Carder
Professional
- Messages
- 2,620
- Reaction score
- 2,043
- Points
- 113
If your task is to find evidence on your hard drive, then the worst thing you can do is to “stomp” yourself, changing some data and creating new files. To prevent this from happening, it is best to work with electronic material evidence by booting from a live CD. Better yet, have a bootable media with a specialized distribution. We will talk about their choice and features in this article.
Forensics goals and methods
As you may have already learned from the previous article in the topic of this issue, forensics methods are divided into two large groups: analysis of a turned on system (for example, a running server) and off (for example, seized drives). They are also called dynamic and static analysis.These two methods are fundamentally different not only in approaches, but also in the data that can be collected. In the first case, it is monitoring the attacked system in real time. It is possible to directly assess disk and network activity, get a list of running processes, open ports, view logged in users, and most importantly, get from RAM the data that will disappear without a trace when the power is turned off. For example, the keys of a ransomware trojan, a decrypted copy of mounted crypto-containers, and even access to remote resources, if they were authorized in the current session. After shutting down the computer, all this information will be irretrievably lost, and the cryptographic containers will remain only encrypted files on the disk.
Each specialist forms kits for the analysis "live" based on his own needs. For example, it is enough for an administrator to be able to quickly pick up services that fell after an attack and restore production from a backup. Later, in a calm atmosphere, he may look at the logs, but he is unlikely to find anything valuable in them. Chinese proxy IPs? Signs of entering a corporate site through a leaky CMS that he wanted to patch a month ago? If all business processes go on as usual, further CI investigation becomes meaningless for him.
The anti-virus company's computer incident investigation department (which, together with law enforcement agencies, analyzes a recent case of mass infection) or FinCERT, which unravels APT in some payment system, has different approaches. Here are completely different priorities: you need to collect as much information as possible, which can then be used in court. Detect the botnet's C&C servers, find the source of the threat, reconstruct the hacking scenario in detail, and contact its organizers (ideally, with their subsequent arrest). This requires a thorough collection of evidence, but the problem is that the analysis of the system almost always introduces distortions into it. The task of a specialist in computer forensics is to minimize them and take them into account in further analysis.
How not to inherit the pathfinder
The first rule of forensics is not to distort the original. To do this, all actions are performed with an exact (sector-by-sector) copy of the investigated file system and full dumps of RAM.Unfortunately, in practice, this principle is often violated due to ignorance of the operating features of the operating system, including Live distributions. For convenience, in many of them, by default, the function of automatic connection of all detected drives is activated. This is especially true for Windows (including PE-based assemblies), which creates temporary files and service directories on each disk (System Volume Information, $ Recycle.Bin, and so on), but Linux has enough problems as well.
Many bootable Linux-based forensic distributions mount disk partitions with the option -o ro. This is believed to be sufficient to prevent accidental recording. However, even if to the user the disk looks like it is connected in read-only mode, the OS kernel and file system drivers can still change service data on it, for example, the time of the last file access.
By default, among the mount options, it is specified atime, which means to update the "last access time" attribute on any file access. For forensics it is wiser to use noatime.
Another problem is incorrectly unmounted partitions, which often happens when ejecting disks during the "mask show". Before the next mount, the corrupted filesystem will be checked and fsck will attempt to automatically fix any errors it finds. For example, the program will fix "dangling" inodes (which describe files deleted openly).
As a matter of fact, the drivers of all journaled file systems (ext3 / 4, ReiserFS, XFS, NTFS and others) ignore this option -o roduring system disk accesses. To disaccustom them to look at the log and try to make corrections, it is better to mount the partitions under study with the option ro,noload, ro,nologor ro,norecovery- depending on the type of file system, however, this is not a panacea either.
Unintentional writing to the drive under investigation during the analysis is still possible, and even at the stage of launching the Live distribution. For example, when searching for bootable media, writing drivers to initramfs and creating a swap file, or automatically mounting detected disk partitions (including searching for Root FS by a banal search of all connected disks). This is one of the reasons to physically connect the drive under investigation after loading the Live distribution.
Options for solving the problem of unauthorized writing to the disk under investigation depend on the features of the distribution kit and the device itself. For example, ext3 and ext4 volumes can be mounted as non-journaled (ext2).
