Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,494
- Points
- 113
The Trojan turns the phones of government employees into a listening device.
The hacker group APT36 (Transparent Tribe )was seen using at least three Android apps that mimic YouTube to infect devices with a Remote Access Trojan called CapraRAT.
The campaign was discovered by the SentinelLabs research laboratory, which warned organizations and individuals associated with military and diplomatic structures in India and Pakistan to be extremely careful with YouTube clients hosted on third-party sites.
How CapraRAT works
Once installed on the victim's device, CapraRAT can collect data, record audio and video, and access confidential information. In essence, it is a tool for cyber espionage. Among the Trojan's features:
Malicious APKs are distributed outside of Google Play, and victims are most likely exposed to social engineering to download and install the Trojan. During installation, apps ask for a lot of risky permissions, which the victim can grant without suspicion, assuming that this is a regular YouTube client.
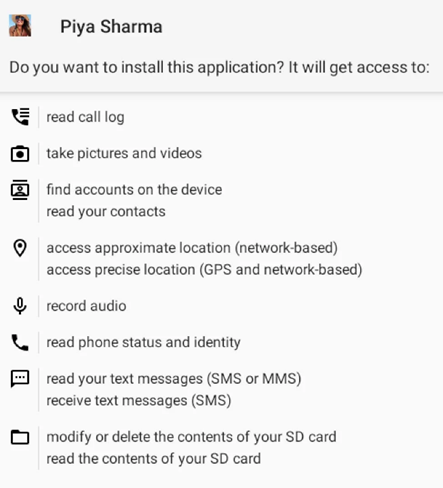
Requested App Permissions
SentinelLabs notes that the latest versions of CapraRAT have a number of improvements over the previous ones, which indicates the continuous development of malware. Despite relatively weak operational security, which makes hackers ' activities relatively easy to detect, the group is constantly updating its tools, which makes their threat more elusive.
SentinelLabs notes that while the group's weak operational security makes campaigns and tools easily identifiable, hackers ' continuous introduction of new applications provides the ability to constantly infect new victims.
The Transparent Tribe group has recently been linked to a number of other attacks targeting Indian government organizations using malicious versions of a two-factor authentication solution called Kavach.
CapraRAT was previously used in the APT36 cyber espionage campaign targeting Indian and Pakistani Android users. According to preliminary estimates, the victims were about 150 people. The malware could be downloaded from fake phishing websites, and the app itself is definitely a parody of WhatsApp by its interface and name.
The hacker group APT36 (Transparent Tribe )was seen using at least three Android apps that mimic YouTube to infect devices with a Remote Access Trojan called CapraRAT.
The campaign was discovered by the SentinelLabs research laboratory, which warned organizations and individuals associated with military and diplomatic structures in India and Pakistan to be extremely careful with YouTube clients hosted on third-party sites.
How CapraRAT works
Once installed on the victim's device, CapraRAT can collect data, record audio and video, and access confidential information. In essence, it is a tool for cyber espionage. Among the Trojan's features:
- Record audio and video using the device's microphone and cameras;
- Collecting SMS and MMS messages, as well as call logs;
- Initiating phone calls and sending SMS;
- Creating screenshots of the device screen;
- Change critical system settings, including GPS and network settings;
- Modification or deletion of files in the device's file system.
Malicious APKs are distributed outside of Google Play, and victims are most likely exposed to social engineering to download and install the Trojan. During installation, apps ask for a lot of risky permissions, which the victim can grant without suspicion, assuming that this is a regular YouTube client.

Requested App Permissions
SentinelLabs notes that the latest versions of CapraRAT have a number of improvements over the previous ones, which indicates the continuous development of malware. Despite relatively weak operational security, which makes hackers ' activities relatively easy to detect, the group is constantly updating its tools, which makes their threat more elusive.
SentinelLabs notes that while the group's weak operational security makes campaigns and tools easily identifiable, hackers ' continuous introduction of new applications provides the ability to constantly infect new victims.
The Transparent Tribe group has recently been linked to a number of other attacks targeting Indian government organizations using malicious versions of a two-factor authentication solution called Kavach.
CapraRAT was previously used in the APT36 cyber espionage campaign targeting Indian and Pakistani Android users. According to preliminary estimates, the victims were about 150 people. The malware could be downloaded from fake phishing websites, and the app itself is definitely a parody of WhatsApp by its interface and name.

