Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
When I get a new phone, I always take it apart. Not out of curiosity or political reasons, but simply for safety. The first step is to remove two or three tiny microphones from the board. This is just the beginning of a complex process. But even after several days of working with a soldering iron, the smartphone is still the most dangerous item in my apartment.

Microphones on smartphone motherboard before removal
Before the publication of the Pegasus project - exposing the fatal consequences of the activities of the NSO Group, another commercial firm that got out of the control of the security industry - most smartphone manufacturers and most of the global press rolled their eyes in unison when I publicly called the new iPhone a potential threat to life.
Now everyone understood what it was about.
For many years, reports were published that the NSO Group was engaged in hacking phones for profit, and was involved in the deaths and detentions of journalists and human rights activists . That the operating systems of smartphones are rife with catastrophic holes (and the code is written in outdated languages long ago recognized as unsafe). For many years, experts have been explaining: even when everything works as expected, the mobile ecosystem is a hellish dystopia, a mixture of surveillance of users and outright manipulation. However, to this day, many do not see evil in an industry that seems so good.
Over the past eight years, I have been trying to convince my only friend to quit smoking and drink less, while ads shout from all cracks: "Nine out of ten doctors smoke iPhones!", "Unprotected mobile surfing is refreshing!"

But I am still optimistic, so the Pegasus project seems to me to be a turning point. This is a well-studied, detailed and completely insane story about a "Trojan horse" with wings (in Greek mythology, Pegasus is a winged horse, the son of the Gorgon Medusa, with a blow of his hoof on the ground could knock out sources, - approx. Trans.), Which turns the phone in your pocket into a universal bug. It can be turned on or off remotely without your knowledge.
This is how the Washington Post describes it:
In short, the phone in your hand exists in a state of perpetual insecurity. He is always open to infection by anyone with enough money. The whole business of this "information security industry" is creating new infections that bypass the latest security updates. These tools are then sold to countries in dire need of the most sophisticated means of oppressing their populations.
An industry like this, with the sole purpose of producing vulnerabilities, must be eliminated.
Even if tomorrow the NSO Group and the entire industry are suddenly wiped off the face of the earth by a volcano of public outrage, it won't change the fact that we are in the midst of the greatest computer security crisis in history. And the developers Apple, Google, Microsoft, who want to sell the product, not bring it to perfection, and their exact opposite - the well-meaning Linux developers who want to perfect the product, not sell it - they all calmly write code in unsafe languages, because ... well, because we are used to it, and modernization requires a lot of effort, not to mention the cost. Overwhelming most of the vulnerabilities that are then exploited by the insecurity industry come from technical reasons related to memory management. Therefore, choosing a safer language is a critical measure of protection ... but few people think about it.
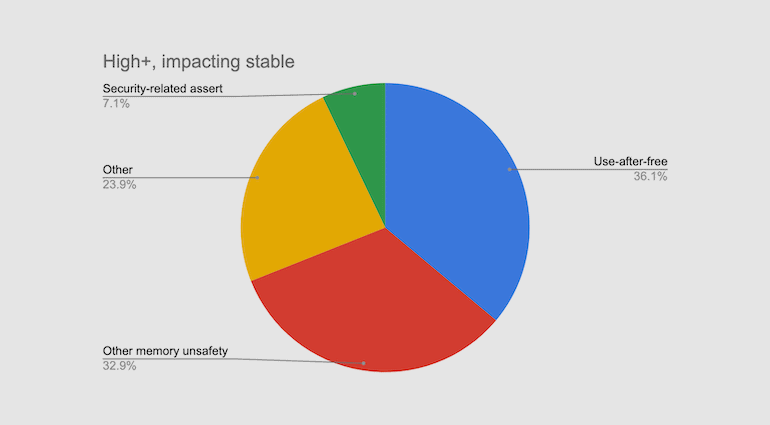
According to Google, 70% of serious bugs in the Chrome browser are related to memory safety. They can be eliminated by using safer languages
If you want change, you need to stimulate it. For example, if you want to give Microsoft a heart attack, suggest the idea of legal liability for bad code in a commercial product. If you want to deprive Facebook of sleep - tell us about the idea of legal responsibility for any leaks of personal data collected unnecessarily. Imagine how quickly Zuckerberg starts pressing a key Delete.
Where there is no responsibility, there is no accountability ... and that brings us to the role of the state.
State-sponsored hacking has become such a common competition that it should have its own category at the Olympics.
Each country condemns the efforts of others as a crime, while refusing to admit guilt for their own violations. So don't be surprised when Jamaica sends a bobsleigh crew to the winter games. Or when a private company comes up and claims the same right to race as the nation state.
If hacking is legal for us, it will be legal for them, the private sector. The basic principle of capitalism: it's just business. If everyone does this, then you can.
This logical oversimplification is the source of all the problems in the history of arms control. And the same mutually assured destruction as in a nuclear conflict is almost guaranteed in a digital conflict, thanks to full interconnection and network homogeneity.
Consider the Pegasus, which is aimed primarily at the iPhone. While iPhones are by default more private and secure than Android, it's a homogeneous monoculture: if you find a way to infect one, you can (probably) infect them all. The problem is compounded by the fact that Apple does not allow customers to make any meaningful changes to the way iOS devices work. If you combine the monoculture, the "black box" with the almost universal popularity of Apple among the world elite, then the reasons for the active hunt for the iPhone by the NSO Group become obvious.
Governments need to understand that it is not in the public interest to allow NSO Group and their malevolent counterparts to operate, much less subsidize them. Regardless of where the client or the client state is located on the axis of authoritarianism. The last US president was constantly tweeting from his iPhone, and I bet half of the most senior officials and their aides in any country read these tweets on their iPhones too.