For a long time, for non-destructive analysis of hard drives, it was considered sufficient to connect them as a block device in the "read-only" mode:
Code:
blockdev --setro / dev / sdb2 (replace sdb2 with the current drive designation)It would seem that everything is correct: blockdev uses a system call to change the kernel flag, which is checked at the filesystem level. If this flag is set, then it disables write operations to the file system, not only user ones, but also system ones (logging, recovery, superblock overwrite). This method is used in most distributions for forensics.
However, in practice, an incorrectly written FS driver can still skip this check and perform write operations.
Therefore, using blockdev in read-only mode is guaranteed to work only for applications launched from userspace, whose calls are checked by the driver, but not for the OS kernel and the drivers themselves.
The safest option is to place a virtual block device loop device between the disk being analyzed and the FS driver. It will not skip low-level commands and prevent the system from silently modifying the disk under investigation.
Code:
mount -o ro, loop / dev / sdb2 dir (where dir is an arbitrary directory name)The method works similarly with disk images.
Code:
mount -o ro, loop diskimage.dd dirFlash
Certain difficulties arise with solid state drives. Their controllers independently perform low-level operations to speed up subsequent writes and equalize the wear and tear of flash memory cells. Banal operations Garbage Collection and TRIM can be performed at any time and bury the hope of recovering deleted files.There are at least two options for solving this problem:
- Unplug the memory chips and read them as a programmer (useless if the SSD uses built-in encryption, and now it is activated by default on most models).
- Create a long queue of read commands (usually the controller does not perform internal operations while processing external requests).
Additional distortions when working with flash drives arise due to the fact that those memory cells that have never been written to are in an undefined state. An attempt to read them returns not zeros, but random data - the noise of the NAND Flash chip. Among this noise, just by the law of large numbers, there may be byte sequences coinciding with known file headers. Therefore, data recovery programs when working in a sector-by-sector mode (deep analysis) often "find" deleted files where they never were.
