Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
Due to the shortcomings of the technology, your files are not only visible to the recipient.
Eurecom Research Center has discovered vulnerabilities in Bluetooth that can compromise the privacy of Bluetooth sessions, allowing hackers to conduct attacks on devices and create conditions for Man-in-the-Middle (MitM) attacks. A series of exploits is called BLUFFS (Bluetooth Forward and Future Secrecy Attacks and Defenses).
The vulnerabilities are related to two new flaws in the Bluetooth standard related to the process of creating session keys for data decryption. It is important to note that the issues are architectural and affect Bluetooth at the most basic level, not dependent on specific hardware or software.
The problems are tracked under the identifier CVE-2023-24023 and affect the basic Bluetooth specification from 4.2 to 5.4, which puts billions of devices at risk, including smartphones, laptops and other mobile devices.
Mechanism of action of BLUFFS
BLUFFS is a series of exploits aimed at violating the privacy of both current and future Bluetooth sessions. Attacks achieve their goal by exploiting four vulnerabilities in the process of obtaining a session key. Two of them allow you to get a short, easily predictable Session Key (SKC), with which an attacker can decrypt previous and future communications.
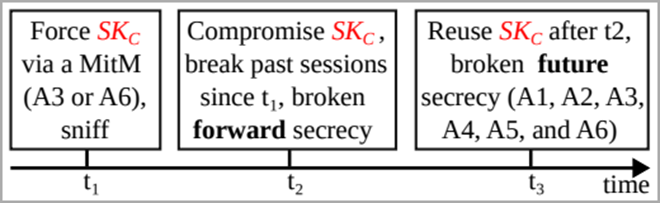
BLUFFS Attack Chain
To carry out an attack, a cybercriminal must be within Bluetooth range of two targets that exchange data, and impersonate one of them to negotiate a weak session key with the other, offering the lowest possible key entropy value and using a permanent session key diversifier.
The published article presents six types of BLUFFS attacks, covering various combinations of device imitation and MitM attacks that work regardless of whether the victims support Secure Connections (SC) or Legacy Secure Connections (LSC).
Exposure and precautions
Eurecom researchers tested BLUFFS on a variety of devices, including smartphones, headphones, and laptops that use Bluetooth versions 4.1 through 5.2.The authors found that all devices are susceptible to at least 3 out of 6 types of BLUFFS attacks. Experts have developed and posted on GitHub a set of tools that demonstrate the effectiveness of BLUFFS.
In response to the threat, the researchers proposed a number of improvements:
Bluetooth SIG, the organization responsible for developing Bluetooth standards, took note of the study's results and recommended rejecting connections with low cryptographic key protection, as well as using modes that provide a higher level of encryption.
Eurecom Research Center has discovered vulnerabilities in Bluetooth that can compromise the privacy of Bluetooth sessions, allowing hackers to conduct attacks on devices and create conditions for Man-in-the-Middle (MitM) attacks. A series of exploits is called BLUFFS (Bluetooth Forward and Future Secrecy Attacks and Defenses).
The vulnerabilities are related to two new flaws in the Bluetooth standard related to the process of creating session keys for data decryption. It is important to note that the issues are architectural and affect Bluetooth at the most basic level, not dependent on specific hardware or software.
The problems are tracked under the identifier CVE-2023-24023 and affect the basic Bluetooth specification from 4.2 to 5.4, which puts billions of devices at risk, including smartphones, laptops and other mobile devices.
Mechanism of action of BLUFFS
BLUFFS is a series of exploits aimed at violating the privacy of both current and future Bluetooth sessions. Attacks achieve their goal by exploiting four vulnerabilities in the process of obtaining a session key. Two of them allow you to get a short, easily predictable Session Key (SKC), with which an attacker can decrypt previous and future communications.

BLUFFS Attack Chain
To carry out an attack, a cybercriminal must be within Bluetooth range of two targets that exchange data, and impersonate one of them to negotiate a weak session key with the other, offering the lowest possible key entropy value and using a permanent session key diversifier.
The published article presents six types of BLUFFS attacks, covering various combinations of device imitation and MitM attacks that work regardless of whether the victims support Secure Connections (SC) or Legacy Secure Connections (LSC).
Exposure and precautions
Eurecom researchers tested BLUFFS on a variety of devices, including smartphones, headphones, and laptops that use Bluetooth versions 4.1 through 5.2.The authors found that all devices are susceptible to at least 3 out of 6 types of BLUFFS attacks. Experts have developed and posted on GitHub a set of tools that demonstrate the effectiveness of BLUFFS.
In response to the threat, the researchers proposed a number of improvements:
- Implementation of the Key Derivation Function (KDF) for LSC connections, which includes mutual exchange of one-time keys and their verification;
- Devices must use a shared pairing key for mutual authentication of key diversifiers, ensuring the legitimacy of session participants;
- Enable Secure Connections (SC) mode where possible;
- Maintain a cache of session key diversifiers to prevent their reuse.
Bluetooth SIG, the organization responsible for developing Bluetooth standards, took note of the study's results and recommended rejecting connections with low cryptographic key protection, as well as using modes that provide a higher level of encryption.

