In December 2020, the value of Bitcoin reached a record $ 20,000, and interest in cryptocurrencies has once again increased, despite the fact that over the past month the rate has dropped significantly. So, many large exchangers and exchanges were forced to suspend the registration of new users, unable to cope with the influx of interested people, and video cards almost completely disappeared from the stores again, since mining can still be a very profitable occupation.
Cryptocurrencies are not ignored by criminals either. So, in recent months, the number of mining malware has increased significantly, and the phenomenon of the so-called "browser mining" (aka cryptojacking) has also emerged - site visitors are forced to mine cryptocurrency without their knowledge. But this week it became known that operators of large botnets are now interested in cryptocurrency.
Satori
Qihoo 360 Netlab specialists discovered that on January 8, 2021, a new botnet appeared on the network landscape - a modification of the Satori botnet already known to experts. Researchers are confident that the same author created a new variation of malware, previously intended exclusively for hacking IoT devices, since the malware code is similar.Let me remind you that the original Satori botnet was spotted in early December 2020. The Satori malware, on which the botnet of the same name is being built, was another variation of the acclaimed IoT malware Mirai. At the time, Qihoo 360 Netlab analysts warned about 280,000 active bots and that the threat was using tactics different from Mirai. The fact is that the classic version of Mirai works like a Telnet scanner, while using long lists of usernames and passwords suitable for various “smart” devices that the malware brute-forces. But Satori was armed with two exploits, which he used instead of brute force.
Now Qihoo 360 Netlab researchers have discovered a modification of Satori.Coin.Robber , which, as the name implies, is designed to steal cryptocurrency. If the first botnet, as experts assume, was created by a novice hacker or script kiddie, then he is definitely learning. The new version of the malware is designed not only for attacks on IoT devices (the malware still uses the same exploits), but also on devices for mining Ethereum cryptocurrency.
Satori.Coin.Robber scans port 3333 and looks for Claymore Miner mining software in order to then replace the miner's wallet address with your own. So far, the researchers have not published practically any information about the exploit itself, which the malware uses, as they are afraid to aggravate the situation. We only know that an attacker can interact with the device and replace data without proper authentication. So, Satori.Coin.Robber changes the miner's configuration by adding a new pool (eth-us2.dwarfpool.com:8008) and a new wallet (0xB15A5332eB7cD2DD7a4Ec7f96749E769A371572d). Currently, according to the pool statistics, the malware operator has earned more than 2 ETH (more than 2000 at the current exchange rate).
Moreover, the author of the malware leaves a message with the following content, in case the owner of the miner discovers a hack:
“This is the developer of Satori. Don't worry about this bot as long as it doesn't have any malicious functionality, so go ahead and ignore it. You can reach me at [email protected]. "
Necurs
Operators of one of the largest botnets in the world, Necurs, with over 6 million infected hosts, are also interested in cryptocurrency. Let me remind you that earlier Necurs was mainly engaged in sending malicious spam, for example, at the end of November 2017, the botnet began distributing the Scarab ransomware at a rate of 12.5 million spam letters in a few hours. But the main malware distributed by Necurs is the well-known Dridex banker.Now the journalists of Bleeping Computer, together with information security specialist and the author of the blog MyOnlineSecurity, who is known simply as Derek, have discovered that Necurs is being used to manipulate cryptocurrency rates.
It should be said that this is not the first experience of this kind for botnet owners. Previously, Necurs operators have already tried to manipulate the securities market. Back then, spammers' messages were based on the classic pump-and-dump scheme in this area. This illegal practice is used to artificially raise the price of stocks by misleading users in order to sell cheap stocks at a higher price. Earlier, cybercriminals massively misinformed users, reporting, according to a certain Manhattan firm, that soon InCapta Inc ($ INCT), which develops mobile applications, will be acquired at a price of $ 1.37 per share by DJI, which produces drones. The cybercriminals recommended buying up InCapta Inc shares before it was too late, and promised that these investments would bring big profits.
Botnet operators are now using the same tactic, again implementing a pump-and-dump scheme, only this time to “promote” the Swisscoin (SIC) cryptocurrency. Moreover, this altcoin last year was named a network marketing from a cryptocurrency that implements the so-called "Ponzi scheme", after which its circulation was suspended. However, trading resumed on January 15, 2021, and the attackers hastened to take advantage of this.
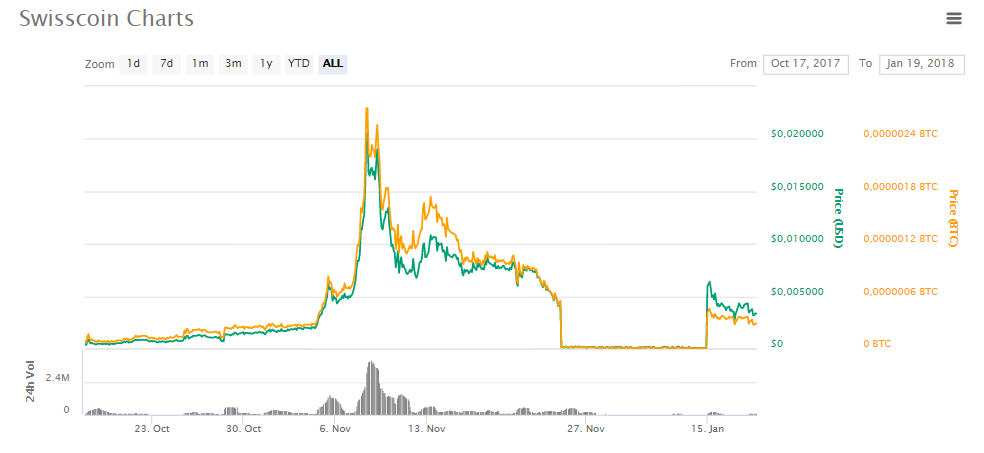
The spam now being sent out by Necurs promises that the value of Swisscoin could increase by 50,000 percent this year, and an investment of $ 1,000 would eventually bring the investor a million.
Unfortunately, it is still difficult to judge exactly how the actions of the Necurs operators affect the cost of Swisscoin, since on January 16-17, 2018, the entire cryptocurrency market significantly "sagged", the Bitcoin price dropped to $ 9000, and the cost of altcoins also changed almost unpredictably (mainly towards a sharp decrease).
Attacks on web servers
However, botnets are far from the only problem today. It has long been clear that criminals have realized how profitable it can be to infect various servers with mining malware, where malware is not immediately detected, and their power, as a rule, significantly exceeds ordinary user devices.
Another proof of this was the detection of the RubyMiner malware, which was warned about by Check Point and Certego specialists. According to researchers, the malware massively attacks vulnerable web servers in the UK, Germany, USA, Norway and Sweden, and managed to infect more than 700 machines in the first day.

Windows and Linux servers vulnerable to various bugs were under threat. Exploiting various vulnerabilities discovered in PHP, Microsoft IIS and Ruby on Rails back in 2012-2013, criminals install an XMRig miner on servers to “mine” the Monero cryptocurrency. According to experts, the criminals are not particularly trying to hide their actions; rather, the attack is aimed at compromising as many devices as possible in the shortest possible time.
Given that attackers have targeted servers that are vulnerable to five-year-old problems, it can be expected that these machines have long been "abandoned", and there will be simply no one to discover the hidden manner.
