Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,089
- Points
- 113
Braille helps hide malicious files to infect Windows.
The US Cybersecurity Agency (CISA) has demanded that federal agencies protect their systems as soon as possible from a recently discovered vulnerability in Windows, exploited by the Void Banshee hacker group.
The CVE-2024-43461 spoofing vulnerability (CVSS score: 8.8) in Windows MSHTML was disclosed as part of Microsoft's September (Patch Tuesday) security updates. Initially, it was believed that the vulnerability was not exploited in the attacks, but the company later confirmed that it had been exploited before the problem was fixed.
According to Microsoft, the bug was exploited by attackers before July 2024, as part of a chain of attacks that included another spoofing vulnerability, CVE-2024-38112 (CVSS score: 7.5), which is also related to MSHTML, which allowed hackers to run arbitrary code on vulnerable systems when opening a malicious file or navigating to a specially prepared web page.
Trend Micro ZDI specialists who discovered the vulnerability reported that the Void Banshee group used the bug to install the infostealer. During the attacks, cybercriminals disguised malicious HTA files as PDF documents, hiding the extension with 26 encoded whitespace characters in Braille.
The file name started with PDF, followed by 26 whitespace Braille characters, and only then did the actual .hta extension follow:
Books_A0UJKO.pdf%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80.hta
However, when Windows tries to open such a file, the braille space characters hide the HTA extension outside the visible area, leaving "..." instead. As a result, the file looks like a PDF document, which increases the chances of the user opening it.
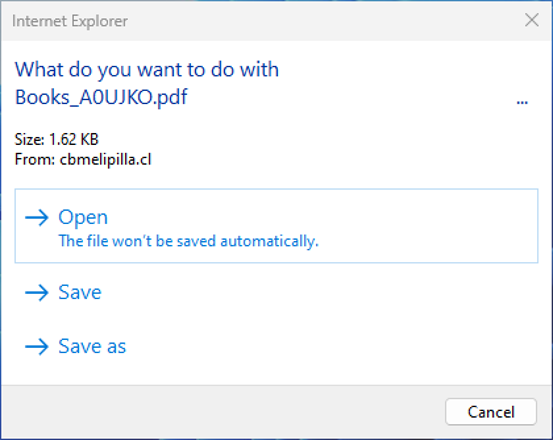
HTA file disguised as PDF
After the update, the braille space characters remain, but now Windows displays the true .hta extension in tooltips.
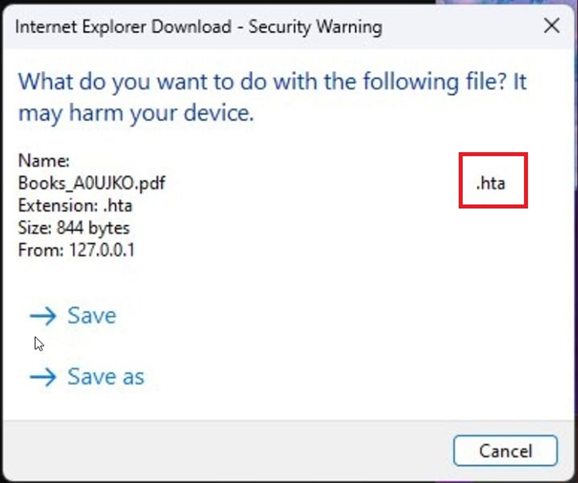
Displaying the actual file extension in the dialog
The attacks used the Atlantida malware, which is designed to steal passwords, authentication cookies, and crypto wallets from infected devices. The Void Banshee group, known since 2023, is targeting companies in North America, Europe, and Southeast Asia in an effort to gain financial gain and steal data.
CISA has included the CVE-2024-43461 vulnerability in its Known Exploited Vulnerabilities (KEV) directory and has required federal agencies to remediate the vulnerabilities by October 7. Under BOD Directive 22-01, agencies must install updates within 3 weeks to prevent further attacks.
CISA emphasizes that such vulnerabilities are frequent attack vectors, posing a serious threat to government organizations. In this regard, not only federal agencies, but also private companies around the world are urged to take steps to protect their systems as soon as possible.
It is worth noting that in the September updates, Microsoft fixed 3 more actively exploited vulnerabilities, including CVE-2024-38217. This vulnerability has been exploited since 2018 in attacks aimed at bypassing Windows security systems, such as Smart App Control and Mark of the Web (MotW).
Source
The US Cybersecurity Agency (CISA) has demanded that federal agencies protect their systems as soon as possible from a recently discovered vulnerability in Windows, exploited by the Void Banshee hacker group.
The CVE-2024-43461 spoofing vulnerability (CVSS score: 8.8) in Windows MSHTML was disclosed as part of Microsoft's September (Patch Tuesday) security updates. Initially, it was believed that the vulnerability was not exploited in the attacks, but the company later confirmed that it had been exploited before the problem was fixed.
According to Microsoft, the bug was exploited by attackers before July 2024, as part of a chain of attacks that included another spoofing vulnerability, CVE-2024-38112 (CVSS score: 7.5), which is also related to MSHTML, which allowed hackers to run arbitrary code on vulnerable systems when opening a malicious file or navigating to a specially prepared web page.
Trend Micro ZDI specialists who discovered the vulnerability reported that the Void Banshee group used the bug to install the infostealer. During the attacks, cybercriminals disguised malicious HTA files as PDF documents, hiding the extension with 26 encoded whitespace characters in Braille.
The file name started with PDF, followed by 26 whitespace Braille characters, and only then did the actual .hta extension follow:
Books_A0UJKO.pdf%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80.hta
However, when Windows tries to open such a file, the braille space characters hide the HTA extension outside the visible area, leaving "..." instead. As a result, the file looks like a PDF document, which increases the chances of the user opening it.

HTA file disguised as PDF
After the update, the braille space characters remain, but now Windows displays the true .hta extension in tooltips.

Displaying the actual file extension in the dialog
The attacks used the Atlantida malware, which is designed to steal passwords, authentication cookies, and crypto wallets from infected devices. The Void Banshee group, known since 2023, is targeting companies in North America, Europe, and Southeast Asia in an effort to gain financial gain and steal data.
CISA has included the CVE-2024-43461 vulnerability in its Known Exploited Vulnerabilities (KEV) directory and has required federal agencies to remediate the vulnerabilities by October 7. Under BOD Directive 22-01, agencies must install updates within 3 weeks to prevent further attacks.
CISA emphasizes that such vulnerabilities are frequent attack vectors, posing a serious threat to government organizations. In this regard, not only federal agencies, but also private companies around the world are urged to take steps to protect their systems as soon as possible.
It is worth noting that in the September updates, Microsoft fixed 3 more actively exploited vulnerabilities, including CVE-2024-38217. This vulnerability has been exploited since 2018 in attacks aimed at bypassing Windows security systems, such as Smart App Control and Mark of the Web (MotW).
Source

