Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,579
- Points
- 113
Just 3 new campaigns have taken over the experience of the oldest SocGholish, occupying their own niches.
Recent cybersecurity research shows a growing number of cybercriminals disguising malicious downloads as fake browser updates.
Researchers from Proofpoint drew attention to the strengthening of tactics, inspired by the success of the SocGholish malware, which has been used for more than 5 years. Over the past 5 months, 3 large campaigns have been identified that use similar methods, but with different payloads.
There is a concern that, despite the fact that only malware is currently distributed, campaigns can be a great opportunity for Initial Access Brokers (IAB) to provide an effective way to infect end users with ransomware.
SocGholish is the oldest campaign that uses fake browser update notifications. The campaign is usually attributed to the TA569 group. In August, it became known that SocGholish contributed to the delivery of malware in 27% of infections. SocGholish was one of the top three malware uploaders, accounting for 80% of all attacks.
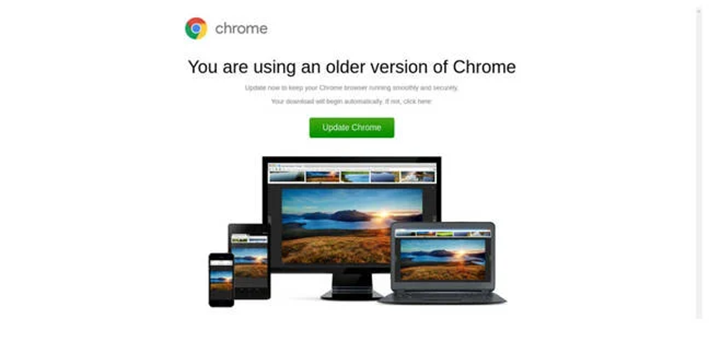
Typical bait of a fake browser update of the SocGholish campaign
All campaigns differ in the way malware is delivered, but they follow a three-step structure, adapting their notifications depending on the user's machine and browser. At the first stage, the compromised site is infected with malicious code. The second stage involves interaction between the malicious site and the user. At the third stage, the malware is finally delivered.
SocGholish operators have developed three different methods for moving from the first stage (infecting a legitimate site with malicious code) to the second stage (intercepting traffic between the attacker and the user).
Two of these methods involve the use of different Traffic Distribution Systems (TDS), which allow you to automatically redirect traffic from infected sites to the attacker's domains. The third method uses an asynchronous JavaScript request to redirect traffic to the domain where the malicious code is located. This method is particularly effective because it allows you to quickly and imperceptibly redirect the user to a malicious resource.
On the other hand, the RogueRaticate and ClearFake campaigns take a more direct approach. They use TDS only in the second stage of the attack. Instead of using complex redirection mechanisms, campaigns rely on direct interaction with the user through infected ad blocks or messages about the need to update the browser.
Thus, despite the common goal of infecting users devices with malware, various cybercrime groups use unique and diverse methods to achieve their goals.
Recent cybersecurity research shows a growing number of cybercriminals disguising malicious downloads as fake browser updates.
Researchers from Proofpoint drew attention to the strengthening of tactics, inspired by the success of the SocGholish malware, which has been used for more than 5 years. Over the past 5 months, 3 large campaigns have been identified that use similar methods, but with different payloads.
There is a concern that, despite the fact that only malware is currently distributed, campaigns can be a great opportunity for Initial Access Brokers (IAB) to provide an effective way to infect end users with ransomware.
SocGholish is the oldest campaign that uses fake browser update notifications. The campaign is usually attributed to the TA569 group. In August, it became known that SocGholish contributed to the delivery of malware in 27% of infections. SocGholish was one of the top three malware uploaders, accounting for 80% of all attacks.

Typical bait of a fake browser update of the SocGholish campaign
- RogueRaticate (FakeSG), was discovered in May 2023, but its activity is believed to have started as early as November 2022. This is the first major fake browser update campaign since SocGholish.
- ZPHP (SmartApeSG), discovered in June. Similar to RogueRaticate, ZPHP most often leads to the installation of the NetSupport RAT Trojan on the victim's computer.
- ClearFake, discovered in July. Proofpoint described ClearFake as a campaign that delivers infostilers and adapts baits not only to the user's browser, but also to their language, expanding the range of goals.
All campaigns differ in the way malware is delivered, but they follow a three-step structure, adapting their notifications depending on the user's machine and browser. At the first stage, the compromised site is infected with malicious code. The second stage involves interaction between the malicious site and the user. At the third stage, the malware is finally delivered.
SocGholish operators have developed three different methods for moving from the first stage (infecting a legitimate site with malicious code) to the second stage (intercepting traffic between the attacker and the user).
Two of these methods involve the use of different Traffic Distribution Systems (TDS), which allow you to automatically redirect traffic from infected sites to the attacker's domains. The third method uses an asynchronous JavaScript request to redirect traffic to the domain where the malicious code is located. This method is particularly effective because it allows you to quickly and imperceptibly redirect the user to a malicious resource.
On the other hand, the RogueRaticate and ClearFake campaigns take a more direct approach. They use TDS only in the second stage of the attack. Instead of using complex redirection mechanisms, campaigns rely on direct interaction with the user through infected ad blocks or messages about the need to update the browser.
Thus, despite the common goal of infecting users devices with malware, various cybercrime groups use unique and diverse methods to achieve their goals.

