Tomcat
Professional
- Messages
- 2,688
- Reaction score
- 1,015
- Points
- 113
Urgently check your Docker settings to stop a possible attack.
A group of cybercriminals, Commando Cat, continues a financially motivated cryptojacking campaign aimed at incorrectly configured Docker instances.
Named after the use of the Commando project to create containers, the grouping was first documented by Cado Security earlier this year.
Malicious activities of cybercriminals include creating containers using an image "cmd.cat/chattr", after which they can manage Docker on the compromised host.
The process of each attack begins with checking the availability of the Docker Remote API server. After confirming availability, a container is created that allows attackers to reach the host operating system level.
If the required image is missing, attackers extract it from the repository "cmd.cat", followed by creating a container. During this process, attackers execute a string encoded in base64, which is decrypted into a script. This script checks for the presence of a file on the system and, if the file is missing, downloads and executes the malicious binary file ZiggyStarTux — an open source IRC bot based on the Kaiten malware (aka Tsunami).
Although the attackers C2 server was unavailable at the time of analysis by the researchers, the presence of certain User-Agent strings in the binary code made it possible to track the presence of this software on the network.
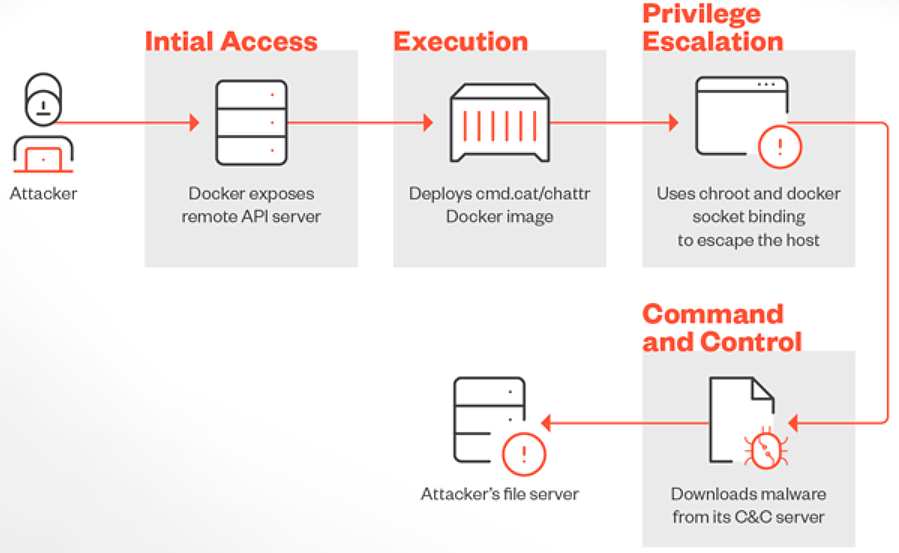
Attack pattern
"The significance of this attack lies in the use of Docker images to deploy cryptojacking scripts on compromised systems," the Trend Micro researchers noted. "This tactic allows attackers to exploit vulnerabilities in Docker configurations and avoid detection by antivirus software."
To protect development environments from such attacks, we recommend carefully configuring containers and APIs, using only official or certified images, and conducting regular security audits.
A group of cybercriminals, Commando Cat, continues a financially motivated cryptojacking campaign aimed at incorrectly configured Docker instances.
Named after the use of the Commando project to create containers, the grouping was first documented by Cado Security earlier this year.
Malicious activities of cybercriminals include creating containers using an image "cmd.cat/chattr", after which they can manage Docker on the compromised host.
The process of each attack begins with checking the availability of the Docker Remote API server. After confirming availability, a container is created that allows attackers to reach the host operating system level.
If the required image is missing, attackers extract it from the repository "cmd.cat", followed by creating a container. During this process, attackers execute a string encoded in base64, which is decrypted into a script. This script checks for the presence of a file on the system and, if the file is missing, downloads and executes the malicious binary file ZiggyStarTux — an open source IRC bot based on the Kaiten malware (aka Tsunami).
Although the attackers C2 server was unavailable at the time of analysis by the researchers, the presence of certain User-Agent strings in the binary code made it possible to track the presence of this software on the network.

Attack pattern
"The significance of this attack lies in the use of Docker images to deploy cryptojacking scripts on compromised systems," the Trend Micro researchers noted. "This tactic allows attackers to exploit vulnerabilities in Docker configurations and avoid detection by antivirus software."
To protect development environments from such attacks, we recommend carefully configuring containers and APIs, using only official or certified images, and conducting regular security audits.
