Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,245
- Points
- 113
Chinese hackers use their victims partners for spying.
2 years after the last appearance, the Chinese hacker group GhostEmperor has re-established itself. Known for its sophisticated supply chain attacks targeting telecommunications and government entities in Southeast Asia, GhostEmperor has significantly improved its stealth techniques. This was reported by Sygnia in a new report.
Sygnia discovered that GhostEmperor was behind an incident late last year in which an unnamed client's network was compromised and used as a springboard to access another victim's systems. GhostEmperor was first identified by Kaspersky Lab in 2021. Sygnia noted that the lack of public reports about GhostEmperor during this period remains a mystery.
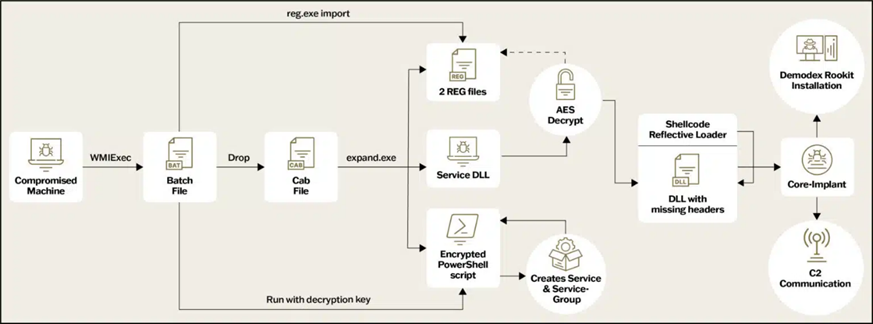
GhostEmperor Infection Chain
GhostEmperor is known for using a kernel - level rootkit, which allows them to avoid detection by security systems, including EDR solutions. Such tools are usually developed by State-sponsored groups because of the resources required to do so. The rootkit provides access to a privileged part of the computer's operating system, the kernel, which makes it difficult to detect for standard security tools.
The Demodex rootkit is basically an updated version of the previous version, but of particular interest was caused by a different infection chain, which has become more complex and secretive. This indicates that GhostEmperor is continuing to develop its methods to ensure maximum stealth.
In 2021, Kaspersky Lab described GhostEmperor as highly skilled hackers who attacked major targets in Malaysia, Thailand, Vietnam, and Indonesia. Additional victims were identified in Egypt, Ethiopia and Afghanistan. Some organizations from these countries have close ties with Southeast Asian countries. It is likely that hackers could have used the infections to spy on the activities of countries of geopolitical interest to the group.
An important aspect of the attack – after breaking into the client's network, hackers attacked the networks of its business partners. Sygnia hopes that the information provided will help organizations better prepare for threats. It is necessary to minimize the time that the enemy is in the environment and speed up the detection process. Although 100% security is not possible, organizations must develop strategies to prevent and mitigate risks.
Source
2 years after the last appearance, the Chinese hacker group GhostEmperor has re-established itself. Known for its sophisticated supply chain attacks targeting telecommunications and government entities in Southeast Asia, GhostEmperor has significantly improved its stealth techniques. This was reported by Sygnia in a new report.
Sygnia discovered that GhostEmperor was behind an incident late last year in which an unnamed client's network was compromised and used as a springboard to access another victim's systems. GhostEmperor was first identified by Kaspersky Lab in 2021. Sygnia noted that the lack of public reports about GhostEmperor during this period remains a mystery.

GhostEmperor Infection Chain
GhostEmperor is known for using a kernel - level rootkit, which allows them to avoid detection by security systems, including EDR solutions. Such tools are usually developed by State-sponsored groups because of the resources required to do so. The rootkit provides access to a privileged part of the computer's operating system, the kernel, which makes it difficult to detect for standard security tools.
The Demodex rootkit is basically an updated version of the previous version, but of particular interest was caused by a different infection chain, which has become more complex and secretive. This indicates that GhostEmperor is continuing to develop its methods to ensure maximum stealth.
In 2021, Kaspersky Lab described GhostEmperor as highly skilled hackers who attacked major targets in Malaysia, Thailand, Vietnam, and Indonesia. Additional victims were identified in Egypt, Ethiopia and Afghanistan. Some organizations from these countries have close ties with Southeast Asian countries. It is likely that hackers could have used the infections to spy on the activities of countries of geopolitical interest to the group.
An important aspect of the attack – after breaking into the client's network, hackers attacked the networks of its business partners. Sygnia hopes that the information provided will help organizations better prepare for threats. It is necessary to minimize the time that the enemy is in the environment and speed up the detection process. Although 100% security is not possible, organizations must develop strategies to prevent and mitigate risks.
Source
