Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Hundreds of thousands of devices are still not updated, undermining system security.
A critical vulnerability in the Fortinet security systems affected about 150,000 devices worldwide.
Vulnerability CVE-2024-21762 (CVSS score: 9.8) is characterized as an Out-of-Bounds write problem in FortiOS, which allows an unauthenticated attacker to perform Remote Code Execution (RCE) using specially generated requests. The cybersecurity Agency CISA confirmed the active use of the flaw by including it in the KEV catalog.
A month after Fortinet took steps to fix the bug, the Shadowserver service found about 150,000 vulnerable devices, most of which (more than 24,000) are located in the United States, India, Brazil and Canada. Companies can check whether their SSL VPN systems are vulnerable by using a simple Python script developed by researchers from BishopFox.
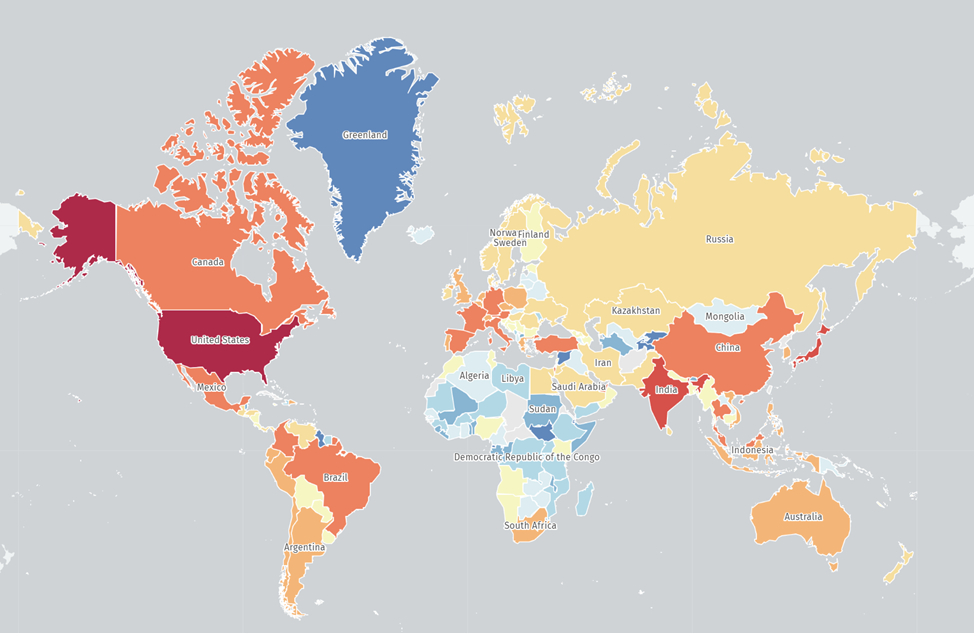
Geography of vulnerable devices
Details about groups that actively exploit the vulnerability are still limited, as public platforms do not record such activity, or the vulnerability is used in selective attacks by more advanced cybercriminals.
A critical vulnerability in the Fortinet security systems affected about 150,000 devices worldwide.
Vulnerability CVE-2024-21762 (CVSS score: 9.8) is characterized as an Out-of-Bounds write problem in FortiOS, which allows an unauthenticated attacker to perform Remote Code Execution (RCE) using specially generated requests. The cybersecurity Agency CISA confirmed the active use of the flaw by including it in the KEV catalog.
A month after Fortinet took steps to fix the bug, the Shadowserver service found about 150,000 vulnerable devices, most of which (more than 24,000) are located in the United States, India, Brazil and Canada. Companies can check whether their SSL VPN systems are vulnerable by using a simple Python script developed by researchers from BishopFox.

Geography of vulnerable devices
Details about groups that actively exploit the vulnerability are still limited, as public platforms do not record such activity, or the vulnerability is used in selective attacks by more advanced cybercriminals.