Copy or fake?
Qualitative collection of information is characterized by the reproducibility (verifiability) of its results. This is only possible with non-destructive and accurate data copying. However, even among specialized "forensic" programs for creating images, there are errors.For example, forensics often used (and continues to be used in some places) the console utility dcfldd, developed by the Computer Security Forensic Laboratory (DCFL), a division of the Center for Defense Against Cybercrime in Lintikam, Maryland. It is an extended version of the program ddthat makes a bit-by-bit copy of the file system. If a read error occurs while dcfldd is running, then all subsequent sector numbers in the image will be offset. Support for dcfldd was discontinued in 2006 and the bug remains unpatched.
The created copy may also be incomplete in the event of a memory dump. Most utilities write only the contents of RAM, ignoring the paging file. Therefore, in addition to the standard dump, it makes sense to make a copy of pagefile.sys. It is convenient to use the Forensic Toolkit Imager utility for this. It is a free part of Access Data's paid Forensic ToolKit, a powerful data preview and visualization tool used to retrieve evidence from running Windows machines.
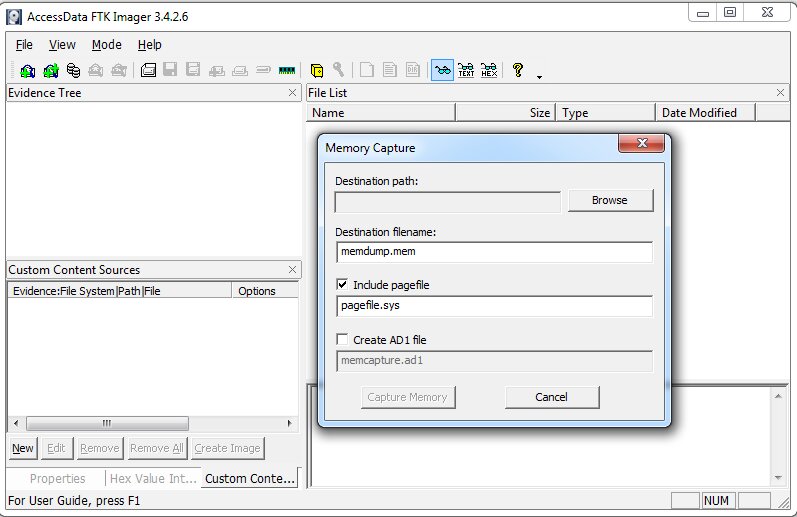
Dumping along with pagefile.sys
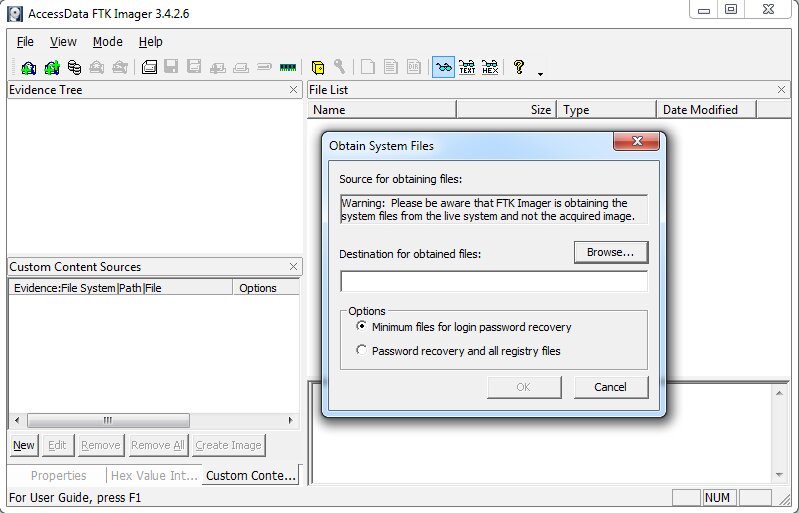
Getting system files
Additionally, FTK Imager allows you to get copies of locked SAM and SECURITY files without rebooting, make copies of the SOFTWARE and SYSTEM registry branches. The program can create bit-by-bit copies of data (both individual files or folders, and entire disks) without modifying the original. With its help, it is convenient to view all physically available files, including deleted, but not yet overwritten.
We create images
Even if at the current stage you do not intend to study them, it is still better to play it safe. The preservation of complete information will be required for a deeper study of the incident in the future, when its main consequences have already been eliminated in the working system.
