Friend
Professional
- Messages
- 2,653
- Reaction score
- 850
- Points
- 113
Lone hackers increase their attacks by avoiding associations with large groups.
According to a report from Coveware, in the second quarter of 2024, the number of attacks without explicit reference to a specific brand of ransomware increased significantly. Usually, such attacks can be easily recognized by the type of cryptographer, a ransom note, or a site on the TOR network. However, in more than 10% of the investigated incidents, there were no such signs. This is due to the fact that some criminals prefer to act independently, the so-called "lone wolves".
Criminals are increasingly changing brands of ransomware or acting without reference to a specific brand in order to hide their identity. In the modern world of cyber extortion, criminals usually use one brand, but if hackers attack sensitive and large targets, such as hospitals or large companies, they try to minimize the risks. A high profile of the victim can draw attention to the group and increase the interest of law enforcement agencies.
When an entire brand of ransomware is eliminated, the number of attacks from independent groups increases dramatically. For example, after the collapse of the BlackCat/ALPHV and Lockbit groups, there was an increase in attacks from the BlackSuit, RansomHub, Medusa and other groups. The methods and procedures of attacks often coincided with those used by the liquidated brands, which indicates the transition of participants to new platforms.
Some criminals prefer to remain independent, but use the infrastructure of well-known brands. For example, they can rent a data leak site to threaten the victim, or use someone else's encryption engine. In the second quarter, members of the Scattered Spider group used the Qilin group encoder.
Such trends suggest that businesses should focus on attack methods rather than on ransomware brands. The security and media sectors often focus on "brands" to make stories more interesting, but this distracts from the more important aspects of attack methods.
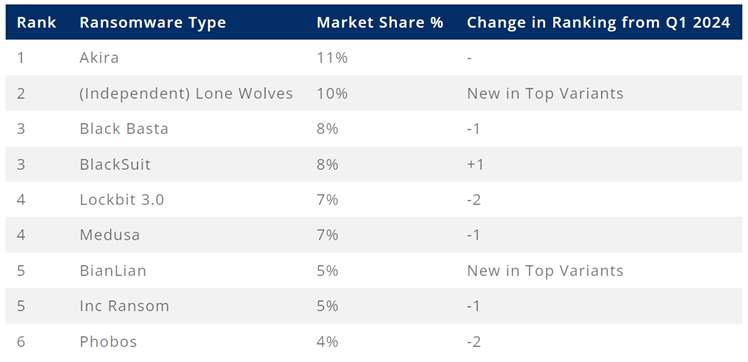
The most common variants of ransomware in the second quarter of 2023
In the second quarter of 2024, the average repurchase amount increased slightly to $391,015, while the median amount decreased to $170,000. The number of cases where companies chose to pay a ransom has also increased, especially in cases of data leaks.
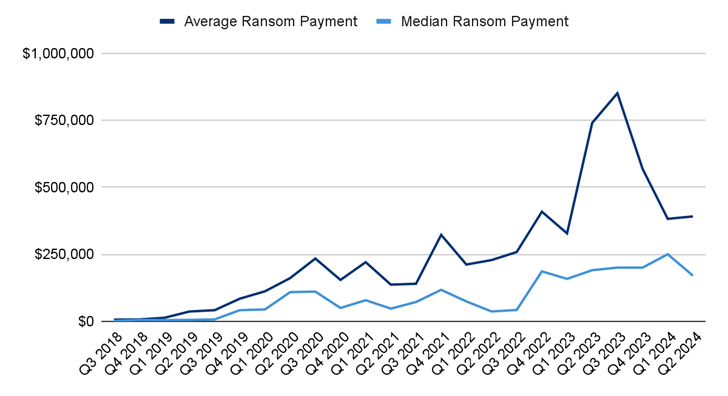
Schedule for changing payments to extortionists
Remote hacking and phishing remain the main attack vectors. Security Event management systems (SIEM) play an important role in helping you identify and isolate initial access more quickly.
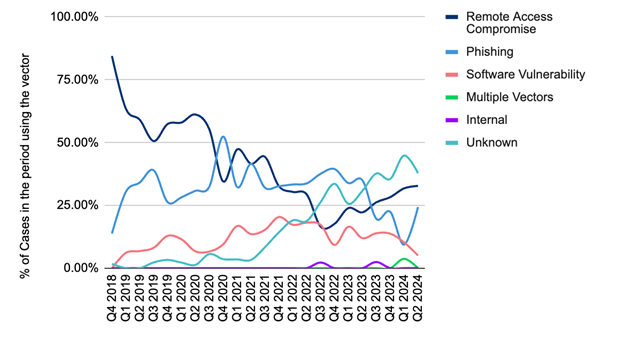
The most common attack vectors in the second quarter of 2024
The main tactics of criminals include data exfiltration, lateral movement in the network, and influencing the availability or integrity of business processes. Hackers use Megasync and Rclone to exfiltrate data, and actively move around the network using RDP and SSH.

