Man
Professional
- Messages
- 3,223
- Reaction score
- 1,163
- Points
- 113
Computer viruses have been terrorizing all PC users for almost half a century, from office workers to officials and directors of international companies. Among the viruses, there are both scary encryptors and harmless "sheep" like USBToy, which displays quotes from the Bible when Windows starts. What can we say about advertising, mining and other unwanted software that can be attached to a useful application by a cunning distributor.
However, even computer viruses were once very small, simple and harmless, and their creators pursued slightly different goals. In this article, we will tell you about "undesirable" programs for personal computers of the end of the last century - Commodore Amiga, ZX Spectrum and Atari ST. It is hard to call them full-fledged viruses: their methods of distribution were quite primitive, and they "reproduced" very ineffectively. Some of them have sunk into oblivion: no names, no developers, only the memories of the "victims". Nevertheless, we managed to get some interesting information!
As is well known, most of the "people's" Amiga computers (models 500 and 500+ in particular) did not have a hard drive. The only ROM was a chip containing part of the computer's operating system, Kickstart. It was assumed that the second "half" of AmigaOS, Workbench, would be loaded by the user from a floppy disk. And games and some of the most heavyweight software bypassed the operating system startup altogether and were loaded directly from the media. Accordingly, there was nowhere to "exit" after playing: to launch another application, it was necessary to reboot the computer using the button on the power supply and insert a new floppy disk. Thus, a virus could be stored either on a floppy disk or in the RAM of a switched-on computer.
In November 1987, the Swiss Cracking Association team, "specializing" in removing protection from licensed software, released the world's first virus for Amiga. The malicious code, initially located in the boot sector of the floppy disk, was loaded into the RAM and wrote its body into the boot sectors of all unprotected disks that the user inserted into the computer.
The virus appeared as the following message on the screen:

Demonstration of the virus operation
The "virus text" was not displayed every time the infected disk was booted, but only once every 15 "warm" computer reboots. Due to this "incubation period", the probability of infecting a new device increased many times.
Despite its apparent harmlessness, the virus could cause real harm to programs whose disks had their own boot loaders. By rewriting itself to a new disk, the virus violated the boot loader code, as a result of which the program stopped starting.
Removing the virus was quite simple: in the case of disks containing only files, it was necessary to give the "install" command, after which the boot sector was completely rewritten. It was already somewhat more difficult to "cure" a game or program: it was necessary to find exactly the same, but "healthy" disk and rewrite the contents of its boot sector to the infected one.
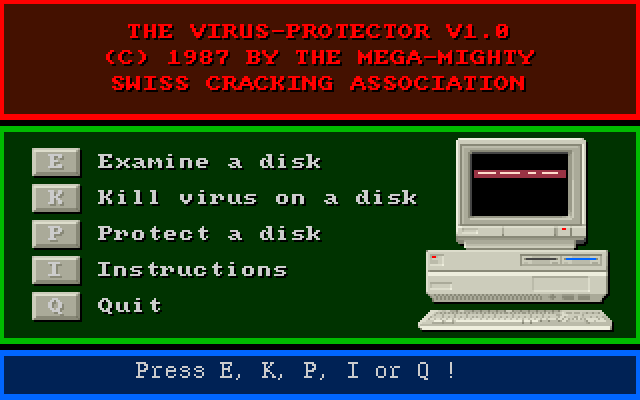
Another fact is extremely noteworthy: ASC was not just a virus, but a suicide virus: the developers “took care” of their victims and built a deactivation function into the program. To remove the virus from memory, you had to hold down the fire button 1 of the device connected to the first port during reboot. That is, either “fire” on the joystick or the left mouse button.
To combat the SCA virus, there was a special program created by a programmer nicknamed Saturnus The Invincible. Below you can see a demonstration of its interface.
The most inquisitive readers can even read the source code of the virus and some documents related to its authors on the SCA website.
