Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,583
- Points
- 113
Poisoning of search results and pirated software-is this not the formula for perfect hacking?
Recently, cybercriminals have been using a new and highly sophisticated method of abusing certificates to spread malware. Its main purpose is to steal credentials and other confidential information. And in some cases, hackers may also target the theft of cryptocurrencies.
This campaign uses SEO poisoning to provide search results that lead to malicious pages and offer hacked software.
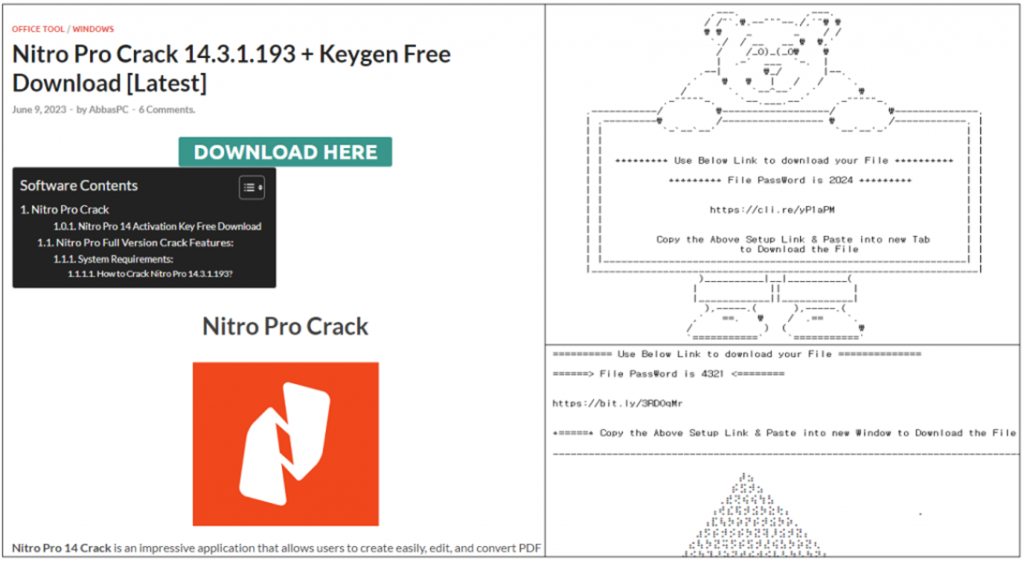
While illegal "cracks" are advertised in the foreground of the site, remote access Trojans known as LummaC2 and RecordBreaker (aka Raccoon Stealer V2) are delivered to victims computers in the background, researchers from South Korea's ASEC reported in their October 10 report.
In addition to being delivered via websites with illegal software, the researchers also noticed the spread of RecordBreaker via YouTube and other malware.
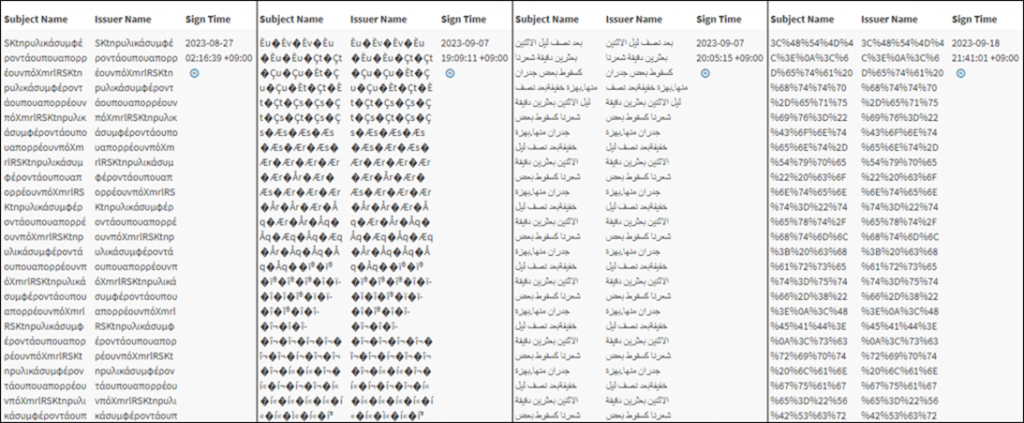
It is important to note that the malware uses non-standard certificates that contain unusually long strings in the "Subject Name" and "Issuer Name" fields, which makes them invisible to Windows systems. Captions include Arabic, Japanese, and other languages other than English, as well as special characters.
The last instance of the malware used in real attacks considered by the researchers consists of a string with malicious code intended for loading and executing PowerShell commands.
"Similar patterns were consistently distributed with little structural changes for more than two months, suggesting a specific intent behind these actions," the ASEC researcher wrote.
While such certificates probably wouldn't pass signature verification, they can still confuse and even circumvent some security measures. In general, certificate abuse has already become a somewhat common tactic used by threats.
LummaC2 and Raccoon Stealer are well known to security professionals. Once infected, they can transmit sensitive information, such as credentials stored in the browser, documents, files of cryptocurrency wallets, and so on.
Researchers at AhnLab Security strongly recommend that Windows users be careful when downloading software from the Internet, especially from sites that distribute illegal software. Even if you have already used this site before and you trust it.
Recently, cybercriminals have been using a new and highly sophisticated method of abusing certificates to spread malware. Its main purpose is to steal credentials and other confidential information. And in some cases, hackers may also target the theft of cryptocurrencies.
This campaign uses SEO poisoning to provide search results that lead to malicious pages and offer hacked software.

While illegal "cracks" are advertised in the foreground of the site, remote access Trojans known as LummaC2 and RecordBreaker (aka Raccoon Stealer V2) are delivered to victims computers in the background, researchers from South Korea's ASEC reported in their October 10 report.
In addition to being delivered via websites with illegal software, the researchers also noticed the spread of RecordBreaker via YouTube and other malware.
It is important to note that the malware uses non-standard certificates that contain unusually long strings in the "Subject Name" and "Issuer Name" fields, which makes them invisible to Windows systems. Captions include Arabic, Japanese, and other languages other than English, as well as special characters.

The last instance of the malware used in real attacks considered by the researchers consists of a string with malicious code intended for loading and executing PowerShell commands.
"Similar patterns were consistently distributed with little structural changes for more than two months, suggesting a specific intent behind these actions," the ASEC researcher wrote.
While such certificates probably wouldn't pass signature verification, they can still confuse and even circumvent some security measures. In general, certificate abuse has already become a somewhat common tactic used by threats.
LummaC2 and Raccoon Stealer are well known to security professionals. Once infected, they can transmit sensitive information, such as credentials stored in the browser, documents, files of cryptocurrency wallets, and so on.
Researchers at AhnLab Security strongly recommend that Windows users be careful when downloading software from the Internet, especially from sites that distribute illegal software. Even if you have already used this site before and you trust it.

