Ande Loader is at the forefront of a malicious campaign aimed at spreading Trojan software.
A cybercrime group known as Blind Eagle has stepped up its attacks on users who speak Spanish and work in the manufacturing industry in North America.
Hackers use a new type of loader called Ande Loader to distribute malicious software. The purpose of these attacks is to deliver Remote access Trojans (RAT), including well-known instances such as Remcos and njRAT.
According to the Canadian information security company eSentire, cybercriminals use the method of phishing emails containing RAR and BZ2 archives, which is the key to activating the malicious chain. Password-protected archives contain a Visual Basic Script (VBScript) file, which ensures that malware remains persistent on the target system and runs Ande Loader. The loader, in turn, activates the Remcos RAT trojan.
In an alternative version of the attack recorded by experts, attackers use a Discord link to distribute the BZ2 archive, which launches Ande Loader to deliver njRAT instead of Remcos RAT.
eSentire notes that the Blind Eagle group uses special cryptographers (crypters) to mask malicious components written by hackers under the pseudonyms Roda and Pjoao1578. Among such cryptographers, researchers note the FuckCrypt and UpCry programs.
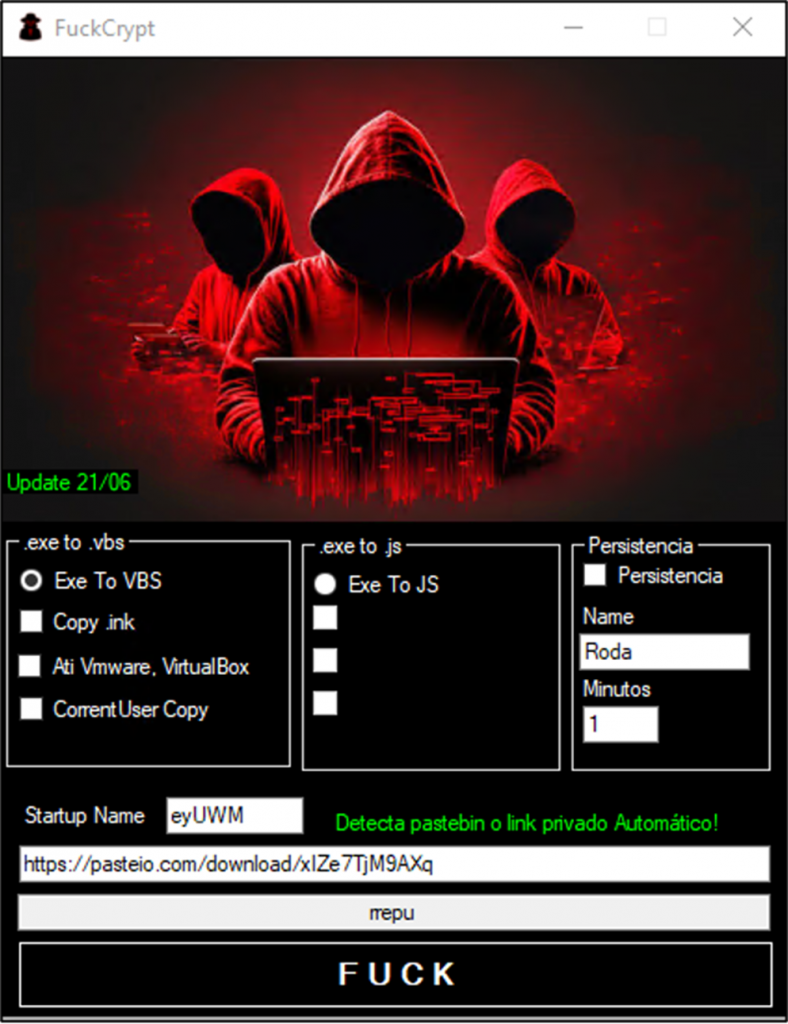
Crypter for bypassing security systems
Thus, the Blind Eagle group demonstrated the expansion of its attack geography and improved methods of delivering malicious programs aimed at industrial enterprises, actively using sophisticated methods to circumvent security mechanisms.
To avoid such attacks, companies need to implement multi-level security tools, including advanced solutions for monitoring endpoints, network traffic, and cloud activity.
In addition, it is extremely important to regularly train employees in cybersecurity to resist social engineering and phishing attacks, which are often the starting point of an intrusion.
Only a comprehensive approach to cybersecurity, combining security tools, monitoring and awareness-raising, can ensure that enterprises are resilient to modern cyber threats.
A cybercrime group known as Blind Eagle has stepped up its attacks on users who speak Spanish and work in the manufacturing industry in North America.
Hackers use a new type of loader called Ande Loader to distribute malicious software. The purpose of these attacks is to deliver Remote access Trojans (RAT), including well-known instances such as Remcos and njRAT.
According to the Canadian information security company eSentire, cybercriminals use the method of phishing emails containing RAR and BZ2 archives, which is the key to activating the malicious chain. Password-protected archives contain a Visual Basic Script (VBScript) file, which ensures that malware remains persistent on the target system and runs Ande Loader. The loader, in turn, activates the Remcos RAT trojan.
In an alternative version of the attack recorded by experts, attackers use a Discord link to distribute the BZ2 archive, which launches Ande Loader to deliver njRAT instead of Remcos RAT.
eSentire notes that the Blind Eagle group uses special cryptographers (crypters) to mask malicious components written by hackers under the pseudonyms Roda and Pjoao1578. Among such cryptographers, researchers note the FuckCrypt and UpCry programs.

Crypter for bypassing security systems
Thus, the Blind Eagle group demonstrated the expansion of its attack geography and improved methods of delivering malicious programs aimed at industrial enterprises, actively using sophisticated methods to circumvent security mechanisms.
To avoid such attacks, companies need to implement multi-level security tools, including advanced solutions for monitoring endpoints, network traffic, and cloud activity.
In addition, it is extremely important to regularly train employees in cybersecurity to resist social engineering and phishing attacks, which are often the starting point of an intrusion.
Only a comprehensive approach to cybersecurity, combining security tools, monitoring and awareness-raising, can ensure that enterprises are resilient to modern cyber threats.
