Mutt
Professional
- Messages
- 1,457
- Reaction score
- 1,268
- Points
- 113
There are several excellent tools for capturing network traffic. So, Scapy and Wireshark are excellent solutions for organizing passive sniffing, and Scapy, moreover, is capable of sending additional packets.
In case you need to intercept traffic in the Man-in-the-Middle position, you can use such popular tools as Fiddler, Burp Suite or OWASP ZAP. These are good solutions, however, they only target the HTTP (S) protocols. But what software should you use if you need to modify generic non-HTTP traffic?
So, for example, if you need to analyze the traffic of the Telegram messaging system, which uses its own MTProto protocol, which runs directly on top of TCP / IP packets (in other words, HTTP or HTTPS is not used at all), then in this case the tools mentioned above will not work.
One of the tools with similar functionality is Ettercap. It provides a simple filtering interface to modify the transmitted data. Unfortunately, Ettercap requires filters to be written in its own language, which significantly limits the number of users who can fully use it for their needs.
Two other tools that you can also turn your attention to are Mallory and Trudy. Mallory software can be found on github and was mentioned back in 2010 at the Black Hat USA conference. Much water has flowed under the bridge since then, and at present the project seems to be abandoned. Therefore, in this article, we will focus on the second software toolkit - Trudy, authored by @kelbyludwig, and the source code for this software is also available on github (https://github.com/praetorian-code/trudy).
Interception and modification of traffic with Trudy
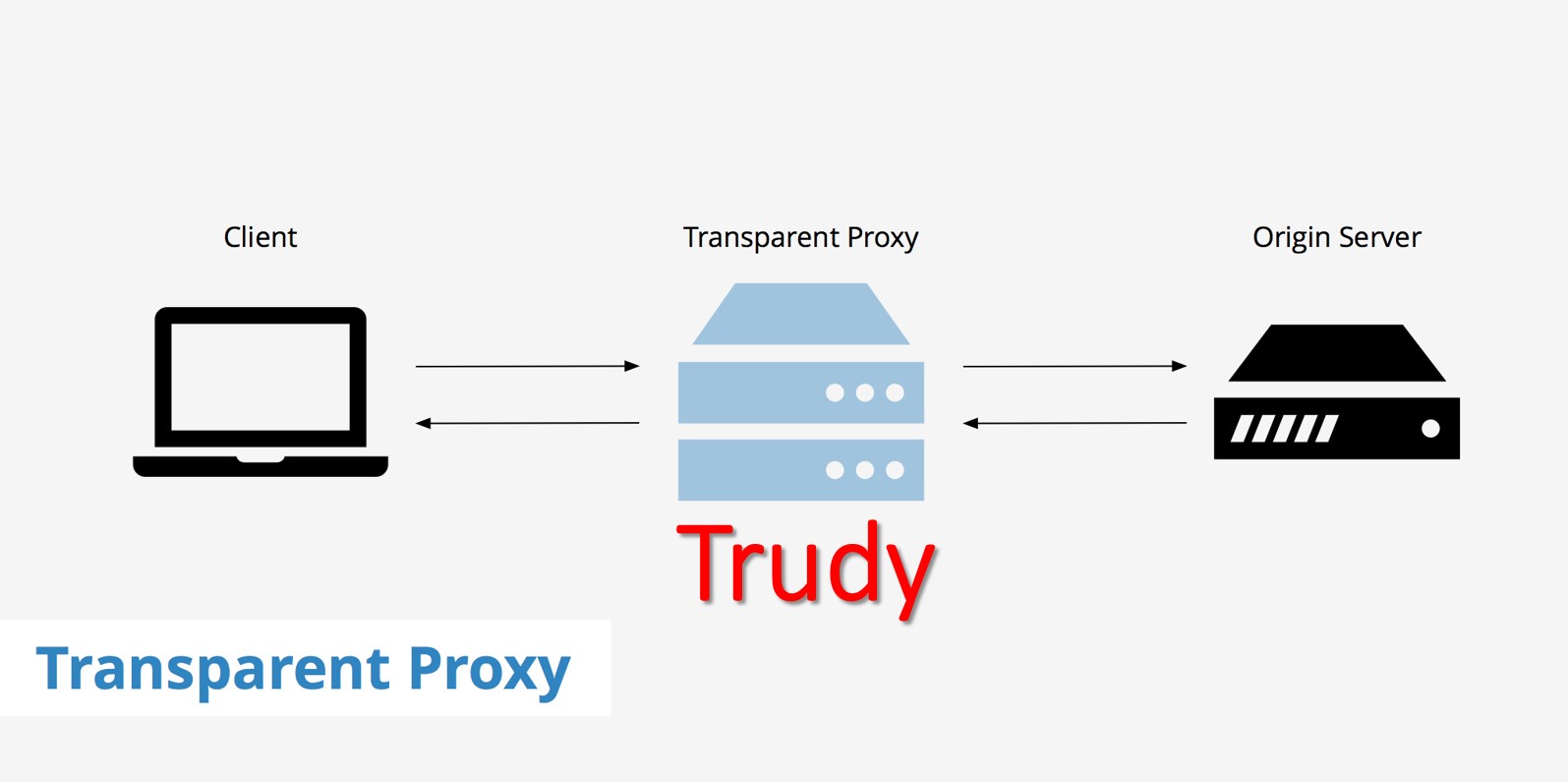
Trudy software can intercept and modify any TCP traffic, and its creators, when they worked on the project, were most likely inspired by the Mallory software mentioned just above. As the documentation says, Trudy is "a transparent proxy that can modify and drop traffic for arbitrary TCP connections." All traffic is routed through Trudy, which uses so-called modules to modify it.