Video Not For The Faint-Hearted: Master Virus Killer Takes Down SCA

A comic image of a virus on a ZX Spectrum
The phrase "virus for Spectrum" sounds pretty funny. If you think about it, that's true: who would need to write malicious programs for this little thing with 16-128 KB of RAM and a tape recorder under its arm? Nevertheless, there were some craftsmen.
In fairness, we should note that virus software for Spectrum was not particularly widespread due to the peculiarities of the computer's work with files and the lack of a full-fledged operating system (TR-DOS cannot be considered as such).
So, how exactly can you do harm to the owner of a Spectrum or its clone? For example, you can spoil a valuable disk. DZU-class programs, the so-called "Disk-Steaming Utilities", handled this task perfectly. The invention of this term (and at the same time the first program of this kind) according to some sources belongs to Stanislav Novikov.
The essence of DZU was as follows: the virus was disguised as a demo, during which the "side" code damaged the floppy disk in the drive: erased the zero track, deleted files or physically damaged the disk and brought it to an inoperative state.
It is noteworthy that the negative consequences of some DZU could be "cured" by an anti-DZU program from the same author. Still, despite the toxicity of certain individuals, Spectrum programmers in the USSR and the CIS were adequate people, and "virus" software was most often created not to harm users, but as an experiment or as a joke.
Another class of viruses, much more harmless, did not perform destructive actions, but "registered" itself to the basic bootloaders found on the diskette, increasing their size. Two such viruses are reliably known: Red October and Berezka. In the conditions of constant memory saving, even a slight increase in the size of programs significantly irritated Spectrum users.
In conclusion, we will provide a screenshot-quote from user Evgeny Muchkin from the site zx-pk.ru.
The very first worm virus, Signum, written for the Atari ST in 1987, infected up to 1-1.5 million computers in its “best days”. However, in 2020, neither a copy of it for live testing nor a detailed description of the mechanism of operation could be found. It is only known that, like many other viruses, it was loaded into the computer’s RAM and methodically copied to the input floppy disks without write protection.
Unlike Signum, its later brother, Evilnick, or simply Evil, turned out to be a little more tenacious. Now it is no longer possible to say for sure who its author was, but all traces lead to the UK, where it was discovered by a certain Jeremy Hughes. The virus was most widespread in Scandinavia. A notable feature of the virus was its method of disguise: Evil mimicked the system disk and remained unnoticed even by the popular Ultimate Virus Killer. The incubation period of Evilnick lasted quite a long time: the virus did not reveal itself until 100 disks had been infected.
After the 100th copy of itself was created, the "payload" included in the virus was launched, and the colors on the monitor were inverted. In the text of the virus itself, one could find a message from the developer: "EVIL! - A Gift from Old Nick".
To sum up, I would like to note one general tendency that persisted in the disparate community of the first virus makers. Many of them tended to believe that their programs were like living beings. They were able to reproduce, feed on the computer's power, interact with the user, cheat, hide, and die. Decades after these viruses were written, it is difficult to judge the true motives of their creators. Some wanted to spite their colleagues, others wanted to make a witty joke. For some, the very fact of writing a virus was akin to intellectual sports.
Technologies do not stand still: protection methods are being improved, operating systems are becoming more complex, hardware power is increasing, attack vectors are shifting. As a cloud provider, we will make a small remark on this matter.
As is known, about 80% of threats feel great in virtual environments, because such an environment practically does not create obstacles for the spread of malicious code, the emergence of virus epidemics and any other attacks. But antivirus software is getting smarter following viruses, and sometimes is a couple of steps ahead of them.
Currently, there are two main ways to ensure security in the cloud using specialized antivirus software: agentless protection and protection with a light agent. Agentless protection is currently only possible on VMware solutions: two additional ones are deployed on a physical server with a VM: SVM (dedicated security device) and NAB (network protection server). When implementing protection with a light agent, a light agent is installed on each virtual machine, which monitors everything that happens inside its VM.
