Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,175
- Points
- 113
North Korea is infiltrating the systems of key industries.
360 Advanced Threat Research Institute specialists have discovered a new campaign of the North Korean group Lazarus (APT-C-26), during which malicious PyPI packages are distributed.
Lazarus continues its active activities aimed at cyber attacks in various industries. This time, hackers targeted not only financial institutions and crypto exchanges, but also government organizations, the aerospace industry and military structures around the world. The main purpose of attacks is to gain financial benefits and steal confidential information.
Malicious packages are uploaded to PyPI under the guise of legitimate libraries. Packages do not arouse suspicion among developers who may accidentally install them in their projects. Infected packages are designed for various operating systems and are used to launch multi-level attacks.
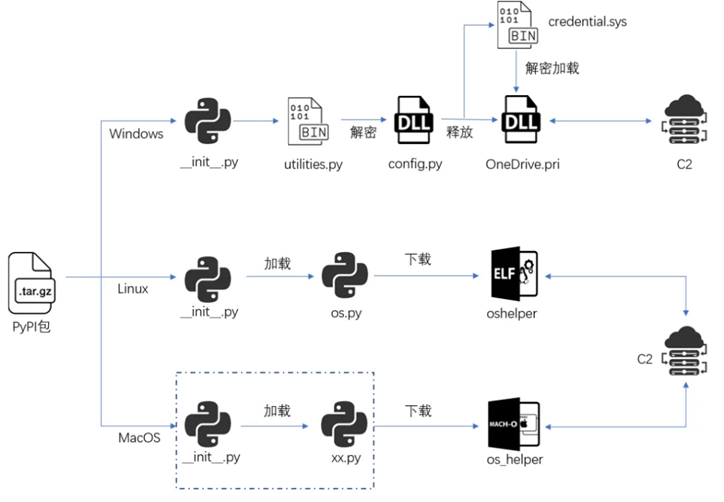
Lazarus infection chain
Using one of the packages as an example, you can see exactly how the malicious mechanism works. When installing a package under certain conditions, the file is executed init.py, which decodes malicious code and saves it as a DLL file. The DLL is then run using the rundll32 command, which allows attackers to execute malicious commands.
For Windows, the malicious package contains an encrypted payload that is gradually decrypted and loaded into memory, leaving no trace on disk. On Linux, the malicious package downloads an ELF file with a full set of remote management functions. In macOS, the malicious code is similar to the Linux version. This suggests that the attack process is similar.
According to the analysis, one of the detected files (config.py) contains malicious code that is used to further spread attacks. config.py downloads and decrypts new DLLs, placing them in system directories, including OneDrive. The files are then executed through the task scheduler, registry settings, or startup directories.
Components of the attack include encrypting data and using special keys to decrypt it. For example, the file credential.sys it is decrypted twice before the new "Comebacker" DLL is loaded and executed, which then downloads and runs the malicious code of the next stage.
For Linux, malicious packages use a similar distribution method. When installing the package, code is run that downloads malware from a remote server. In macOS, malicious files also use similar methods and have similar functions to the Linux versions.
The attacks demonstrate a high level of training and organization typical of Lazarus. The use of complex encryption methods and multi-level attacks, as well as the ability to attack multiple operating systems simultaneously, makes the group one of the most dangerous today. Organizations and individuals should be especially vigilant and take measures to protect their systems from such threats.
Source
360 Advanced Threat Research Institute specialists have discovered a new campaign of the North Korean group Lazarus (APT-C-26), during which malicious PyPI packages are distributed.
Lazarus continues its active activities aimed at cyber attacks in various industries. This time, hackers targeted not only financial institutions and crypto exchanges, but also government organizations, the aerospace industry and military structures around the world. The main purpose of attacks is to gain financial benefits and steal confidential information.
Malicious packages are uploaded to PyPI under the guise of legitimate libraries. Packages do not arouse suspicion among developers who may accidentally install them in their projects. Infected packages are designed for various operating systems and are used to launch multi-level attacks.

Lazarus infection chain
Using one of the packages as an example, you can see exactly how the malicious mechanism works. When installing a package under certain conditions, the file is executed init.py, which decodes malicious code and saves it as a DLL file. The DLL is then run using the rundll32 command, which allows attackers to execute malicious commands.
For Windows, the malicious package contains an encrypted payload that is gradually decrypted and loaded into memory, leaving no trace on disk. On Linux, the malicious package downloads an ELF file with a full set of remote management functions. In macOS, the malicious code is similar to the Linux version. This suggests that the attack process is similar.
According to the analysis, one of the detected files (config.py) contains malicious code that is used to further spread attacks. config.py downloads and decrypts new DLLs, placing them in system directories, including OneDrive. The files are then executed through the task scheduler, registry settings, or startup directories.
Components of the attack include encrypting data and using special keys to decrypt it. For example, the file credential.sys it is decrypted twice before the new "Comebacker" DLL is loaded and executed, which then downloads and runs the malicious code of the next stage.
For Linux, malicious packages use a similar distribution method. When installing the package, code is run that downloads malware from a remote server. In macOS, malicious files also use similar methods and have similar functions to the Linux versions.
The attacks demonstrate a high level of training and organization typical of Lazarus. The use of complex encryption methods and multi-level attacks, as well as the ability to attack multiple operating systems simultaneously, makes the group one of the most dangerous today. Organizations and individuals should be especially vigilant and take measures to protect their systems from such threats.
Source