Whether we like it or not, adversaries and allies have a common technological environment, and every day we are more and more dependent on devices running a common code.
The idea of strategic parity in intelligence gathering between the great powers (USA, China, Russia, even Israel) and developing countries (for example, Azerbaijan) is, of course, deeply flawed. Governments have not yet grasped the threat because the opportunity gap has not yet disappeared. But soon they will realize that the full power of global digital espionage is becoming available to absolutely any player.
In technology (as in the fight against viral infections), protecting everyone means protecting everyone. The first step is to ban the trade in malware. We do not allow the trading of dangerous biological viruses, the same should be true for digital infections. Eliminating the profit motive reduces proliferation risks while protecting progress by leaving room for socially significant research.
While removing malware from the commercial market will not take it away from government intelligence agencies, we at least reduce the likelihood that reckless drug dealers and sexually anxious Hollywood producers with millions of dollars in their pockets can infect any (or all) iPhones on the planet , spoiling the status toys of latte lovers.
The moratorium is only an intermediate stage in order to gain time. The next step is legal responsibility. It is important to understand that neither the scale of the NSO Group's business, nor the global damage to the world community, would have been possible without access to the global capital of such immoral firms as Novalpina Capital (Europe) and Francisco Partners (USA) ... The plan is simple: if the companies don't sell, the owners should be arrested. The industry's only product is deliberate, predictable harm, and these companies are voluntary partners. In addition, if a company is engaged in such activities at the direction of the state , liability should go beyond the vegetarian civil and criminal codes. A coordinated international response is needed.

Diplomacy by other means
Imagine that you are the editorial staff of the Washington Post (of course, first you have to be deprived of the backbone, but still). Imagine that your columnist is killed, and in response you quietly turn to the organizers of this murder with a request to fill out a little more paperwork next time. Quite frankly, the Post's reaction to the NSO Group scandal is so shamefully weak that it is a scandal in itself: How many authors must die before they can hear the effects of spyware?
Saudi Arabia, with the help of Pegasus, hacked into the phones of Jamal Khashoggi's ex-wife and his fiancée - and used the information received to prepare a monstrous murder and the subsequent hiding of traces.
But Khashoggi is only the most famous of the Pegasus victims, thanks to the cold-blooded and brutal nature of his murder. The NSO Group's “product” (read: criminal service) has been used to spy on countless other journalists, judges and even teachers. For opposition politicians, for the spouses and children of "objects of surveillance" because of their doctors, lawyers and even their priests. One thing that is always overlooked by people who think the ban is "too extreme" is that this industry sells the ability to just shoot reporters you don't like.
If we do not stop the sale of these technologies, then we will have not 50 thousand, but 50 million targets. And it will happen much faster than any of us expects.
This will be the reality: people are so busy playing with their smartphones that they don't notice - the devices are already under someone else's control.