Trudy Modules are functionality-oriented pre-programmed pieces of code that the user can modify to get the desired result. Trudy also provides interfaces for these modules . Since Trudy is written in Go, all modules and their interfaces must also be written in Go. A provisioned virtual machine is available to route traffic and properly configure the environment.
Configuring a virtual machine for traffic spoofing
The virtual machine installs all the necessary software and Trudy itself. It then routes all traffic to and from Trudy using the iptables utility. Trudy receives all traffic, modifies it based on the module used, and then sends the traffic back to the Internet (see Figure 1 for more details).
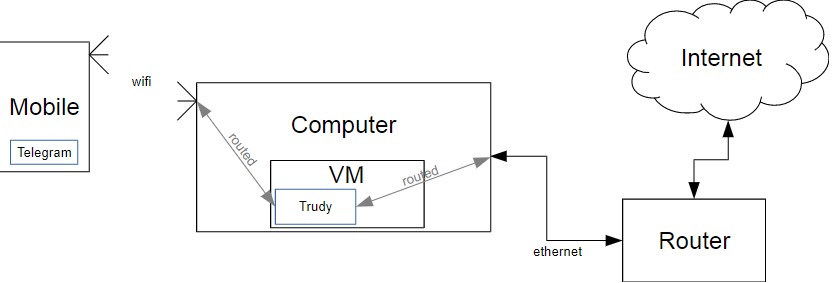
Figure 1. Trudy receives all traffic, modifies it based on the module being used, and then sends the traffic back to the Internet.
Trudy Modules
Using Trudy modules is pretty straightforward. Trudy calls certain methods in a fixed order, each of which is for one specific action:
An example of changing (spoofing) traffic using Trudy
Here's a simple example of a module that mangles all incoming traffic received from the IP address "139.59.129.86" on port 80. It does this by overwriting all TCP / IP payloads to zero. The main part of the module uses the DoMangle () and Mangle () functions (see Figure 2 for more details).
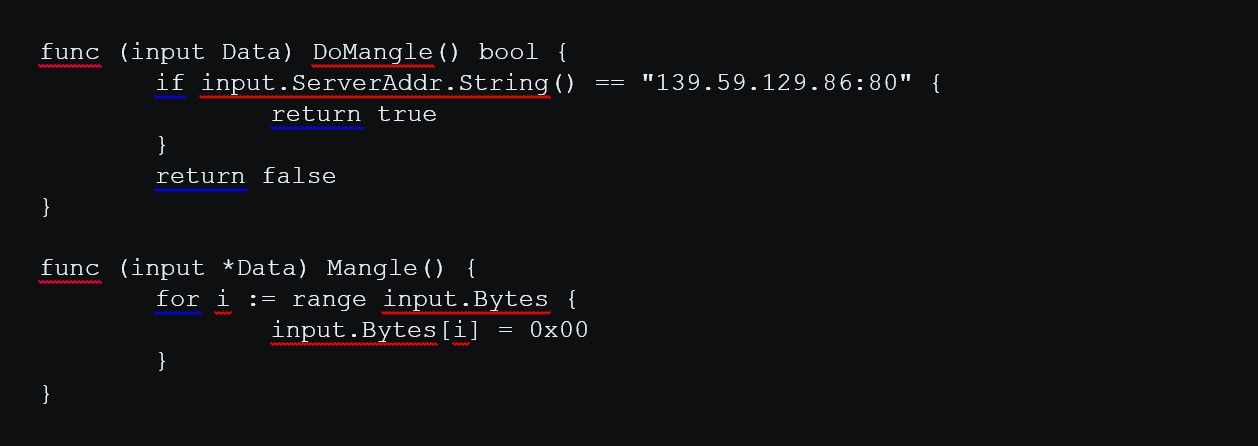
Figure 2. The main part of the Trudy module, which zeros all incoming traffic received from the IP address "139.59.129.86" on port 80, uses the DoMangle () and Mangle () functions
So, as you can see in the example, the DoMangle () function restricts the spoofing to the specified IP address, and Mangle () does all the actual work of turning that traffic to zeros.
