Lord777
Professional
- Messages
- 2,578
- Reaction score
- 1,536
- Points
- 113
Alternative versions of the messenger have put hundreds of thousands of devices at risk.
Kaspersky Lab specialists have identified a Trojan module in modifications of the popular WhatsApp messenger, which is actively distributed through Telegram channels. The spyware is called CanesSpy. Disguised as a regular messenger, the infected Android versions contain hidden tracking features.
This became known after a thorough analysis of the app's manifest, where inconsistencies in the original version were found: added a third-party service and receiver (receiver of broadcast messages) that are missing from the legitimate app.
A Broadcast Receiver that is configured to listen for system events, such as connecting the device to charging or receiving an SMS, activates the service that starts the spy module. The malicious code then communicates with the Command and Control (C2) server, which transmits information about the victim's device, including IMEI, phone number, and other identifiers. In addition, the spyware sends data about the victim's contacts and accounts every 5 minutes.
In the course of further work, the malware requests new commands from the C2 server at specified time intervals to perform actions on the infected device. Analysts found that the commands on the server were written in Arabic, which indicates a possible Arabic-language origin of the malware developer.
The investigation revealed that the main distribution channel of the modified WhatsApp is Telegram channels containing texts mainly in Arabic and Azerbaijani. The most popular channels have almost 2 million users. Channel creators were warned about the presence of malware in their content.
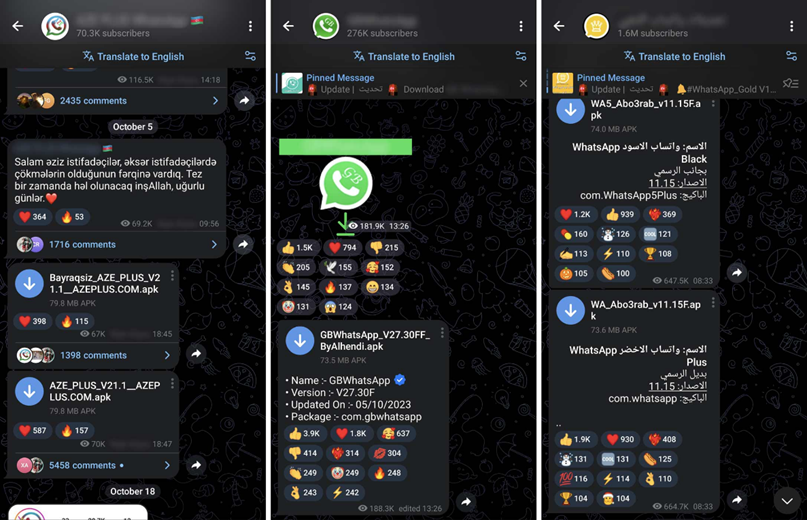
Malicious modifications available for download
Experts note that the spyware modules were activated from mid-August 2023, and all versions of the program downloaded from that time contained malicious code. However, in one of the channels, the latest version of the virus modification was replaced with the original one. In addition to Telegram channels, infected versions of the messenger are also distributed on sites that specialize in WhatsApp modifications.
Between October 5 and 31, Kaspersky Lab blocked more than 340,000 attack attempts via modified WhatsApp in more than 100 countries around the world. However, given the distribution methods, the actual number of installations of spyware modifications may be significantly higher. The top five countries with the highest number of attacks include Azerbaijan, Yemen, Saudi Arabia, Egypt and Turkey.
Users are strongly advised to avoid downloading instant messengers from unverified sources and use only official services to install applications.
Kaspersky Lab specialists have identified a Trojan module in modifications of the popular WhatsApp messenger, which is actively distributed through Telegram channels. The spyware is called CanesSpy. Disguised as a regular messenger, the infected Android versions contain hidden tracking features.
This became known after a thorough analysis of the app's manifest, where inconsistencies in the original version were found: added a third-party service and receiver (receiver of broadcast messages) that are missing from the legitimate app.
A Broadcast Receiver that is configured to listen for system events, such as connecting the device to charging or receiving an SMS, activates the service that starts the spy module. The malicious code then communicates with the Command and Control (C2) server, which transmits information about the victim's device, including IMEI, phone number, and other identifiers. In addition, the spyware sends data about the victim's contacts and accounts every 5 minutes.
In the course of further work, the malware requests new commands from the C2 server at specified time intervals to perform actions on the infected device. Analysts found that the commands on the server were written in Arabic, which indicates a possible Arabic-language origin of the malware developer.
The investigation revealed that the main distribution channel of the modified WhatsApp is Telegram channels containing texts mainly in Arabic and Azerbaijani. The most popular channels have almost 2 million users. Channel creators were warned about the presence of malware in their content.

Malicious modifications available for download
Experts note that the spyware modules were activated from mid-August 2023, and all versions of the program downloaded from that time contained malicious code. However, in one of the channels, the latest version of the virus modification was replaced with the original one. In addition to Telegram channels, infected versions of the messenger are also distributed on sites that specialize in WhatsApp modifications.
Between October 5 and 31, Kaspersky Lab blocked more than 340,000 attack attempts via modified WhatsApp in more than 100 countries around the world. However, given the distribution methods, the actual number of installations of spyware modifications may be significantly higher. The top five countries with the highest number of attacks include Azerbaijan, Yemen, Saudi Arabia, Egypt and Turkey.
Users are strongly advised to avoid downloading instant messengers from unverified sources and use only official services to install applications.