Microphones on smartphone motherboard before removal
Before the publication of the Pegasus project - exposing the fatal consequences of the activities of the NSO Group, another commercial firm that got out of the control of the security industry - most smartphone manufacturers and most of the global press rolled their eyes in unison when I publicly called the new iPhone a potential threat to life.
Now everyone understood what it was about.
For many years, reports were published that the NSO Group was engaged in hacking phones for profit, and was involved in the deaths and detentions of journalists and human rights activists . That the operating systems of smartphones are rife with catastrophic holes (and the code is written in outdated languages long ago recognized as unsafe). For many years, experts have been explaining: even when everything works as expected, the mobile ecosystem is a hellish dystopia, a mixture of surveillance of users and outright manipulation. However, to this day, many do not see evil in an industry that seems so good.
Over the past eight years, I have been trying to convince my only friend to quit smoking and drink less, while ads shout from all cracks: "Nine out of ten doctors smoke iPhones!", "Unprotected mobile surfing is refreshing!"

But I am still optimistic, so the Pegasus project seems to me to be a turning point. This is a well-studied, detailed and completely insane story about a "Trojan horse" with wings (in Greek mythology, Pegasus is a winged horse, the son of the Gorgon Medusa, with a blow of his hoof on the ground could knock out sources, - approx. Trans.), Which turns the phone in your pocket into a universal bug. It can be turned on or off remotely without your knowledge.
This is how the Washington Post describes it:
“Claude Mangin is the wife of a French political activist imprisoned in Morocco. A month ago, her iPhone 11 received an iMessage from an unknown account that delivered malware to the phone. The software was installed without any warnings or notifications, bypassing Apple's security systems.
The examination was unable to reveal what exactly was copied and sent. It could be anything: Pegasus has access to email, voice, social media, passwords, contact list, photos, videos, sound recordings, and surfing history. Spyware can activate cameras or microphones for fresh images and recordings. Can listen to calls and voicemail. Maintain geolocation logs and determine where the user is now: whether the person is standing still, and if he is moving, then in which direction.
And all this without the slightest human intervention. The user does not need to touch the phone, he does not even know that he received a mysterious message from a stranger - in the case of Mangen, a certain one linakeller2203@gmail.com”.
In short, the phone in your hand exists in a state of perpetual insecurity. He is always open to infection by anyone with enough money. The whole business of this "information security industry" is creating new infections that bypass the latest security updates. These tools are then sold to countries in dire need of the most sophisticated means of oppressing their populations.
An industry like this, with the sole purpose of producing vulnerabilities, must be eliminated.
Even if tomorrow the NSO Group and the entire industry are suddenly wiped off the face of the earth by a volcano of public outrage, it won't change the fact that we are in the midst of the greatest computer security crisis in history. And the developers Apple, Google, Microsoft, who want to sell the product, not bring it to perfection, and their exact opposite - the well-meaning Linux developers who want to perfect the product, not sell it - they all calmly write code in unsafe languages, because ... well, because we are used to it, and modernization requires a lot of effort, not to mention the cost. Overwhelming most of the vulnerabilities that are then exploited by the insecurity industry come from technical reasons related to memory management. Therefore, choosing a safer language is a critical measure of protection ... but few people think about it.

