Man
Professional
- Messages
- 3,221
- Reaction score
- 1,175
- Points
- 113
Group-IB estimated the damage to clients of Russian banks from a fraudulent scheme using fake payment systems at 3.15 billion rubles . This is stated in the new Hi-Tech Crime Trends 2021/2022 report “Big Score. Threats for the Financial Sector” , which analyzes current cyber threats to banks and financial organizations for the period from H2 2020 to H1 2021. The circle of victims in this scheme is quite wide - these are bank clients who lost their money, and issuing banks that approved the transaction, online services or stores whose websites were faked by attackers, and payment systems whose brands are illegally and without their knowledge used in the fraudulent scheme, Group-IB emphasizes.
To ensure the security of online payments, as well as two-factor authentication of the user, 3-D Secure technology was developed more than 10 years ago, supported by all payment systems - Visa, JCB International, AmEx and MIR (NSPK). Until now, it was synonymous with security, until fraudsters learned to forge 3-D Secure pages, according to the Group-IB report.
Fraud with imitation of payment confirmation pages was first noticed by Group-IB specialists at the end of 2020. It refers to the so-called Card-Not-Present fraud (CNP, card transactions without its presence). Every day in Russia, 11,767 payments were made by deceived users, a total of 8.6 million rubles per day, which led to damages of 3.15 billion rubles for the reporting period, based on the average transaction size multiplied by the number of identified transactions on phishing payment pages.
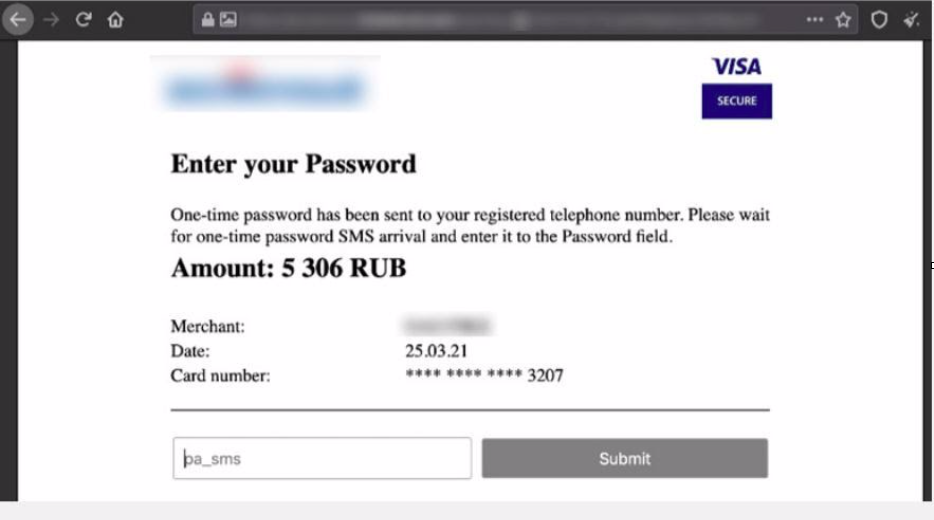 An example of a phishing 3-D Secure page located on a fraudster's domain
An example of a phishing 3-D Secure page located on a fraudster's domain
The danger of using counterfeit payment systems with a 3-D Secure page is that they are quite difficult to detect, they often contain logos of international payment systems Visa, MasterCard or Russian MIR and do not arouse suspicion in buyers who are trying to quickly make a purchase online. At the same time, for the issuing bank, the payment of its client looks legal, and in case of dissatisfaction, it will be extremely difficult for the client to return the money that he sent to the scammers through the supposedly "real" 3-D Secure page, confirming the transaction with a verification code from an SMS.
Group-IB experts urge people to be vigilant, especially on the eve of the New Year rush around buying gifts, some of which are purchased online.
In response, the fraudster's server received a service message (the so-called PaReq message) from the bank's P2P service, which contained encoded information about the payer's bank card, the transfer amount, and the name and details of the P2P service used.
The data in the service message (information about the payer's bank card, the transfer amount, the name of the acquirer and the online store) remains intact, but instead of a legitimate 3-D Secure page, the victim is redirected to a fake one - with fake information about the store.
