Competition in privacy. Testing browsers that promise to leave no traces.
Installing a special secure browser is one of the ways to quickly and easily increase your privacy level. Only these browsers have recently bred like fleas on barbosk. Which of them are not afraid to go to fire, water, and adult sites, and which ones are better not to go further than Yandex at all? Today we will try to find the answer to this burning question.
Once on the "humpback" there was a special breed of peasants with a sly squint, from which ordinary people could buy at a reasonable price a CD with the address and telephone database of residents of Moscow and the rest of the Moscow region up to Kamchatka. Now much cooler guys are engaged in personal data trading: social networks compete in this business with search engines, which banks and other commercial structures lag behind by a small margin.
For tracking users, not only cookies and the notorious IP tracking are used, but also the so-called browser fingerprint, which includes data about the program version, OS bit depth, language settings, User Agent, screen resolution and other technical parameters of the system. There is also Evercookie technology, implemented using a special JavaScript application, and behavioral analysis, when special scripts collect information about user actions - web browsing time, scroll speed, clicks on links, and so on. It is not so easy to track or block all these functions.
In the settings of any modern browser, you can find the "Security" section, which contains parameters related to privacy and confidentiality. So, in Chrome there is a "safe browsing" mode for web pages with built-in protection against "potentially dangerous" sites, the ability to enable your own DNS service, as well as configure electronic keys and certificates. Opera has its own VPN, which looks more like a banal proxy, and the ability to prevent web sites from tracking outgoing traffic. Plus the same standard "protection against malicious sites". Firefox has built-in tracking protection and allows you to configure settings for storing passwords, cookies, and browser history.
However, all these technical tweaks are offset by the ability to install plugins that can do almost anything their developers want. Some plugins can send personal data to a remote server, track user actions, and embed ads in the web pages you view. In General, if elementary protection against surveillance is built into almost all modern browsers, then there is no protection from the user at all.
It is believed that secure, or, as they are also called, protected, browsers are a "clean" program without any whistles and add-ons, sharpened for maximum privacy. They allow you to work on the Internet, leaving a minimum of digital traces, block the transmission of telemetry and data collection. They are careful about cookies, browsing history, and more carefully store the data of forms that the user fills out, or do not store them at all. But the main thing is that most of them do not support the installation of third-party untested extensions, among which something bad can "stick" to the browser.
When it comes to secure web browsing programs, the first thing you think about is Tor Browser, which is well-known to everyone. That is why we will not consider it in this article. Moreover, Tor Browser is more often used as a tool for surfing the darknet. Instead, we will take a closer look at six alternative programs that their developers position as safe and secure browsers for Windows.
Trust, but check!
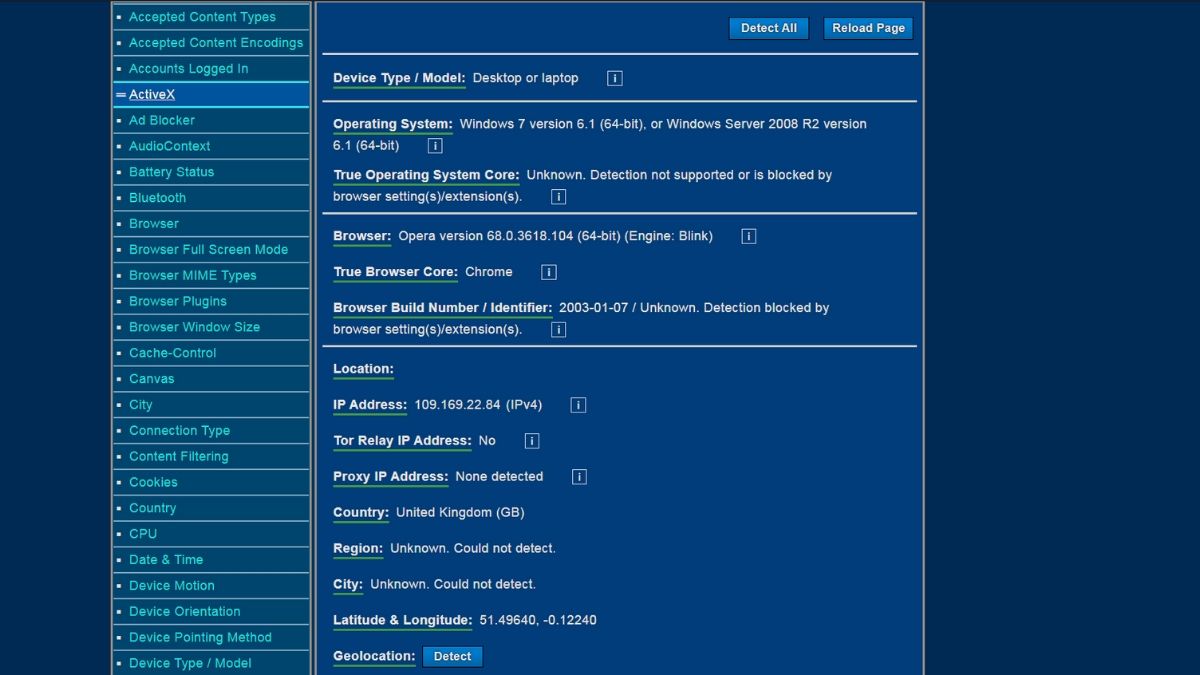
To find out whether to trust such programs, I decided not to invent complex stands and not to build a special laboratory. To compare secure browsers, a virtual machine with a freshly installed Windows and several online tests specially created to check the security level of such programs are quite enough. Here they are.