Most common TTPs in the second quarter of 2024
Attacks continue in various industries, including healthcare, industry, and finance. Cyber extortion remains a problem for small and medium-sized businesses. Although large companies attract more media attention, the main victims are small and medium-sized businesses.
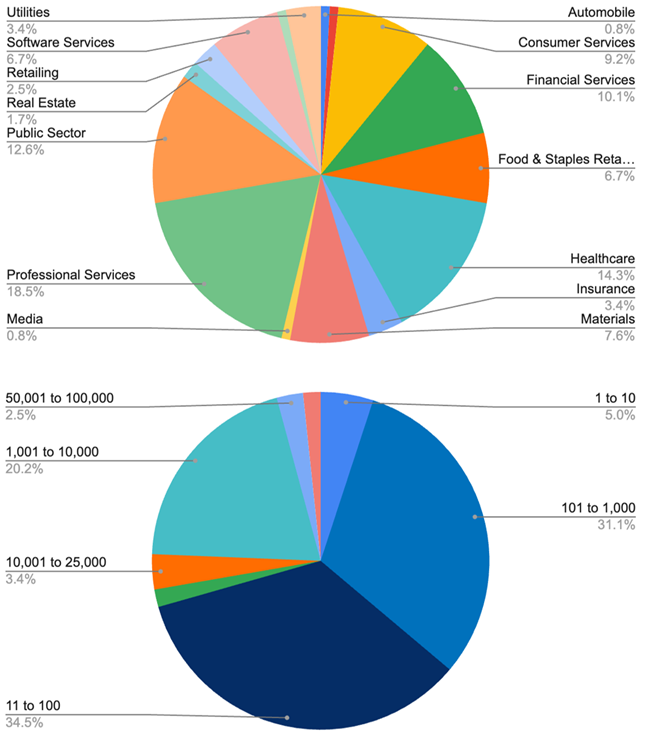
Industries and the number of companies affected by ransomware in the second half of 2024
Current trends show that organizations need to focus on protecting against repeated attack methods and improving cybersecurity measures to minimize the risks and consequences of such incidents.
Source
According to a report from Coveware, in the second quarter of 2024, the number of attacks without explicit reference to a specific brand of ransomware increased significantly. Usually, such attacks can be easily recognized by the type of cryptographer, a ransom note, or a site on the TOR network. However, in more than 10% of the investigated incidents, there were no such signs. This is due to the fact that some criminals prefer to act independently, the so-called "lone wolves".
Criminals are increasingly changing brands of ransomware or acting without reference to a specific brand in order to hide their identity. In the modern world of cyber extortion, criminals usually use one brand, but if hackers attack sensitive and large targets, such as hospitals or large companies, they try to minimize the risks. A high profile of the victim can draw attention to the group and increase the interest of law enforcement agencies.
When an entire brand of ransomware is eliminated, the number of attacks from independent groups increases dramatically. For example, after the collapse of the BlackCat/ALPHV and Lockbit groups, there was an increase in attacks from the BlackSuit, RansomHub, Medusa and other groups. The methods and procedures of attacks often coincided with those used by the liquidated brands, which indicates the transition of participants to new platforms.
Some criminals prefer to remain independent, but use the infrastructure of well-known brands. For example, they can rent a data leak site to threaten the victim, or use someone else's encryption engine. In the second quarter, members of the Scattered Spider group used the Qilin group encoder.
Such trends suggest that businesses should focus on attack methods rather than on ransomware brands. The security and media sectors often focus on "brands" to make stories more interesting, but this distracts from the more important aspects of attack methods.

The most common variants of ransomware in the second quarter of 2023
In the second quarter of 2024, the average repurchase amount increased slightly to $391,015, while the median amount decreased to $170,000. The number of cases where companies chose to pay a ransom has also increased, especially in cases of data leaks.

Schedule for changing payments to extortionists
Remote hacking and phishing remain the main attack vectors. Security Event management systems (SIEM) play an important role in helping you identify and isolate initial access more quickly.

The most common attack vectors in the second quarter of 2024
The main tactics of criminals include data exfiltration, lateral movement in the network, and influencing the availability or integrity of business processes. Hackers use Megasync and Rclone to exfiltrate data, and actively move around the network using RDP and SSH.

Most common TTPs in the second quarter of 2024
Attacks continue in various industries, including healthcare, industry, and finance. Cyber extortion remains a problem for small and medium-sized businesses. Although large companies attract more media attention, the main victims are small and medium-sized businesses.

Industries and the number of companies affected by ransomware in the second half of 2024
Current trends show that organizations need to focus on protecting against repeated attack methods and improving cybersecurity measures to minimize the risks and consequences of such incidents.
Source

