Father
Professional
- Messages
- 2,602
- Reaction score
- 832
- Points
- 113
Victims of malware risk being left not only without data, but also without chakra.
Cybersecurity experts are warning of a new wave of attacks on Portuguese-speaking countries using fake Adobe Reader installers to distribute a multi-functional malicious software called Byakugan.
The attack starts with a PDF file, which when opened displays a blurry image and prompts the victim to download a third-party application to view its contents.

Fake notification (translated from Portuguese)
According to researchers from Fortinet, clicking on the label loads the installer that initiates the infection process. Information about this campaign was first published by the ASEC Cyber Intelligence Center last month.
The attack technique involves using techniques such as DLL Hijacking and bypassing Windows User Account Control (UAC) to download a malicious DLL file, which in turn activates the underlying malicious code. The process also involves the legitimate installer of the Wondershare PDFelement PDF reader.
The binary file is able to collect system metadata and transmit it to the management server, as well as load the main module "chrome.exe", which also acts as a management server for receiving files and commands.
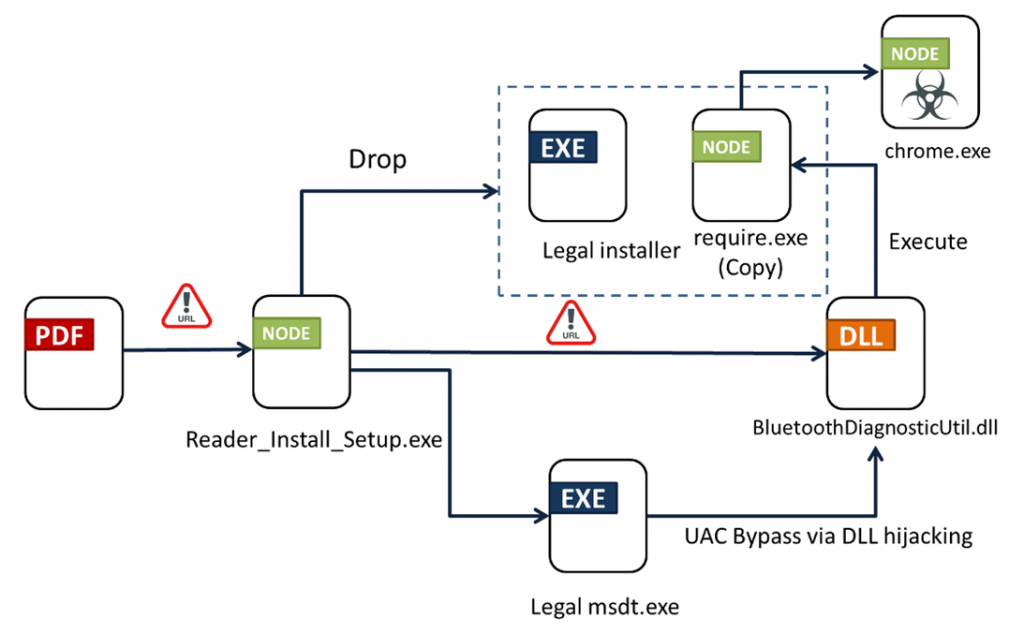
Full attack pattern
Byakugan is based on node.js and includes several libraries that are responsible for various functions: establishing persistence in the system, monitoring the user's desktop using OBS Studio, capturing screenshots, downloading cryptocurrency miners, logging keystrokes, inventory and downloading files, and stealing data stored in web browsers.
When analyzing malware connections, researchers can launch the Byakugan web control panel, which greets uninvited guests with an authorization screen. In the corner of the open tab, you can see an icon of a ninja with white eyes, which is an obvious reference to the anime "Naruto". Actually, just like the name of the malware itself.
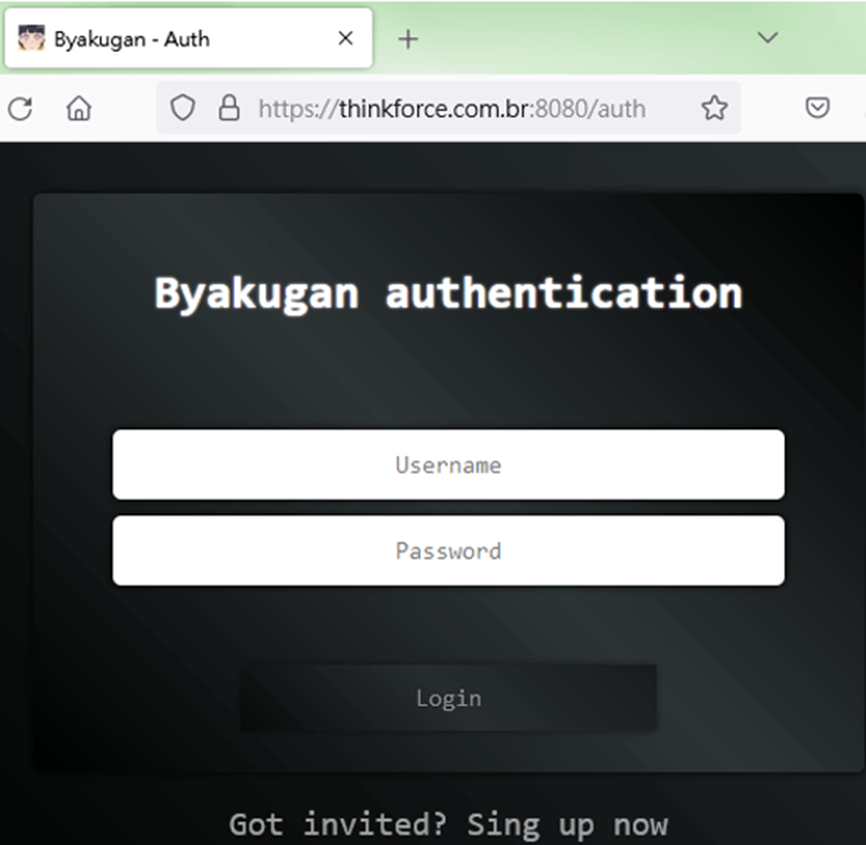
Malware Authorization Panel
Fortinet notes the growing trend of using fully legitimate components in ransomware software, which complicates the process of analyzing and detecting threats.
We wrote about a similar threat with a fake installer just today: the US oil and gas corporate sector faced phishing attacks containing a notification of an accident, the person involved in which was allegedly the victim, or rather her car. In the uploaded PDF file, hackers also use background blur and a fake notification that mimics Adobe Reader to force the user to click on the link and install the Rhadamanthys malware that collects data from the infected system.
Cybersecurity experts are warning of a new wave of attacks on Portuguese-speaking countries using fake Adobe Reader installers to distribute a multi-functional malicious software called Byakugan.
The attack starts with a PDF file, which when opened displays a blurry image and prompts the victim to download a third-party application to view its contents.

