Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,096
- Points
- 113
The Versa Director zero-day vulnerability opens the door for China to the systems of the United States and India.
The Chinese hacker group Volt Typhoon carried out a series of attacks using 0Day in the Versa Director management system, a platform that ISPs use to manage virtual networks.
Vulnerability CVE-2024-39717 (CVSS score: 7.2) allows downloading malicious files disguised as PNG images to gain access to corporate networks. The bug affected versions 21.2.3, 22.1.2 and 22.1.3. Updating to version 22.1.4 fixes the issue, and Versa recommends that administrators follow best practices to protect the system. In addition, CISA recently added this vulnerability to its KEV directory.
Researchers at Black Lotus Labs discovered the bug in June after finding a malicious file uploaded to VirusTotal. The attackers used the flaw to install the VersaMem web shell, which has not yet been detected by antiviruses. The analysis showed that since June 12, the web shell has been actively used to hack into SOHO routers and install malware.
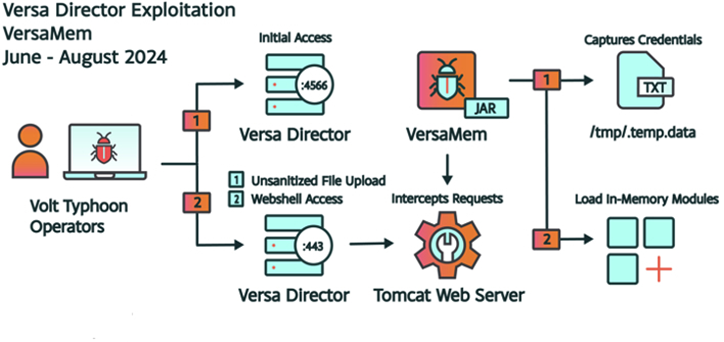
Volt Typhoon Attack Chain
Although admin privileges are required to exploit the vulnerability, the hackers obtained them through the open port of the Versa Director, which is used to ensure high availability (HA) of hosts. The attackers created an account with high privileges, injected a malicious web shell, which was then used to steal user credentials.
Versa confirmed that the vulnerability could have been exploited to steal credentials if the HA port was not secured in accordance with the company's recommendations. The company also explained that the port is open by default to provide a high availability feature.
According to Black Lotus Labs, at least 4 organizations in the United States and 1 in India were affected. The attackers were able to gain access to the internal networks of one of the companies. Experts attributed the attacks to the Volt Typhoon group, which is known for attacking routers and VPN devices to gain covert access to target networks. Previously, the group used similar methods to create a botnet and attack critical infrastructure.
Source
The Chinese hacker group Volt Typhoon carried out a series of attacks using 0Day in the Versa Director management system, a platform that ISPs use to manage virtual networks.
Vulnerability CVE-2024-39717 (CVSS score: 7.2) allows downloading malicious files disguised as PNG images to gain access to corporate networks. The bug affected versions 21.2.3, 22.1.2 and 22.1.3. Updating to version 22.1.4 fixes the issue, and Versa recommends that administrators follow best practices to protect the system. In addition, CISA recently added this vulnerability to its KEV directory.
Researchers at Black Lotus Labs discovered the bug in June after finding a malicious file uploaded to VirusTotal. The attackers used the flaw to install the VersaMem web shell, which has not yet been detected by antiviruses. The analysis showed that since June 12, the web shell has been actively used to hack into SOHO routers and install malware.

Volt Typhoon Attack Chain
Although admin privileges are required to exploit the vulnerability, the hackers obtained them through the open port of the Versa Director, which is used to ensure high availability (HA) of hosts. The attackers created an account with high privileges, injected a malicious web shell, which was then used to steal user credentials.
Versa confirmed that the vulnerability could have been exploited to steal credentials if the HA port was not secured in accordance with the company's recommendations. The company also explained that the port is open by default to provide a high availability feature.
According to Black Lotus Labs, at least 4 organizations in the United States and 1 in India were affected. The attackers were able to gain access to the internal networks of one of the companies. Experts attributed the attacks to the Volt Typhoon group, which is known for attacking routers and VPN devices to gain covert access to target networks. Previously, the group used similar methods to create a botnet and attack critical infrastructure.
Source