Any distribution kit for forensics will require some "peeling". That is why the article deals with the main problems and methods of solving them. There is no generally accepted standard here. In real lawsuits, forensic scientists constantly balance between the purity of the methodology and the speed of collecting evidence.
What type of CI do you think is the most common today?
- Data theft and privacy breach
- Extortion using DDoS or ransomware
- Infection with hidden miners
- NSD, deface and data substitution
- Another option (I will indicate in the comments)
Popular Live distributions:
For computer forensics, dozens of live CDs / USBs with big titles have been created. Most of them turned out to be the same type of clones based on Knoppix, Ubuntu and, less often, other operating systems. Here we will only mention modern and well-proven ones. Let's start with the free ones.CAINE
The Italian distribution kit CAINE (Computer Aided Investigative Environment) is based on Ubuntu 16.04. It is available in 32-bit and 64-bit versions. The latest build is called CAINE 9.0 Quantum and was released in October 2017. The authors of CAINE have implemented the read-only mode through blockdevand offer a convenient tool for managing the permission of writing to disks. By default, the entry is locked and no partitions (except for the main one) are automatically mounted. However, CAINE does not prevent overwriting of service information on partitions with journaling filesystems and connected through the LVM logical volume manager.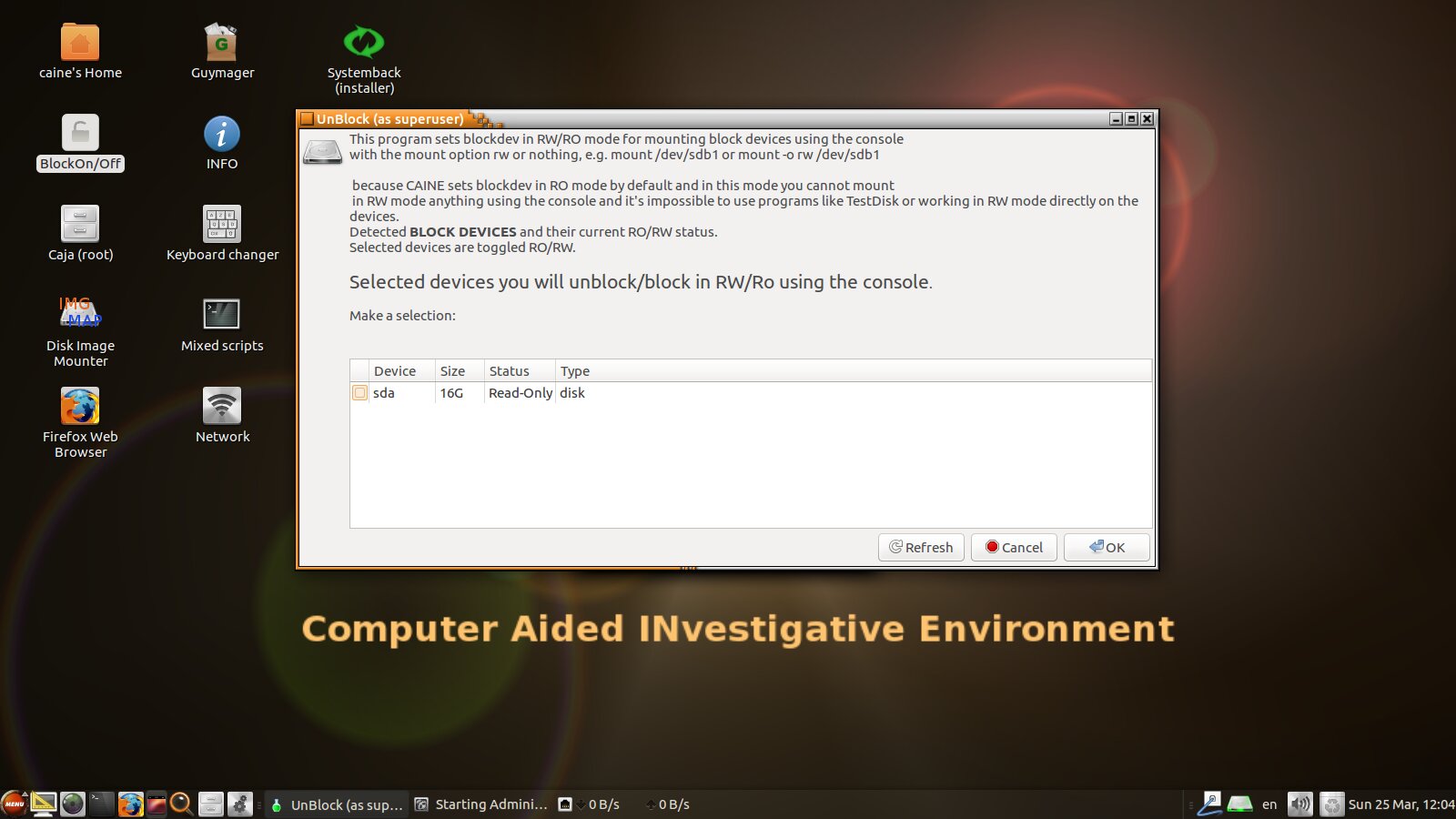
Write lock in CAINE
CAINE contains dozens of popular forensics utilities, organized into corresponding sections. They are used to study Windows and Linux systems. Typical analysis scenarios are partially automated. It also provides a semi-automatic compilation of the final report, which helps to quickly create a standardized evidence base for the trial.

A set of utilities in CAINE
CAINE incorporates well-known toolkits (NirSoft, Sleuth Kit, Autopsy and others), so there is no need to download them separately with it. Windows utilities are used in Live Forensic mode and were previously developed as part of the friendly Win-UFO project. After it closed, they were added to CAINE. Just unzip the image to a USB flash drive and run them separately or through the launcher.