After configuring Trudy using this example module, we can try to access the site with the specified IP address through a regular browser. The request will send fine, but the response will be overwritten with zeros. The browser will clearly not be able to parse the response and will eventually time out.
We can confirm this with WireShark. Figure 3 shows the modified answer. The blue line is the TCP / IP payload full of zeros, as expected. At the same time, the TCP / IP headers (some of the bits outside the blue frame) remained intact.
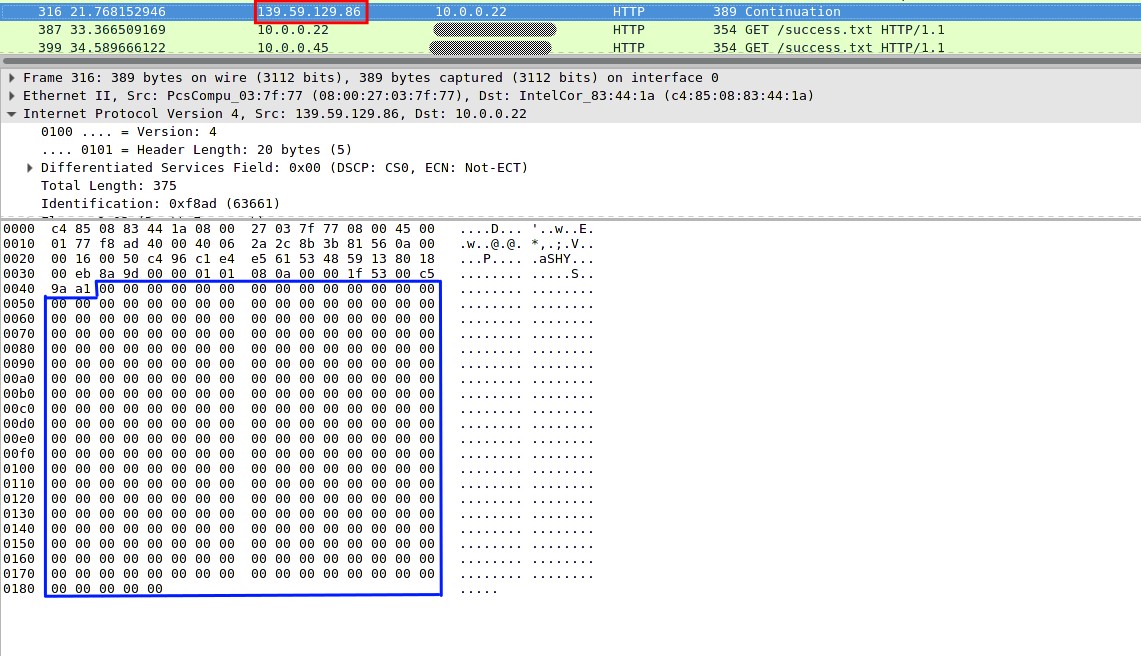
Figure 3. Testing the results of the Trudy module using WireShark.
You can find the whole module here: https://gist.github.com/tsusanka/8ce41c64f80836500410e490075b1df8
In addition to the functionality described above, it outputs information about events to the console so you have an idea of what is happening.
Likewise, you can easily use Trudy for many other tasks of intercepting and modifying TCP / IP traffic over the air.
In case you need to intercept traffic in the Man-in-the-Middle position, you can use such popular tools as Fiddler, Burp Suite or OWASP ZAP. These are good solutions, however, they only target the HTTP (S) protocols. But what software should you use if you need to modify generic non-HTTP traffic?
