Carding 4 Carders
Professional
- Messages
- 2,729
- Reaction score
- 1,521
- Points
- 113

IBM X-Force experts discovered the CamuBot banker, which appeared last month in Brazil and is different from most similar threats. CamuBot attacks a wide variety of companies and government agencies, but the main “weapon” of attackers is social engineering. Thus, the authors of the malware present their malware as a bank's security application, and themselves as its employees. As a result, the victims install the banker themselves, under the strict guidance of a human operator who gives them instructions over the phone.
IBM X-Force analysts explain that criminals carefully prepare for each attack. They find companies and organizations that do business with a specific financial institution and prepare the malware, equipping it with the necessary branding and logos.
The attackers then call the target company, the employee most likely to know the credentials from the corporate bank account. Posing as employees of the bank the company works with, the criminals ask the victim to follow the link and check the status of a certain bank security module. The site, diligently disguising itself as legitimate, will inform the victim that the security software needs to be urgently updated. If the victim falls for the attackers and decides to download the updated security module (which also requires administrator privileges), it will download the CamuBot Trojan.
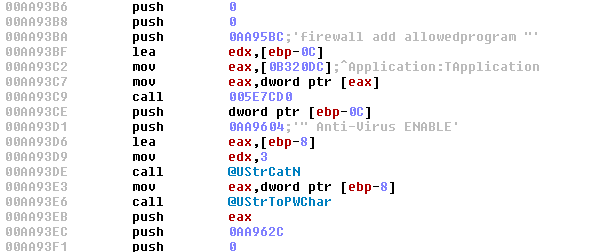
The banker, still posing as the banking security module, will add itself to the trusted Windows Firewall applications, as well as install a SOCKS proxy (SSH) and allow port forwarding. This two-way tunnel will allow attackers to use the victim's IP address when it comes to infiltrating the company's bank account.
Criminals also obtain credentials from a bank account using social engineering. The fact is that after installing CamuBot, it will open a fake bank website, where the user will be prompted to log in, after which this information will fall into the hands of the attackers.
IBM X-Force experts emphasize that the developers of CamuBot and this complex scheme even provided for the possibility of a collision with two-factor authentication. If the bank account is additionally protected by 2FA and biometrics, the malware is also able to install the drivers necessary for the authentication device to work, after which the operator will ask the victim by phone to provide a temporary code or provide a fake bank employee with remote access.