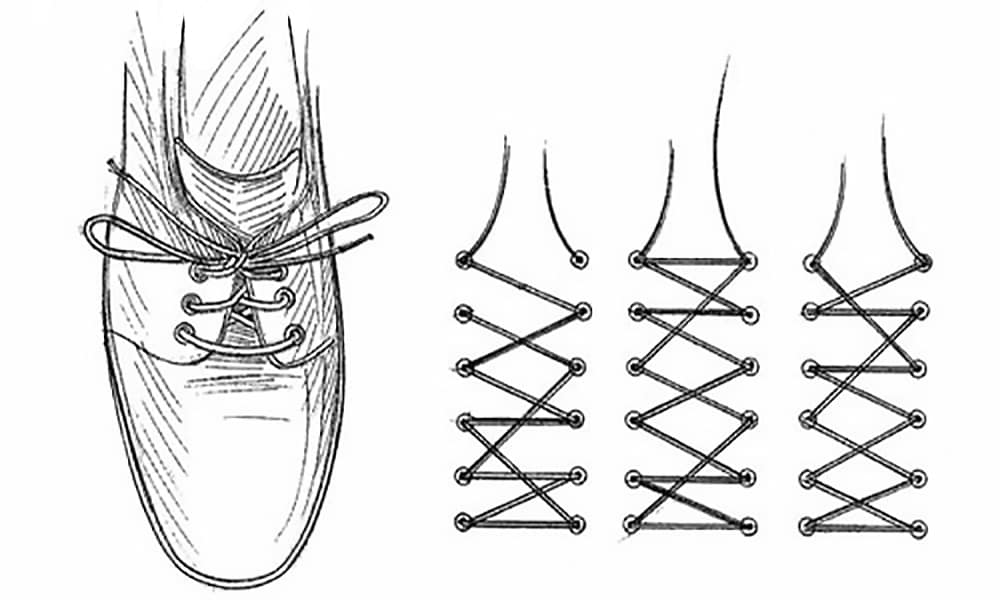
During the Cold War, CIA agents operating behind the Iron Curtain are reported to have used several clever visual cues to communicate with their contacts. Some of these were documented by Robert Parker in his book The Cold War Spy's Pocket Guide. For example, agents can change the pattern in which shoelaces are inserted into shoes, change the size or color of a single shirt button, or change the position of a pen or pencil in a pocket. These signs on the body can mean "I have information for you" or "I am awaiting further instructions."
Conclusion
The principle of "dead drops" has long occupied a certain niche in the art of information transfer, although it was originally developed exclusively for spies and agents to avoid interception by hostile intelligence services. But it can be adapted in the same way for the transfer of electronic data carriers under conditions of total surveillance or power outages. The fact that such caches do not require electricity or any external resources makes them unhackable, untraceable and protected from EMP.So, with careful planning and a little ingenuity, you can create a system to transmit any information you need, regardless of Wi-Fi signal, cell phone signal, or power source.
