Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,038
- Points
- 113
The long-running campaign showed how cyber espionage is conducted at the state level.
Sophos specialists have identified a complex and long-term cyber espionage operation by Chinese state hackers aimed at maintaining constant access to the network of a government organization in Southeast Asia. The campaign was named Crimson Palace.
Cyber spies sought to gain access to critical IT systems, conduct intelligence on specific users, collect confidential military and technical information, and deploy various malicious programs for remote control.
Although the name of the targeted government organization was not disclosed, it is known that the country in which it is located has ongoing territorial conflicts with China in the South China Sea. This suggests that we may be talking about the Philippines, which has previously been attacked by the Chinese group Mustang Panda.
Operation Crimson Palace includes 3 clusters of activity, some of which use the same tactics:
According to Sophos, they are part of a coordinated campaign organized by a single group with a large set of tools, a diverse infrastructure, and multiple operators.
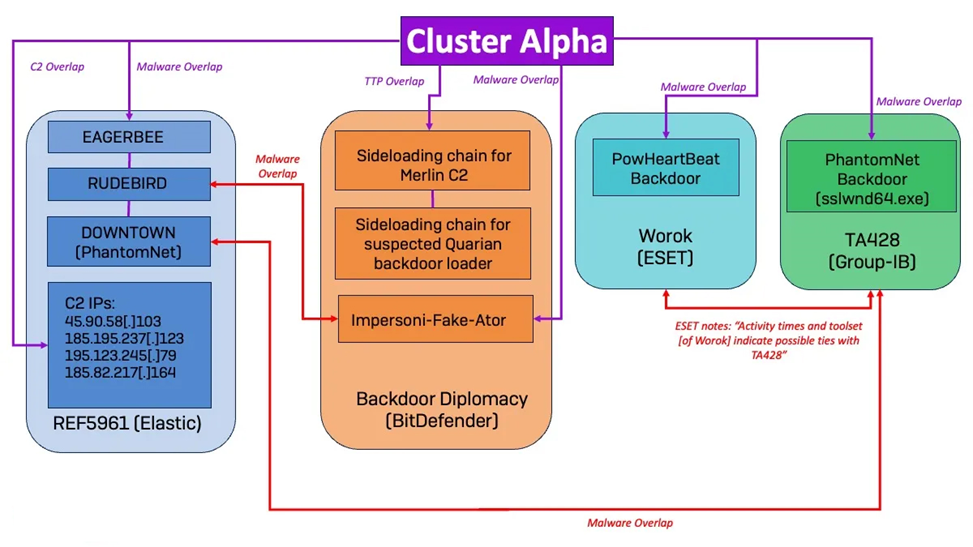
Intersection of the with other threat actors
The campaign is notable for its use of previously unknown malware such as PocoProxy, as well as an updated version of EAGERBEE and other well-known malware families, including NUPAKAGE, PowHeartBeat, RUDEBIRD, DOWNTOWN (PhantomNet), and EtherealGh0st (also known as CCoreDoor).
The campaign also features extensive use of DLL Sideloading techniques and unusual stealth techniques. The attackers used many new methods to bypass the protection:
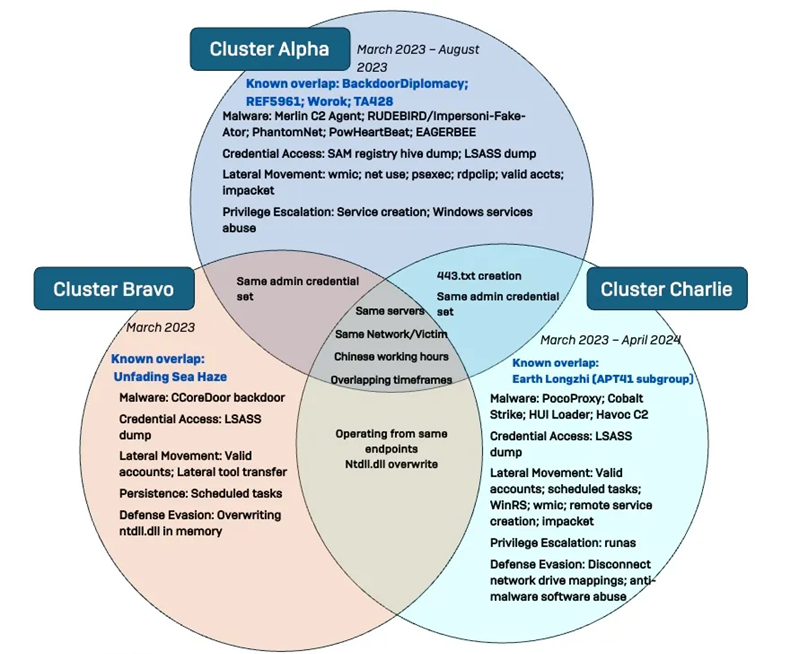
Differences and coincidences between the three clusters
The Sophos report also provides indicators of compromise (IoC) for each cluster of activity, and in the meantime, experts continue to investigate the campaign to find out more details about the attacks. Note that HUI Loader was previously used by Chinese groups in attacks on the gambling sector in Southeast Asia for the purpose of espionage.
Sophos specialists have identified a complex and long-term cyber espionage operation by Chinese state hackers aimed at maintaining constant access to the network of a government organization in Southeast Asia. The campaign was named Crimson Palace.
Cyber spies sought to gain access to critical IT systems, conduct intelligence on specific users, collect confidential military and technical information, and deploy various malicious programs for remote control.
Although the name of the targeted government organization was not disclosed, it is known that the country in which it is located has ongoing territorial conflicts with China in the South China Sea. This suggests that we may be talking about the Philippines, which has previously been attacked by the Chinese group Mustang Panda.
Operation Crimson Palace includes 3 clusters of activity, some of which use the same tactics:
- Cluster Alpha (STAC1248) (March 2023-August 2023), has similarities with the groups BackdoorDiplomacy, REF5961, Worok, and TA428. Scouting server subnets and Active Directory infrastructure.
- The Bravo cluster (STAC1870) (from March 2023), shares common features with Unfading Sea Haze. Use valid accounts for lateral movement and deployment of the EtherealGh0st malware.
- Cluster Charlie (STAC1305) (March 2023-April 2024), intersects with Earth Longzhi (subgroup APT41). It uses PocoProxy to establish permanent access and HUI Loader to deliver Cobalt Strike.
According to Sophos, they are part of a coordinated campaign organized by a single group with a large set of tools, a diverse infrastructure, and multiple operators.

Intersection of the with other threat actors
The campaign is notable for its use of previously unknown malware such as PocoProxy, as well as an updated version of EAGERBEE and other well-known malware families, including NUPAKAGE, PowHeartBeat, RUDEBIRD, DOWNTOWN (PhantomNet), and EtherealGh0st (also known as CCoreDoor).
The campaign also features extensive use of DLL Sideloading techniques and unusual stealth techniques. The attackers used many new methods to bypass the protection:
- overwriting an in-memory DLL to remove the antivirus agent from the kernel;
- using antivirus software for sideloading;
- and various other techniques for testing the most effective and secretive methods for completing tasks.

Differences and coincidences between the three clusters
The Sophos report also provides indicators of compromise (IoC) for each cluster of activity, and in the meantime, experts continue to investigate the campaign to find out more details about the attacks. Note that HUI Loader was previously used by Chinese groups in attacks on the gambling sector in Southeast Asia for the purpose of espionage.