This naturally leads us to the fact that each new virus, in order to survive, must be smarter, more cunning and more adaptable than the previous one. So, perhaps the first authors of viruses were not mistaken. They managed to release into the world the concept of a “living” organism capable of evolution. It’s just a pity that along with brains, these “monsters” also got teeth. They were so cute as children…
Source
However, even computer viruses were once very small, simple and harmless, and their creators pursued slightly different goals. In this article, we will tell you about "undesirable" programs for personal computers of the end of the last century - Commodore Amiga, ZX Spectrum and Atari ST. It is hard to call them full-fledged viruses: their methods of distribution were quite primitive, and they "reproduced" very ineffectively. Some of them have sunk into oblivion: no names, no developers, only the memories of the "victims". Nevertheless, we managed to get some interesting information!
Anyone who is even slightly familiar with these creations of human hands finds it difficult to shake off the idea that computer viruses are not just small programs, but real living creatures that are no different from their more material counterparts, waging a continuous war with humanity. And how can one think otherwise, if these programs are capable of independently moving, disguising themselves, reproducing and, finally, delivering crushing blows, regardless of state borders and geographical distances, while remaining invisible to humans.
Evgeny Golomolzin, introduction to the article "Viruses on IBM PC & ZX-SPECTRUM", 1997
SCA: The First Virus for the Commodore Amiga
As is well known, most of the "people's" Amiga computers (models 500 and 500+ in particular) did not have a hard drive. The only ROM was a chip containing part of the computer's operating system, Kickstart. It was assumed that the second "half" of AmigaOS, Workbench, would be loaded by the user from a floppy disk. And games and some of the most heavyweight software bypassed the operating system startup altogether and were loaded directly from the media. Accordingly, there was nowhere to "exit" after playing: to launch another application, it was necessary to reboot the computer using the button on the power supply and insert a new floppy disk. Thus, a virus could be stored either on a floppy disk or in the RAM of a switched-on computer.
In November 1987, the Swiss Cracking Association team, "specializing" in removing protection from licensed software, released the world's first virus for Amiga. The malicious code, initially located in the boot sector of the floppy disk, was loaded into the RAM and wrote its body into the boot sectors of all unprotected disks that the user inserted into the computer.
The virus appeared as the following message on the screen:
Something wonderful has happened
Your AMIGA is alive!!!
and, even better…
Some of your disks are infected by a VIRUS!!!
Another masterpiece of The Mega-Mighty SCA!!

Demonstration of the virus operation
The "virus text" was not displayed every time the infected disk was booted, but only once every 15 "warm" computer reboots. Due to this "incubation period", the probability of infecting a new device increased many times.
Despite its apparent harmlessness, the virus could cause real harm to programs whose disks had their own boot loaders. By rewriting itself to a new disk, the virus violated the boot loader code, as a result of which the program stopped starting.
Removing the virus was quite simple: in the case of disks containing only files, it was necessary to give the "install" command, after which the boot sector was completely rewritten. It was already somewhat more difficult to "cure" a game or program: it was necessary to find exactly the same, but "healthy" disk and rewrite the contents of its boot sector to the infected one.
Another fact is extremely noteworthy: ASC was not just a virus, but a suicide virus: the developers “took care” of their victims and built a deactivation function into the program. To remove the virus from memory, you had to hold down the fire button 1 of the device connected to the first port during reboot. That is, either “fire” on the joystick or the left mouse button.
To combat the SCA virus, there was a special program created by a programmer nicknamed Saturnus The Invincible. Below you can see a demonstration of its interface.

The most inquisitive readers can even read the source code of the virus and some documents related to its authors on the SCA website.
ZX Spectrum

A comic image of a virus on a ZX Spectrum
The phrase "virus for Spectrum" sounds pretty funny. If you think about it, that's true: who would need to write malicious programs for this little thing with 16-128 KB of RAM and a tape recorder under its arm? Nevertheless, there were some craftsmen.