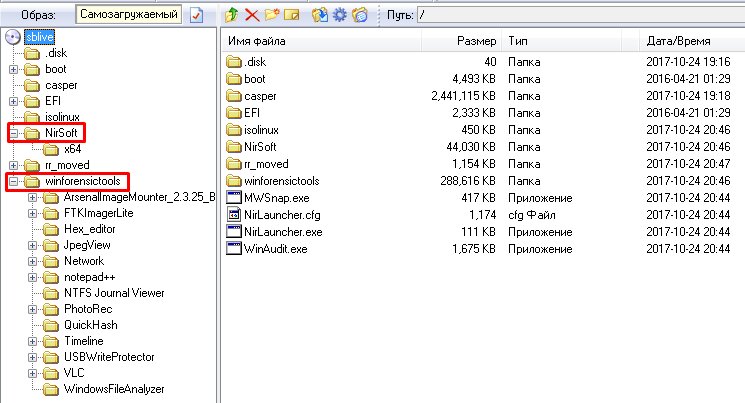
Windows analysis utilities
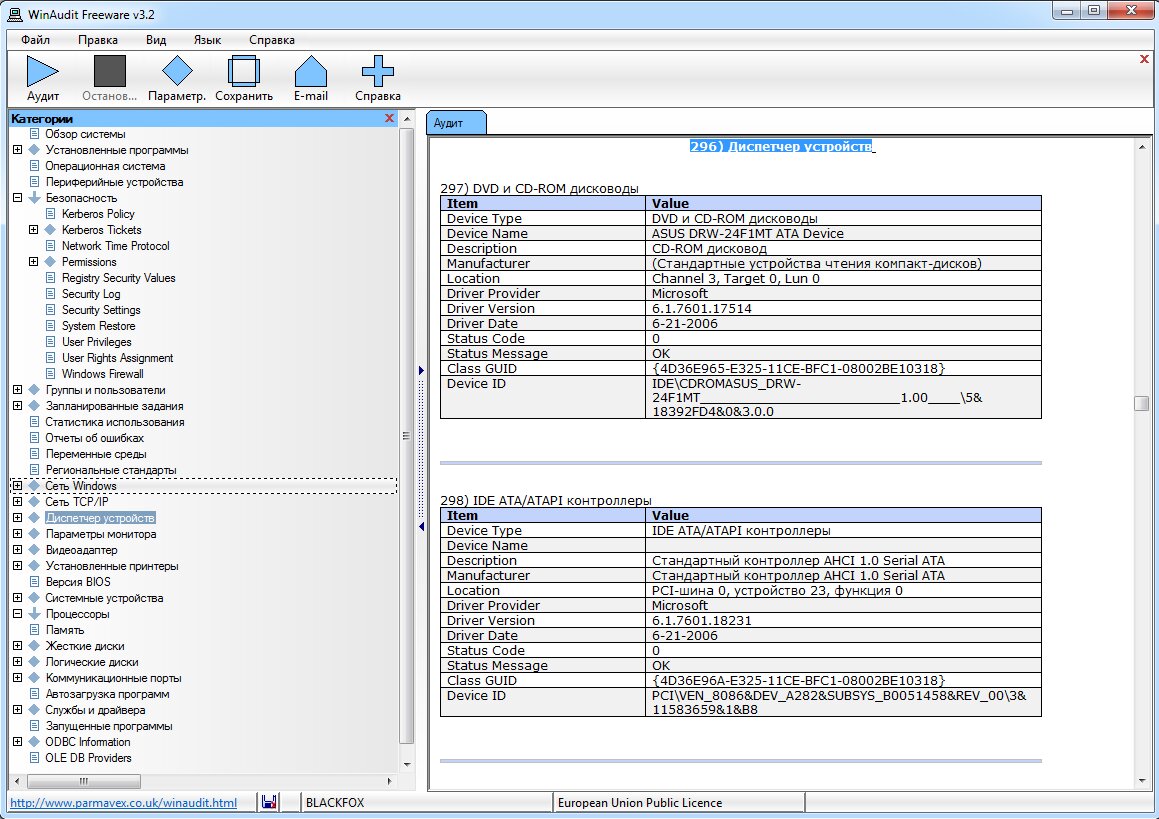
Detailed collection of system data in WinAudit
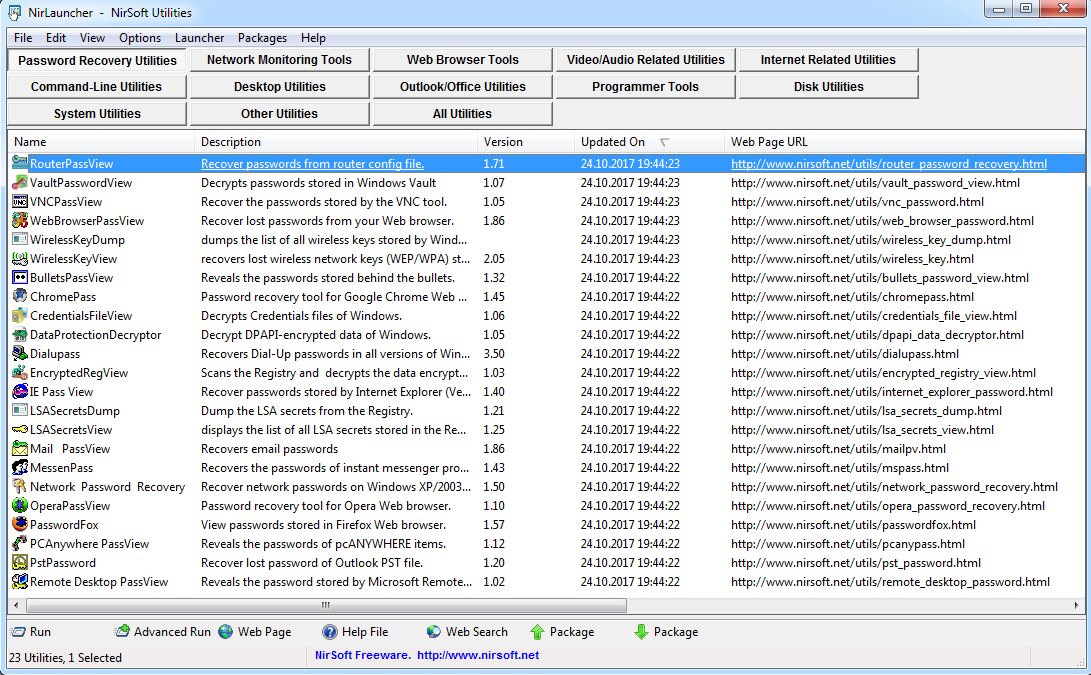
NirSoft Launcher as part of CAINE
DEFT
Another Italian Ubuntu-based distribution is DEFT (Digital Evidence & Forensic Toolkit). It is associated with a popular toolkit for dissecting Windows machines for live - DART (Digital Advanced Response Toolkit) and includes the utilities presented in it (run through the WINE emulator). This bundle does not work as stable as native applications, and in general DEFT is inferior to CAINE in functionality.The main focus in DEFT is on creating accurate disk images and advanced data integrity checking using different hash functions.

Hashing utilities in DEFT

Creating images in DEFT
The first version of DEFT was released in 2005. Since 2012, it has been developing under the auspices of the non-profit organization DEFT Association. The last (tested in this article) version is dated January 2017.