- Qualys Browser Check-checks vulnerabilities in the browser and tests settings for working with cookies. By default, you are asked to install a special plugin to pass the test, but you can do without it by using the link on the site.
- Cloudflare Browsing Experience Security Check-a test from the well-known company Cloudflare, checks the DNS, certificates, cookie settings used by the browser, and the presence of known vulnerabilities.
- Privacy Analyzer — a comprehensive browser check for possible data leaks. Tracking by IP address, browser fingerprint is checked, and privacy settings are tested.
- Panopticlick-third-party tracking cookies test and browser fingerprint tracking.
- Webkay is a service that shows all the information that your browser transmits to websites on the Internet.
So, the evaluation criteria were sorted out. Now let's move on to our experimental browsers - what results will they show us with the default settings? We'll find out now!
Comodo Dragon
Comodo Dragon is probably the most popular solution for safe surfing on the web after Tor Browser. Dragon claims to be a universal solution for those who are reluctant to wait half an hour for Tor to launch.
INFO
Comodo's reputation was once seriously damaged when in 2016 the company was caught that its products
were put on a VNC server without demand.
In fact, the guys from Comodo made as many as two secure browsers with the same set of functions, but on different engines: Comodo Dragon on the Chromium platform and ice Dragon based on Firefox. Among the announced features are built-in protection against malware, the use of secure DNS, blocking cookies and domain validation to combat phishing.
I downloaded both versions of Lizard at once and ran them on the virtual machine in turn. Externally, Dragon looks like the usual Chrome and runs at about the same speed on my virtual machine, it took an average of 4.5 seconds to load. From Chrome, the browser also inherited a love for RAM — with one window and one open tab, Comodo Dragon immediately launched five processes in the system and ate 90 MB.
Comodo Dragon, like any self-respecting Chromium, loves memory
Well, let's see what the tests say.
- Qualys Browser Check recognized the chrome browser in Comodo Dragon, and an outdated version, and then offered to download a newer version from the Google site.
- Cloudflare Browsing Experience Security Check determined that Dragon does not authenticate DNS server responses using DNSSEC and does not support SNI server name encryption when setting up a TLS connection-in theory, this could compromise privacy.
- The Privacy Analyzer test showed that Dragon successfully transmitted my IP address, location, browser version, OS bit rate, and screen resolution data to the remote host.
- Panopticlick demonstrated that the browser has a unique "fingerprint" and does not send the DNT (do not track) HTTP flag to the server, and this allows you to track the user. All other security tests on this site were passed by Comodo Dragon successfully.
- Finally, judging by the Webkay page, in addition to the version and bit rate of Windows, IP address and screen resolution, Dragon allows you to correctly recognize the battery level of my device and the processor type. The browser didn't allow you to scan your local network for available devices.
Comodo Ice Dragon looks not much different from its "non-food" counterpart. Firefox and Firefox, nothing special. It loads and works quite quickly: it took three seconds from clicking the icon to launching the app.
Comodo Ice Dragon is similar to regular Firefox:
- Qualys Browser Check did not find any shortcomings, the test was passed with absolute success.
- The Cloudflare Browsing Experience Security Check showed exactly the same result as in the previous case.
- According to the Privacy Analyzer, the browser sends out all the same data as its sibling, including the IP address and OS version.
- Panopticlick reported that the program does not block ad tracking attempts, does not send DNT, and has a unique "fingerprint".