So, for example, if you need to analyze the traffic of the Telegram messaging system, which uses its own MTProto protocol, which runs directly on top of TCP / IP packets (in other words, HTTP or HTTPS is not used at all), then in this case the tools mentioned above will not work.
One of the tools with similar functionality is Ettercap. It provides a simple filtering interface to modify the transmitted data. Unfortunately, Ettercap requires filters to be written in its own language, which significantly limits the number of users who can fully use it for their needs.
Two other tools that you can also turn your attention to are Mallory and Trudy. Mallory software can be found on github and was mentioned back in 2010 at the Black Hat USA conference. Much water has flowed under the bridge since then, and at present the project seems to be abandoned. Therefore, in this article, we will focus on the second software toolkit - Trudy, authored by @kelbyludwig, and the source code for this software is also available on github (https://github.com/praetorian-code/trudy).
Interception and modification of traffic with Trudy

Trudy software can intercept and modify any TCP traffic, and its creators, when they worked on the project, were most likely inspired by the Mallory software mentioned just above. As the documentation says, Trudy is "a transparent proxy that can modify and drop traffic for arbitrary TCP connections." All traffic is routed through Trudy, which uses so-called modules to modify it.
Trudy Modules are functionality-oriented pre-programmed pieces of code that the user can modify to get the desired result. Trudy also provides interfaces for these modules . Since Trudy is written in Go, all modules and their interfaces must also be written in Go. A provisioned virtual machine is available to route traffic and properly configure the environment.
Configuring a virtual machine for traffic spoofing
The virtual machine installs all the necessary software and Trudy itself. It then routes all traffic to and from Trudy using the iptables utility. Trudy receives all traffic, modifies it based on the module used, and then sends the traffic back to the Internet (see Figure 1 for more details).

Figure 1. Trudy receives all traffic, modifies it based on the module being used, and then sends the traffic back to the Internet.
Trudy Modules
Using Trudy modules is pretty straightforward. Trudy calls certain methods in a fixed order, each of which is for one specific action:
- Deserialize () - Converts the raw payload into a known data structure (like HTTP).
- Drop () - If the return value is "true", the entire packet is dropped.
- DoMangle () - if the return value is "true", the Mangle () method is called.
- Mangle () - Modifies the payload.
- DoIntercept () - If true is returned, data is sent to the Trudy interpreter.
- DoPrint () - If the return value is "true", the PrettyPrint () method is called.
- PrettyPrint () - Prints data in a human-readable format.
- Serialize () - Converts data back to a raw payload if it was previously "deserialized".
- BeforeWriteToClient (p pipe.Pipe) is a function that is called before sending data to the client.
- BeforeWriteToServer (p pipe.Pipe) is a function that is called before sending data to the server.
- AfterWriteToClient (p pipe.Pipe) is a function that is called after sending data to the client.
- AfterWriteToServer (p pipe.Pipe) is a function that is called after sending data to the server.
An example of changing (spoofing) traffic using Trudy
Here's a simple example of a module that mangles all incoming traffic received from the IP address "139.59.129.86" on port 80. It does this by overwriting all TCP / IP payloads to zero. The main part of the module uses the DoMangle () and Mangle () functions (see Figure 2 for more details).

Figure 2. The main part of the Trudy module, which zeros all incoming traffic received from the IP address "139.59.129.86" on port 80, uses the DoMangle () and Mangle () functions
So, as you can see in the example, the DoMangle () function restricts the spoofing to the specified IP address, and Mangle () does all the actual work of turning that traffic to zeros.
After configuring Trudy using this example module, we can try to access the site with the specified IP address through a regular browser. The request will send fine, but the response will be overwritten with zeros. The browser will clearly not be able to parse the response and will eventually time out.
We can confirm this with WireShark. Figure 3 shows the modified answer. The blue line is the TCP / IP payload full of zeros, as expected. At the same time, the TCP / IP headers (some of the bits outside the blue frame) remained intact.

Figure 3. Testing the results of the Trudy module using WireShark.
You can find the whole module here: https://gist.github.com/tsusanka/8ce41c64f80836500410e490075b1df8
In addition to the functionality described above, it outputs information about events to the console so you have an idea of what is happening.
Likewise, you can easily use Trudy for many other tasks of intercepting and modifying TCP / IP traffic over the air.

