A hybrid proxy network renders defenders useless and attackers invisible.
Chinese hackers have become more likely to use a vast proxy network of VPS servers and hacked online devices to conduct espionage.
Such proxy networks consist of Operational Relay Boxes (ORBS) and are administered by independent cybercriminals who provide access to them to government hackers. ORBs resemble botnets, but they can be a hybrid of rented VPS and compromised IoT devices.
ORB3 Network/SPACEHOP
Mandiant tracks several ORB networks, two of which are actively used by Chinese APT groups. One of these networks, called ORB3 / SPACEHOP, is actively used by the APT5 and APT15 groups for vulnerability exploration and exploitation.
SPACEHOP was used in December 2022 to exploit the CVE-2022-27518 vulnerability in Citrix ADC and Gateway, which the NSA linked to the APT5 group. Mandiant experts claim that SPACEHOP uses a relay server located in Hong Kong or China, and installs an open C2 infrastructure for managing nodes.
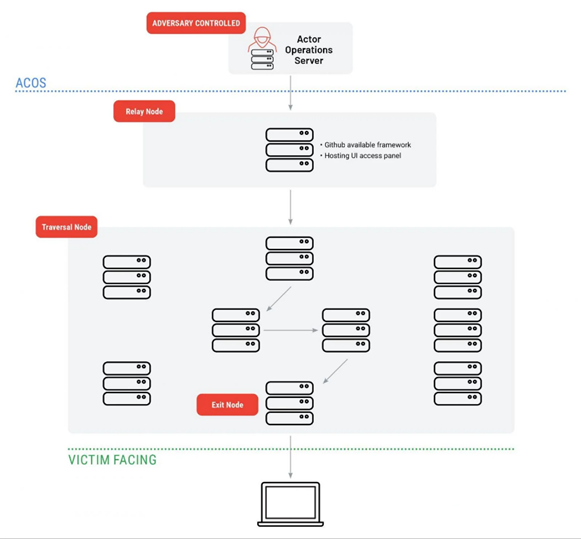
ORB3 Network/SPACEHOP
ORB2/FLORAHOX
The ORB2/FLAHOX network is a hybrid network consisting of a C2 server, compromised connected devices (routers and IoT), and a VPS that passes traffic through TOR and several compromised routers. Researchers believe that this network is used in espionage campaigns by various Chinese groups to mask the source traffic.
The network consists of several subnets that include devices compromised by FLOWERWATER and other router-based payloads. Despite the use of ORB2/FLORAHOX by various threat groups, Mandiant reports clusters of activity attributed to Chinese APT31/Zirconia that focus on intellectual property theft.
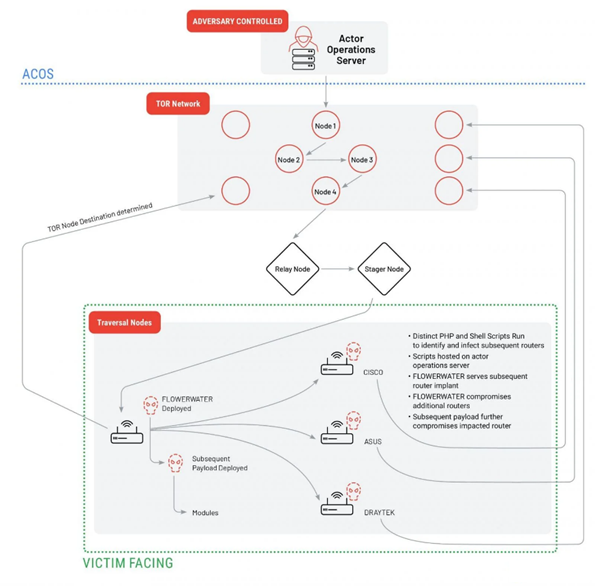
ORB2/FLORAHOX Network
Complexities of enterprise protection
The use of ORBS creates significant difficulties for enterprises, as they provide secrecy, stability and independence from the country's Internet infrastructure. Such networks are actively used by different groups for limited periods, which makes them more difficult to track and attribute.
According to Mandiant, an ORB node's IP address can last as little as 31 days, a feature of the ORB network that allows attackers to update significant parts of their compromised or leased infrastructure on a monthly basis.
Analyzing traffic from ORB networks is complicated by the fact that administrators use ASN number providers in different parts of the world. This makes networks more reliable and allows attackers to attack businesses from devices located in geographical proximity, which causes less suspicion when analyzing traffic.
With the increasing use of ORBS by hackers, protecting corporate environments is becoming increasingly challenging. Detection of such networks becomes more complex, attribution becomes more problematic, and enemy infrastructure indicators are less useful for defenders. With the growing threat of cyber espionage, businesses need to develop new defense strategies and adapt to new attack methods.
Chinese hackers have become more likely to use a vast proxy network of VPS servers and hacked online devices to conduct espionage.
Such proxy networks consist of Operational Relay Boxes (ORBS) and are administered by independent cybercriminals who provide access to them to government hackers. ORBs resemble botnets, but they can be a hybrid of rented VPS and compromised IoT devices.
ORB3 Network/SPACEHOP
Mandiant tracks several ORB networks, two of which are actively used by Chinese APT groups. One of these networks, called ORB3 / SPACEHOP, is actively used by the APT5 and APT15 groups for vulnerability exploration and exploitation.
SPACEHOP was used in December 2022 to exploit the CVE-2022-27518 vulnerability in Citrix ADC and Gateway, which the NSA linked to the APT5 group. Mandiant experts claim that SPACEHOP uses a relay server located in Hong Kong or China, and installs an open C2 infrastructure for managing nodes.

ORB3 Network/SPACEHOP
ORB2/FLORAHOX
The ORB2/FLAHOX network is a hybrid network consisting of a C2 server, compromised connected devices (routers and IoT), and a VPS that passes traffic through TOR and several compromised routers. Researchers believe that this network is used in espionage campaigns by various Chinese groups to mask the source traffic.
The network consists of several subnets that include devices compromised by FLOWERWATER and other router-based payloads. Despite the use of ORB2/FLORAHOX by various threat groups, Mandiant reports clusters of activity attributed to Chinese APT31/Zirconia that focus on intellectual property theft.

ORB2/FLORAHOX Network
Complexities of enterprise protection
The use of ORBS creates significant difficulties for enterprises, as they provide secrecy, stability and independence from the country's Internet infrastructure. Such networks are actively used by different groups for limited periods, which makes them more difficult to track and attribute.
According to Mandiant, an ORB node's IP address can last as little as 31 days, a feature of the ORB network that allows attackers to update significant parts of their compromised or leased infrastructure on a monthly basis.
Analyzing traffic from ORB networks is complicated by the fact that administrators use ASN number providers in different parts of the world. This makes networks more reliable and allows attackers to attack businesses from devices located in geographical proximity, which causes less suspicion when analyzing traffic.
With the increasing use of ORBS by hackers, protecting corporate environments is becoming increasingly challenging. Detection of such networks becomes more complex, attribution becomes more problematic, and enemy infrastructure indicators are less useful for defenders. With the growing threat of cyber espionage, businesses need to develop new defense strategies and adapt to new attack methods.