- But Webkay gave a surprise: it turned out that the browser has a unique User Agent IceDracon 65.0.2and does not send any data about the hardware to the side at all, except for the processor bit rate. But, in addition to the external ipishnik, Webkay happily showed me the IP of the network interface of my locale. Using a special button on the site, I tried to scan devices available on the local network, but the search did not bring any results.
Waterfox
This is another security-focused Firefox clone that has versions not only for Windows, but also for macOS and Linux, and only the 64-bit version is available. In the "About" section of the official website, it says that the browser was made in 2011 by a sixteen-year-old schoolboy Alex Kontos, who is still updating and maintaining his brainchild to this day. The author claims that his application does not collect telemetry and sends out only data about the browser version and OS in order to receive updates on time. All others are confidential, the developer assures us, and are completely safe. Outwardly, the program is the most ordinary Firefox-so ordinary that it's even boring. It works and loads at the same speed, I didn't notice any significant differences with the usual "Fox".
Waterfox is also Firefox without any special external differences
Let's see how the tests will evaluate the student's craft.
- Qualys Browser Check-the test was passed successfully, no problems were detected.
- The Cloudflare Browsing Experience Security Check showed that Waterfox has problems with DDNSEC verification and the use of Encrypted SNI. In addition, the browser does not support TLS 1.3.
- Finally, Waterfox successfully failed all the Privacy Analyzer tests, and according to Panopticlick and Webkay, it leaked my IP address, processor type and bit depth, as well as screen resolution parameters, but wisely withheld all other data.
It is noteworthy that Waterfox is recognized as Firefox 56.0, while the current version of "Fox" today is 79.0. That is, the clone lags behind the original for about an eternity,and this may mean problems not with privacy, but with security.
Iron
Iron is not "irony", but
" iron» "iron", which seems to hint at the brutality and reliability of this browser. The hardware is built on the basis of Chromium, uses the latest versions of WebKit and V8, and also includes its own ad blocking component. It is noteworthy that the developer's site has a Russian version — however, it seems that it was translated into the great and mighty using the same Google Translate. According to the creators, Iron does not send telemetry to Google, does not send automatic bug reports, and does not update in the background, which saves traffic. It also has an "elegant design".
SRWare Iron is similar to Chrome a little less than completely. The program starts up in about 3.5 seconds and works with several open tabs quite quickly: I didn't notice any significant brakes behind it. It even seemed to me that this browser works faster than chromium in the Comodo build.
SRWare Iron:
- Qualys Browser Check complained to me about an outdated version of Google Chrome (83.0.4250) and informed me that it was not secure.
- The cloudflare test showed indicators similar to Comodo browsers - TLS 1.3 support is enabled, but claims about DNSSEC and Encrypted SNI.
- Panopticlick swore at the standard set of privacy problems (all tests were failed) and casually noticed that if SRWare Iron has some kind of ad blocker, it doesn't work.
- Privacy Analyzer and Webkay reported that the Hardware gives out data about the browser version, OS version and bit depth, IP address, and all information about the hardware (including the video card model, screen resolution, and battery status), but data about the local network remained a secret for Webkay.
Brave
The creators of the Brave browser claim that their chromium-based product, like no other, prevents tracking and possible data leaks. One of the features of Brave is the ability to send cryptocurrency payments to websites and content creators in the form
of Basic Attention Tokens, an Etherium-based cryptocurrency platform developed by Brave Software.
In 2017, when the platform was first launched, Brave Software sold tokens worth more than 35 million US dollars, and a total of 300 thousand tokens were distributed to new users of the platform in order to attract. Users of the Brave browser can earn tokens for viewing ads or pay content creators-either by sending microtransactions, or using the built-in Brave function, when a pre-set reward amount is automatically distributed among the owners of sites registered in the system, depending on how much time the user spent watching content.
There are versions of the browser for Windows, macOS, Linux, as well as Android and iOS. We'll only look at the first one, which, as you might expect, has a Chrome-inspired interface.
Brave cryptocurrency browser:
- Qualys Browser Check showed that the current version of Chrome is up-to-date and no updates are required.
- Cloudflare Test it didn't show anything new the Comodo and Iron browsers had the same result.
- And here Panopticlick it gave an unexpected result: as it turned out, Brave successfully blocks ads and automatic tracking, but it does not send DNT and has a characteristic "fingerprint" that can be used to calculate it.
- Privacy Analyzer and Webkay we were even more surprised: both sites did not show my IP address and location, although services like WhatIsMyIP detected it without any problems. The browser transmitted data about the OS version and bit depth, hardware (including the processor, graphics adapter, screen resolution, and battery status). As a User Agent, the program uses Chrome 84.0.4147.125.