Parrot OS
Initially, the Italian (they agreed there, or what ?!) Parrot OS distribution was not focused specifically on forensics. His prerogative was anonymous web surfing and security auditing. After the forensic mode item was added to the boot menu, Parrot OS is successfully used to investigate CIs.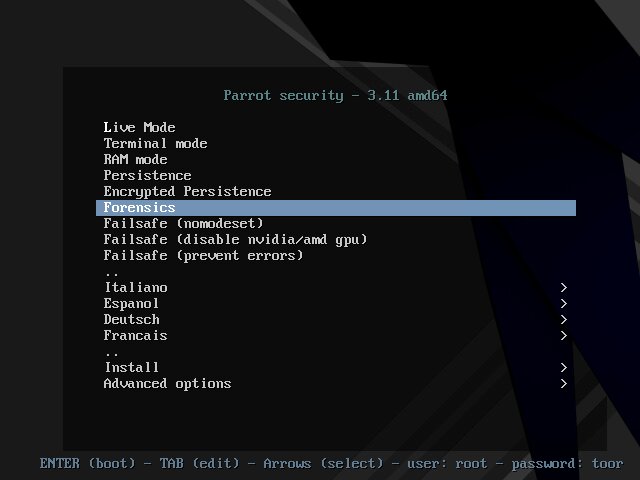
Parrot OS Forensic mode
Parrot OS is based on Debian and is actively developing. The latest version appeared just a month and a half ago. The operating system is very lightweight (it can run on systems with 256 MB of RAM), runs on processors with x86, x86-64 and ARM architecture, which allows it to be effectively used on Raspberry Pi and other single-board devices.
In terms of functionality, this is one of the best distributions. It has all the popular forensic tools for running systems and images, plus a powerful Kali Linux-style auditing package for anything.
