Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,586
- Points
- 113
How does the CIA's tool relate to such a deliberate attack?
The information security company Sangfor discovered a series of phishing attacks that exploit a vulnerability in WinRAR. Documents related to the geopolitical issues of Belarus and Russia serve as bait for victims, and the sender of emails is a person posing as a government employee.
The attack is carried out using the recently discovered WinRAR vulnerability CVE-2023-38831 (CVSS: 7.8). The attack is triggered if the user opens a malicious archive using a vulnerable version of WinRAR. Phishing emails and attachments are carefully prepared to circumvent email filtering systems. The names of archives and the contents of decoy documents are adapted for various purposes.
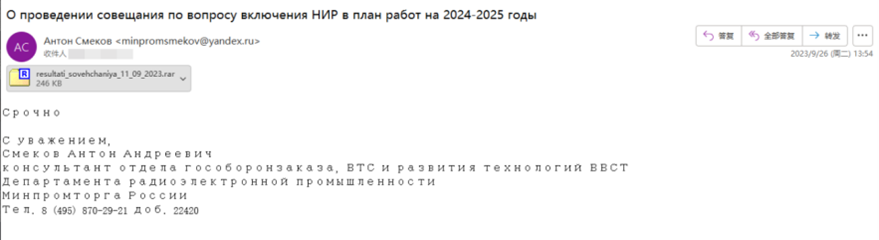
Example of a phishing email
The malicious Powershell script has been optimized over many iterations, which increases the degree of obfuscation and helps bypass static detection. Operator commands download and install the Athena backdoor using Discord as a communication channel to the Command and Control server (C2). The target is organizations with geopolitical significance, including defense industry enterprises, research institutions, and financial organizations.
In 2017, the WikiLeaks portal traditionally published a portion of CIA hacking tools, including the Athena backdoor. The tool is able to download malware to the victim's computer to perform certain tasks, as well as add/extract files to/from certain directories on the attacked system. An attacker can change the settings during program execution, depending on the task at hand. Thus, Athena allows you to gain control over a Windows computer and get any information.
It is noted that attackers show rapid development of abilities and adaptation to changes in the situation. The researchers said that taking into account various factors, the incident is most likely not the work of cybercriminals – it is likely that an previously unknown APT group (Advanced Persistent Threat) is behind the attacks.
The specified error in WinRAR has already been used by North Korean hackers. As part of the campaign, when a victim tries to open an archived HTML file in an email, malicious code is activated, allowing attackers to gain remote access to the system.
The information security company Sangfor discovered a series of phishing attacks that exploit a vulnerability in WinRAR. Documents related to the geopolitical issues of Belarus and Russia serve as bait for victims, and the sender of emails is a person posing as a government employee.
The attack is carried out using the recently discovered WinRAR vulnerability CVE-2023-38831 (CVSS: 7.8). The attack is triggered if the user opens a malicious archive using a vulnerable version of WinRAR. Phishing emails and attachments are carefully prepared to circumvent email filtering systems. The names of archives and the contents of decoy documents are adapted for various purposes.

Example of a phishing email
The malicious Powershell script has been optimized over many iterations, which increases the degree of obfuscation and helps bypass static detection. Operator commands download and install the Athena backdoor using Discord as a communication channel to the Command and Control server (C2). The target is organizations with geopolitical significance, including defense industry enterprises, research institutions, and financial organizations.
In 2017, the WikiLeaks portal traditionally published a portion of CIA hacking tools, including the Athena backdoor. The tool is able to download malware to the victim's computer to perform certain tasks, as well as add/extract files to/from certain directories on the attacked system. An attacker can change the settings during program execution, depending on the task at hand. Thus, Athena allows you to gain control over a Windows computer and get any information.
It is noted that attackers show rapid development of abilities and adaptation to changes in the situation. The researchers said that taking into account various factors, the incident is most likely not the work of cybercriminals – it is likely that an previously unknown APT group (Advanced Persistent Threat) is behind the attacks.
The specified error in WinRAR has already been used by North Korean hackers. As part of the campaign, when a victim tries to open an archived HTML file in an email, malicious code is activated, allowing attackers to gain remote access to the system.