Overall, this is a good result. Given the fact that the app works quite fast (although it feels slower than Iron), it is clearly worth taking a closer look.
Epic
This browser is developed by a company based in Bangalore (India) with a representative office in Washington. Here I could not bear to joke about the Indian code, but Epic, like its competitors, is based on Chromium, so the code there is Google. The developer of the program, Alok Bhardwaj, claims that Epic successfully blocks tracking, fingerprinting, annoying ads, cryptomining
, and voodoo magic. In addition to the Windows version, you can download the MacOS release on the site, and there are also links to Google Play and the App Store for downloading mobile versions.
It's just Epic of some sort
Immediately after launching the app, the user sees a terrible warning that some browser features, such as the built-in VPN, proxy, and ad blocker, need to be installed separately in the form of plugins available on a special page of the Epic Extension Store. How in this case Epic differs from the usual "Chrome", in which you can also configure a proxy and VPN using plugins, remains a mystery to me. Well, let's see what this browser can do out of the box with the default settings.
- Qualys Browser Check - no problems or comments.
- Cloudflare - a similar result to Comodo and Iron.
- Panopticlick-the browser successfully blocks ads and tracking attempts, but does not send DNT and has a characteristic "fingerprint".
- Privacy Analyzer-the test "hung up" on determining the IP address and geolocation, I did not wait for the result.
- Webkay - the service successfully detected my IP and OS version, but showed absolutely no data about the hardware, except for the processor bit rate. The browser is defined as Chrome 84.0.4147.105.
Looking at the name of the product, I was anticipating that I would be able to write about the "epic file", but surprisingly the browser proved to be quite good. Blocking ads and tracking, as well as a minimum of data transmitted to the outside, and all this without additional plugins is a pretty serious bid for success.
Looking at the name of the product, I was anticipating that I would be able to write about the "epic file", but surprisingly the browser proved to be quite good. Blocking ads and tracking, as well as a minimum of data transmitted to the outside, and all this without additional plugins is a pretty serious bid for success.
Dooble Web Browser
The development of this open source browser started twelve years ago. The Dooble interface is based on Qt, and the application itself is cross-platform: there are versions for FreeBSD, Linux, macOS, OS/2, and Windows, and in the form of a portable version for all platforms. The distribution kit can be downloaded from
GitHub as a ZIP archive containing the executable file and all the necessary libraries.
With the default settings, Dooble automatically deletes cookies, and the data stored in the program is encrypted (except for information about user settings). The browser uses a session model using temporary keys, and you can change the passphrase without losing any data. You need to create a master password in the settings when you first start Dooble, otherwise all data stored in the browser will be erased when it finishes. These features allow you to conditionally assign Dooble to the category of secure browsers.
On my virtual machine with Windows 10, Dooble flatly refused to start, swearing at the lack of some library, but on the host machine with Windows 7, it unexpectedly started working. The external design of the program can be described with the phrase "greetings from the nineties" - he even squeezed out a nostalgic tear for me.
Dooble-cross-platform browser based on Qt
Comparative tests yielded the following results.
- Qualys Browser Check - called Dooble an insecure version of Google Chrome-apparently because of the User Agent used by the browser.
- Cloudflare-similar results to Comodo, Iron, Epic, and Brave.
- Panopticlick - complete failure of the test on all points.
- Privacy Analyzer and Webkay - the browser transmitted the IP address, OS and hardware data, geolocation, and screen resolution. The program is presented to external services as Chrome 84.0.4147.163.
Perhaps Dooble is the fastest of all the browsers I tried in this experiment. Given the fact that it is presented as a portable version, the application can be very useful for systems where installing programs is difficult. The browser is also likely to appeal to BSD and Linux users. The functionality of the application in Windows 10 raises some doubts.
Conclusions
The results of the experiment were mixed. Contrary to expectations, the best results were shown not by the products of the famous Comodo company, but by quite modest Brave and Epic. However, Comodo Ice Dragon is also quite good - it sends out less data about the device than its counterpart. I would put Comodo Dragon in fourth place. Owners of devices with weak hardware and older versions of the OS may like Dooble, which is characterized by good performance. But Waterfox and Iron iron dived to the very bottom of our modest rating - they are worse than competitors to cope with advertising and blocking tracking.
Obviously, none of the programs listed in today's article can provide complete anonymity and security on the Internet. For real privacy, you need to use a VPN, disable script processing in the browser settings, and use encrypted containers for storing form data and passwords. In addition, there is a wide range of plug-ins aimed at improving the level of security when working on the network. But we'll talk about them in more detail another time.