Fake notification (translated from Portuguese)
According to researchers from Fortinet, clicking on the label loads the installer that initiates the infection process. Information about this campaign was first published by the ASEC Cyber Intelligence Center last month.
The attack technique involves using techniques such as DLL Hijacking and bypassing Windows User Account Control (UAC) to download a malicious DLL file, which in turn activates the underlying malicious code. The process also involves the legitimate installer of the Wondershare PDFelement PDF reader.
The binary file is able to collect system metadata and transmit it to the management server, as well as load the main module "chrome.exe", which also acts as a management server for receiving files and commands.

Full attack pattern
Byakugan is based on node.js and includes several libraries that are responsible for various functions: establishing persistence in the system, monitoring the user's desktop using OBS Studio, capturing screenshots, downloading cryptocurrency miners, logging keystrokes, inventory and downloading files, and stealing data stored in web browsers.
When analyzing malware connections, researchers can launch the Byakugan web control panel, which greets uninvited guests with an authorization screen. In the corner of the open tab, you can see an icon of a ninja with white eyes, which is an obvious reference to the anime "Naruto". Actually, just like the name of the malware itself.

Malware Authorization Panel
Fortinet notes the growing trend of using fully legitimate components in ransomware software, which complicates the process of analyzing and detecting threats.
We wrote about a similar threat with a fake installer just today: the US oil and gas corporate sector faced phishing attacks containing a notification of an accident, the person involved in which was allegedly the victim, or rather her car. In the uploaded PDF file, hackers also use background blur and a fake notification that mimics Adobe Reader to force the user to click on the link and install the Rhadamanthys malware that collects data from the infected system.