At the same time, the fraudster's server initiates a request to the legitimate 3-D Secure server with the original service message. For the bank, this looks as if the user personally transferred funds to the fraudster's card through the bank's P2P service. The bank sends the cardholder an SMS code to confirm the payment, which the user enters on the phishing 3-D Secure page. As a result, the SMS code received by the fraudster's server from the fake 3-D Secure page is used to request a request to the legitimate server to confirm the fraudulent payment.
Group-IB experts predict that, most likely, as was the case with a number of other fraudulent schemes, “fake” payment systems will become widespread outside of Russia. The danger of the scheme is that transferring money to fraudsters’ accounts looks absolutely legal for banks.
Source
To ensure the security of online payments, as well as two-factor authentication of the user, 3-D Secure technology was developed more than 10 years ago, supported by all payment systems - Visa, JCB International, AmEx and MIR (NSPK). Until now, it was synonymous with security, until fraudsters learned to forge 3-D Secure pages, according to the Group-IB report.
Fraud with imitation of payment confirmation pages was first noticed by Group-IB specialists at the end of 2020. It refers to the so-called Card-Not-Present fraud (CNP, card transactions without its presence). Every day in Russia, 11,767 payments were made by deceived users, a total of 8.6 million rubles per day, which led to damages of 3.15 billion rubles for the reporting period, based on the average transaction size multiplied by the number of identified transactions on phishing payment pages.

The danger of using counterfeit payment systems with a 3-D Secure page is that they are quite difficult to detect, they often contain logos of international payment systems Visa, MasterCard or Russian MIR and do not arouse suspicion in buyers who are trying to quickly make a purchase online. At the same time, for the issuing bank, the payment of its client looks legal, and in case of dissatisfaction, it will be extremely difficult for the client to return the money that he sent to the scammers through the supposedly "real" 3-D Secure page, confirming the transaction with a verification code from an SMS.
Group-IB experts urge people to be vigilant, especially on the eve of the New Year rush around buying gifts, some of which are purchased online.
Scam step by step: how the scheme works
A multi-stage scheme with a fake payment system is difficult to implement and difficult to detect for most classic anti-fraud solutions, experts say. Attracted by fraudulent advertising, spam mailings, ads on bulletin boards, the buyer goes to a phishing page of an online store, marketplace or online service. Having selected a product or service, the victim enters the details of his bank card in the payment acceptance form on the fraudulent resource. The data goes to the fraudster's server, from where a request is made to the P2P services of various banks, indicating one of the fraudster's cards as the recipient.In response, the fraudster's server received a service message (the so-called PaReq message) from the bank's P2P service, which contained encoded information about the payer's bank card, the transfer amount, and the name and details of the P2P service used.
The data in the service message (information about the payer's bank card, the transfer amount, the name of the acquirer and the online store) remains intact, but instead of a legitimate 3-D Secure page, the victim is redirected to a fake one - with fake information about the store.
At the same time, the fraudster's server initiates a request to the legitimate 3-D Secure server with the original service message. For the bank, this looks as if the user personally transferred funds to the fraudster's card through the bank's P2P service. The bank sends the cardholder an SMS code to confirm the payment, which the user enters on the phishing 3-D Secure page. As a result, the SMS code received by the fraudster's server from the fake 3-D Secure page is used to request a request to the legitimate server to confirm the fraudulent payment.
"The scheme is really dangerous and is spreading and modifying extremely quickly," comments Pavel Krylov, head of Group-IB's online fraud prevention department. "We have repeatedly warned banks about the need to strengthen protection against the scheme with a fake 3-D Secure page, blocking the very possibility of fake merchants accessing the legitimate 3-D Secure server. As a rule, this is done using direct requests generated by fraudsters, or automatically, that is, by bots. At the moment, protection against this type of fraud is available in only a few of the largest banks in Russia and the CIS. It is based on behavioral analysis and the ability to track each session and user behavior both on the web resource and in the mobile application in real time, signaling the bank about any suspicious attempts to make payment transactions."
Group-IB experts predict that, most likely, as was the case with a number of other fraudulent schemes, “fake” payment systems will become widespread outside of Russia. The danger of the scheme is that transferring money to fraudsters’ accounts looks absolutely legal for banks.
Source

