Europol detained criminals who emptied ATMs without using a plastic card - using the Tyupkin virus pre-loaded into the ATM.
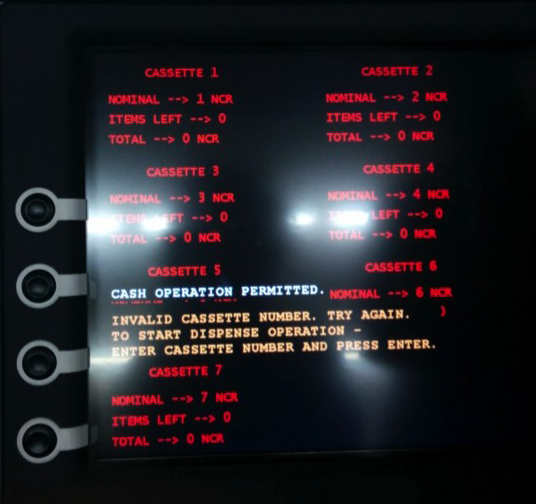
First, using a bootable CD, criminals gained access to computers installed inside ATMs running one of the older versions of Windows and infected them with malware. This virus had some peculiarities: it disabled the installed anti-virus protection, and also spent most of the week “hibernating”: it received commands from criminals at night - from Saturday to Sunday and from Sunday to Monday. The Trojan could also disable the local network so that bank services could not remotely connect to the ATM and check what was happening with it.
To obtain funds, the attacker approached the infected ATM and entered a specific PIN code, after which he gained access to the secret command menu, from where he could either begin the process of issuing money or perform operations with the Trojan itself, including deleting it.
Thus, in Eastern Europe, by infecting more than 50 ATMs, criminals received money worth hundreds of thousands of dollars without arousing any suspicion.
According to Kaspersky Lab, “So far, hackers have learned to infect ATMs of only a certain manufacturer, but nothing prevents them from going further and compromising other models. If manufacturers and banks do not take care of more advanced physical security of ATMs, similar stories will be repeated more often.”
Thus, the arrest of eight people caught as a result of searches in Romania and the Republic of Moldova may not stop this type of fraud; ATM manufacturers and financial institutions should be on alert: change all default passwords, and most importantly, review physical security measures your ATMs, because opening an ATM is not as difficult as it seems:
Well, don’t forget that recently there was another story with the use of ATMs in Eastern Europe, fraud in which also did not affect bank clients, namely: Hackers invented a new scheme for stealing money, stealing 250 million rubles.
Then the criminal received a payment card, topped it up and immediately withdrew the deposited money from an ATM, requesting a check. The transaction data was then sent to an accomplice who had access to the infected POS terminals. Through the terminals, according to the transaction code, the cancellation of cash withdrawal was generated. As a result, the card balance was instantly restored and the attacker had “canceled” money in his account. The criminals repeated these actions repeatedly until the ATMs ran out of cash, modifying their scheme after the banks corrected the error. Several court cases were opened against the perpetrators, the “money mules” were from London, Ukraine, Latvia and Lithuania.

First, using a bootable CD, criminals gained access to computers installed inside ATMs running one of the older versions of Windows and infected them with malware. This virus had some peculiarities: it disabled the installed anti-virus protection, and also spent most of the week “hibernating”: it received commands from criminals at night - from Saturday to Sunday and from Sunday to Monday. The Trojan could also disable the local network so that bank services could not remotely connect to the ATM and check what was happening with it.
To obtain funds, the attacker approached the infected ATM and entered a specific PIN code, after which he gained access to the secret command menu, from where he could either begin the process of issuing money or perform operations with the Trojan itself, including deleting it.
Thus, in Eastern Europe, by infecting more than 50 ATMs, criminals received money worth hundreds of thousands of dollars without arousing any suspicion.
According to Kaspersky Lab, “So far, hackers have learned to infect ATMs of only a certain manufacturer, but nothing prevents them from going further and compromising other models. If manufacturers and banks do not take care of more advanced physical security of ATMs, similar stories will be repeated more often.”
Thus, the arrest of eight people caught as a result of searches in Romania and the Republic of Moldova may not stop this type of fraud; ATM manufacturers and financial institutions should be on alert: change all default passwords, and most importantly, review physical security measures your ATMs, because opening an ATM is not as difficult as it seems:
Well, don’t forget that recently there was another story with the use of ATMs in Eastern Europe, fraud in which also did not affect bank clients, namely: Hackers invented a new scheme for stealing money, stealing 250 million rubles.
Then the criminal received a payment card, topped it up and immediately withdrew the deposited money from an ATM, requesting a check. The transaction data was then sent to an accomplice who had access to the infected POS terminals. Through the terminals, according to the transaction code, the cancellation of cash withdrawal was generated. As a result, the card balance was instantly restored and the attacker had “canceled” money in his account. The criminals repeated these actions repeatedly until the ATMs ran out of cash, modifying their scheme after the banks corrected the error. Several court cases were opened against the perpetrators, the “money mules” were from London, Ukraine, Latvia and Lithuania.