According to Google, 70% of serious bugs in the Chrome browser are related to memory safety. They can be eliminated by using safer languages
If you want change, you need to stimulate it. For example, if you want to give Microsoft a heart attack, suggest the idea of legal liability for bad code in a commercial product. If you want to deprive Facebook of sleep - tell us about the idea of legal responsibility for any leaks of personal data collected unnecessarily. Imagine how quickly Zuckerberg starts pressing a key Delete.
Where there is no responsibility, there is no accountability ... and that brings us to the role of the state.
State-sponsored hacking has become such a common competition that it should have its own category at the Olympics.
Each country condemns the efforts of others as a crime, while refusing to admit guilt for their own violations. So don't be surprised when Jamaica sends a bobsleigh crew to the winter games. Or when a private company comes up and claims the same right to race as the nation state.
If hacking is legal for us, it will be legal for them, the private sector. The basic principle of capitalism: it's just business. If everyone does this, then you can.
This logical oversimplification is the source of all the problems in the history of arms control. And the same mutually assured destruction as in a nuclear conflict is almost guaranteed in a digital conflict, thanks to full interconnection and network homogeneity.
Consider the Pegasus, which is aimed primarily at the iPhone. While iPhones are by default more private and secure than Android, it's a homogeneous monoculture: if you find a way to infect one, you can (probably) infect them all. The problem is compounded by the fact that Apple does not allow customers to make any meaningful changes to the way iOS devices work. If you combine the monoculture, the "black box" with the almost universal popularity of Apple among the world elite, then the reasons for the active hunt for the iPhone by the NSO Group become obvious.
Governments need to understand that it is not in the public interest to allow NSO Group and their malevolent counterparts to operate, much less subsidize them. Regardless of where the client or the client state is located on the axis of authoritarianism. The last US president was constantly tweeting from his iPhone, and I bet half of the most senior officials and their aides in any country read these tweets on their iPhones too.

Whether we like it or not, adversaries and allies have a common technological environment, and every day we are more and more dependent on devices running a common code.
The idea of strategic parity in intelligence gathering between the great powers (USA, China, Russia, even Israel) and developing countries (for example, Azerbaijan) is, of course, deeply flawed. Governments have not yet grasped the threat because the opportunity gap has not yet disappeared. But soon they will realize that the full power of global digital espionage is becoming available to absolutely any player.
In technology (as in the fight against viral infections), protecting everyone means protecting everyone. The first step is to ban the trade in malware. We do not allow the trading of dangerous biological viruses, the same should be true for digital infections. Eliminating the profit motive reduces proliferation risks while protecting progress by leaving room for socially significant research.
While removing malware from the commercial market will not take it away from government intelligence agencies, we at least reduce the likelihood that reckless drug dealers and sexually anxious Hollywood producers with millions of dollars in their pockets can infect any (or all) iPhones on the planet , spoiling the status toys of latte lovers.
The moratorium is only an intermediate stage in order to gain time. The next step is legal responsibility. It is important to understand that neither the scale of the NSO Group's business, nor the global damage to the world community, would have been possible without access to the global capital of such immoral firms as Novalpina Capital (Europe) and Francisco Partners (USA) ... The plan is simple: if the companies don't sell, the owners should be arrested. The industry's only product is deliberate, predictable harm, and these companies are voluntary partners. In addition, if a company is engaged in such activities at the direction of the state , liability should go beyond the vegetarian civil and criminal codes. A coordinated international response is needed.

Diplomacy by other means
Imagine that you are the editorial staff of the Washington Post (of course, first you have to be deprived of the backbone, but still). Imagine that your columnist is killed, and in response you quietly turn to the organizers of this murder with a request to fill out a little more paperwork next time. Quite frankly, the Post's reaction to the NSO Group scandal is so shamefully weak that it is a scandal in itself: How many authors must die before they can hear the effects of spyware?
Saudi Arabia, with the help of Pegasus, hacked into the phones of Jamal Khashoggi's ex-wife and his fiancée - and used the information received to prepare a monstrous murder and the subsequent hiding of traces.
But Khashoggi is only the most famous of the Pegasus victims, thanks to the cold-blooded and brutal nature of his murder. The NSO Group's “product” (read: criminal service) has been used to spy on countless other journalists, judges and even teachers. For opposition politicians, for the spouses and children of "objects of surveillance" because of their doctors, lawyers and even their priests. One thing that is always overlooked by people who think the ban is "too extreme" is that this industry sells the ability to just shoot reporters you don't like.
If we do not stop the sale of these technologies, then we will have not 50 thousand, but 50 million targets. And it will happen much faster than any of us expects.
This will be the reality: people are so busy playing with their smartphones that they don't notice - the devices are already under someone else's control.