In fairness, we should note that virus software for Spectrum was not particularly widespread due to the peculiarities of the computer's work with files and the lack of a full-fledged operating system (TR-DOS cannot be considered as such).
So, how exactly can you do harm to the owner of a Spectrum or its clone? For example, you can spoil a valuable disk. DZU-class programs, the so-called "Disk-Steaming Utilities", handled this task perfectly. The invention of this term (and at the same time the first program of this kind) according to some sources belongs to Stanislav Novikov.
The essence of DZU was as follows: the virus was disguised as a demo, during which the "side" code damaged the floppy disk in the drive: erased the zero track, deleted files or physically damaged the disk and brought it to an inoperative state.
It is noteworthy that the negative consequences of some DZU could be "cured" by an anti-DZU program from the same author. Still, despite the toxicity of certain individuals, Spectrum programmers in the USSR and the CIS were adequate people, and "virus" software was most often created not to harm users, but as an experiment or as a joke.
Another class of viruses, much more harmless, did not perform destructive actions, but "registered" itself to the basic bootloaders found on the diskette, increasing their size. Two such viruses are reliably known: Red October and Berezka. In the conditions of constant memory saving, even a slight increase in the size of programs significantly irritated Spectrum users.
In conclusion, we will provide a screenshot-quote from user Evgeny Muchkin from the site zx-pk.ru.
First viruses for Atari ST
The very first worm virus, Signum, written for the Atari ST in 1987, infected up to 1-1.5 million computers in its “best days”. However, in 2020, neither a copy of it for live testing nor a detailed description of the mechanism of operation could be found. It is only known that, like many other viruses, it was loaded into the computer’s RAM and methodically copied to the input floppy disks without write protection.
Unlike Signum, its later brother, Evilnick, or simply Evil, turned out to be a little more tenacious. Now it is no longer possible to say for sure who its author was, but all traces lead to the UK, where it was discovered by a certain Jeremy Hughes. The virus was most widespread in Scandinavia. A notable feature of the virus was its method of disguise: Evil mimicked the system disk and remained unnoticed even by the popular Ultimate Virus Killer. The incubation period of Evilnick lasted quite a long time: the virus did not reveal itself until 100 disks had been infected.
After the 100th copy of itself was created, the "payload" included in the virus was launched, and the colors on the monitor were inverted. In the text of the virus itself, one could find a message from the developer: "EVIL! - A Gift from Old Nick".
To sum up, I would like to note one general tendency that persisted in the disparate community of the first virus makers. Many of them tended to believe that their programs were like living beings. They were able to reproduce, feed on the computer's power, interact with the user, cheat, hide, and die. Decades after these viruses were written, it is difficult to judge the true motives of their creators. Some wanted to spite their colleagues, others wanted to make a witty joke. For some, the very fact of writing a virus was akin to intellectual sports.
Technologies do not stand still: protection methods are being improved, operating systems are becoming more complex, hardware power is increasing, attack vectors are shifting. As a cloud provider, we will make a small remark on this matter.
As is known, about 80% of threats feel great in virtual environments, because such an environment practically does not create obstacles for the spread of malicious code, the emergence of virus epidemics and any other attacks. But antivirus software is getting smarter following viruses, and sometimes is a couple of steps ahead of them.
Currently, there are two main ways to ensure security in the cloud using specialized antivirus software: agentless protection and protection with a light agent. Agentless protection is currently only possible on VMware solutions: two additional ones are deployed on a physical server with a VM: SVM (dedicated security device) and NAB (network protection server). When implementing protection with a light agent, a light agent is installed on each virtual machine, which monitors everything that happens inside its VM.
This naturally leads us to the fact that each new virus, in order to survive, must be smarter, more cunning and more adaptable than the previous one. So, perhaps the first authors of viruses were not mistaken. They managed to release into the world the concept of a “living” organism capable of evolution. It’s just a pity that along with brains, these “monsters” also got teeth. They were so cute as children…
Source