Parrot OS Forensic Toolkit
The integrated Sleuth Kit and Autopsy (graphical interface to the Sleuth kit) simplify the reporting of CI investigations. They contain all the collected information by section, along with comments that the IT expert left in the course of their discovery.
Sumuri paladin
Sumuri PALADIN is one of the popular Sumuri forensics products. Also based on Ubuntu and trying to block write via blockdev (with the same partial success as CAINE).
Launching Paladin
Paladin includes a utility for creating and converting disk images of various formats. Thanks to the graphical interface, even a beginner can handle it.

Paladin Toolbox
The developers distribute the distribution as donationware with a recommended price of $ 25. You can specify another one (either more or less), but in any case you will have to make a purchase. Hint: fields are not validated. Just enter a valid zip code for the selected state or country.
Kali Linux - Forensic mode
When launched in this mode, Kali does not automatically mount any partition, including swap. All major forensic analysis tools are collected in kali-forensics-toolsa 3.1 GB metapack. This set of 84 utilities is great for building your own Kali image without anything extra.
Kali Forensic tools
Paid distributions:
SMARTLinuxAccording to many users, it most correctly blocks writing to the drive under study in default settings. Recommended for performing verifiable non-destructive analysis to provide reliable digital evidence in court.
EnCase Forensic
De facto, this set has become the benchmark for Interpol. Used to analyze memory dumps of computers and mobile devices, including smartphones and GPS trackers. Suitable for multi-professional collaboration.
Grml-Forensic
A very famous distribution based on Debian, because it is used for teaching forensics. When purchasing a license, access to the closed service Grml-Forensic Bug Tracking System is provided.
Grml-Forensic knows how to interact with X-Ways Forensics. This is an advanced version of WinHex with a bunch of additional features. It supports non-Windows file systems (HFS, XFS and others). Can read and write .e01 evidence files (EnCase images). Can perform separate analysis of files of different users. Has a built-in analyzer for memory dumps and metadata.
Helix
Presented in separate branches for live and offline analysis. For a quick memory dump, collecting passwords, lists of active processes and open ports, there is Helix Live Response. Helix3 Pro is offered for offline forensics. There is also a free version of Helix3, but it hasn't been updated since 2009.
What type of live distribution is best for forensics?
- Free, more specialists can use it
- Paid, it has better developer support
- LiveCD / USB are already poorly suited for forensic analysis
- Another option (I will indicate in the comments)
Excavations:
In the world of specialized distributions, things are changing rapidly. Therefore, I will list the once popular, but outdated today, just to save you time.COFEE (Computer Online Forensic Evidence Extractor)
A set of utilities, popular at the National White Collar Crime Center (NW3C), to collect evidence from computers running Windows XP and earlier. Developed by Anthony Fung, Senior Investigator for the MS Internet Safety Enforcement Team. In 2008-2009, Microsoft distributed it on flash drives to Interpol employees and all IT experts who participated in the arrest of the alleged criminals. COFEE accelerated the collection of digital evidence, including passwords, browser history, user folder contents and detailed system descriptions. Sometimes this eliminated the need to physically seize computers. Now it has been removed from the Microsoft site, but it is on torrents.The distribution kit itself does not contain anything specific except for the script for the data collection procedure. It's just a collection of well-known utilities (autoruns, netstat, ipconfig, pslist, and others) in a single shell.
FIRE (Forensic and Incident Response Environment)
It ceased to exist in 2004. That's all you need to know about him.
REPLACE (Inside Security Rescue Toolkit)
PlainSight
The first and last version 0.1 came out in September 2008. There have been a lot of similar attempts to make your own distribution kit focused on the tasks of forensic science.
Out of the ordinary
All distributions for forensics are quite specific, but there are also very highly specialized ones. For example, MacQuisition for macOS forensics. Prices for the Maquisition indulgence start at $ 1,400. In the sets discussed above, it is partly replaced by the volafox free Linux utility for examining the memory dump of "poppies". It is used (among other things) to search for keys loaded into RAM.The WinFE (Windows Forensic Environment) project is a bold attempt to do offline CI analysis from Windows. However, she was abandoned in 2012. Now for Live Forensic of Windows machines it is more convenient to use sets from NirSoft and Sysinternals, and offline analysis can be performed in Linux.

